
Black Basta ransomware exploits Windows Error Reporting Service vulnerability
Researchers have found an exploit tool using an elevation of privilege vulnerability to drop Black Basta ransomware.
The US Cybersecurity and Infrastructure Security Agency (CISA) has added a vulnerability in the Windows Error Reporting Service to its catalog of known exploited vulnerabilities, based on evidence of active exploitation. This means that Federal Civilian Executive Branch (FCEB) agencies need to remediate this vulnerability by July 4, 2024, to protect their networks against active threats.
The vulnerability in question is listed as CVE-2024-26169, a Windows Error Reporting Service Elevation of Privilege (EoP) vulnerability. A patch for this vulnerability was included in the March 2024 patch Tuesday round of updates.
Reportedly, the vulnerability is under active exploitation by the Black Basta ransomware group. Researchers have found an exploit tool that uses the fact that the Windows file werkernel.sys uses a null security descriptor when creating registry keys to start a shell with administrative privileges.
The null security descriptor means that the Windows Error Reporting Service created registry keys without setting up security checks. As a result, any created subkeys could be controlled by the user currently running the process. The exploit uses this flaw to create a specific registry key and change a setting so it can run its own program instead of a normal Windows program.
The tool creates a subkey of the registry key HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options to pull this off. Image File Execution Options (IFEO) are used for debugging. Malware, as we know, does not only check if there are debuggers active, but it’s also known to use IFEO’s features to their own advantage.
A search for similar tools on VirusTotal indicated that the vulnerability was in use before it was patched as a zero-day vulnerability.
Black Basta is a Ransomware-as-a-Service operator, and its affiliates are known to deploy several methods to gain initial access, including tech support scams, as we reported last month.
The group has become more active recently, reporting more attacks in the previous three months than at any other time in the last two years.
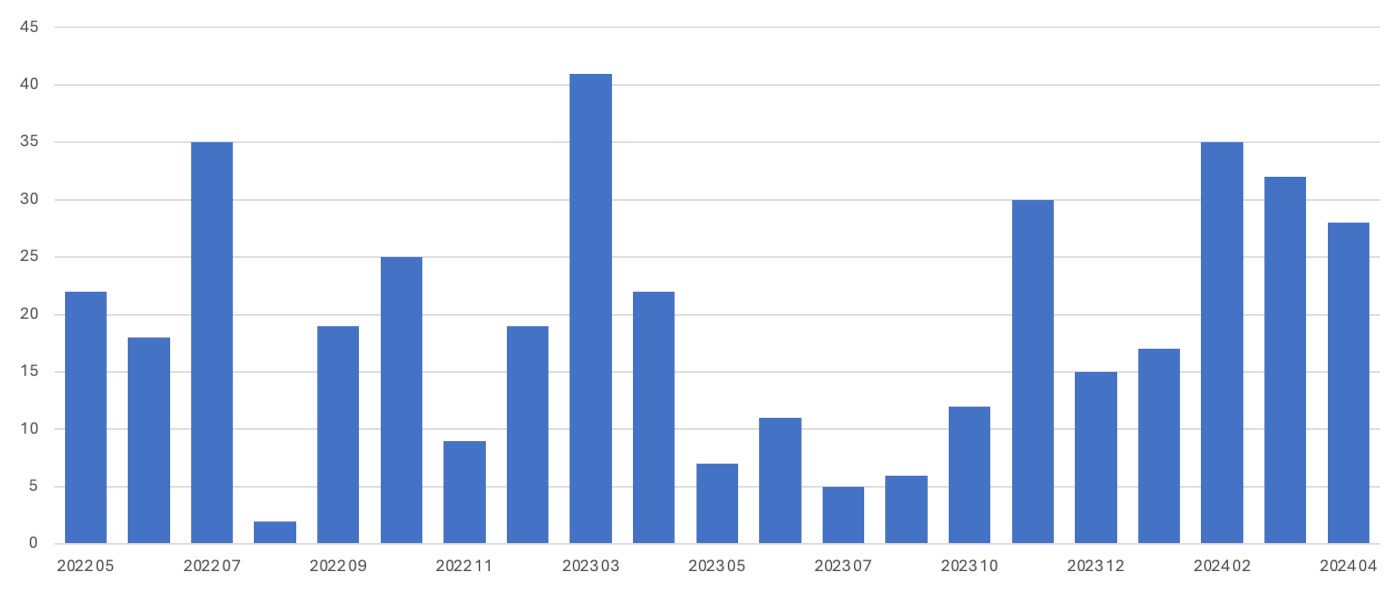
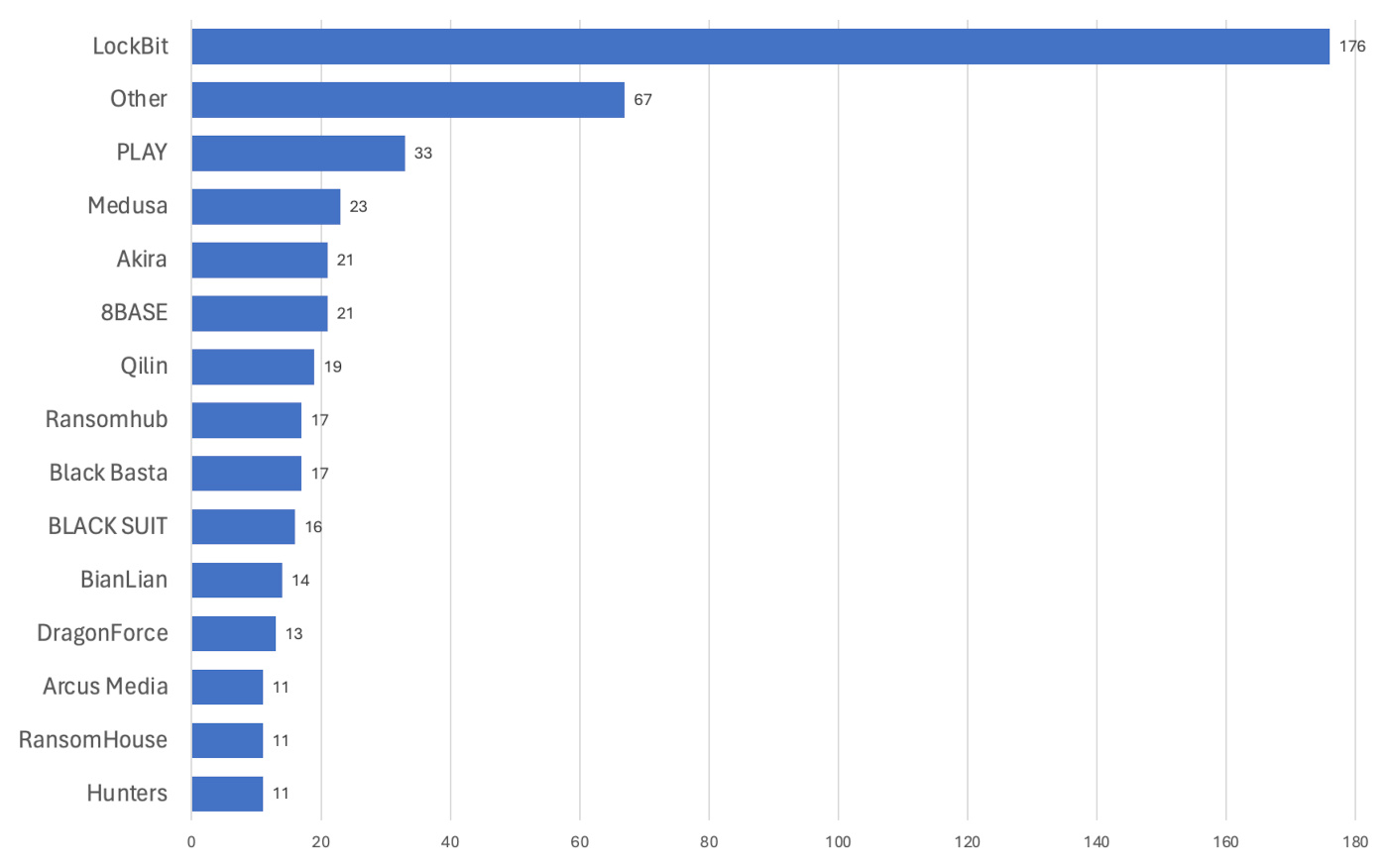
Black Basta is regularly one of the ten most active ransomware groups. In our latest monthly ransomware review it was ranked eighth, making it a globally significant threat actor.
Not too long ago, the Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency (CISA), Department of Health and Human Services (HHS), and Multi-State Information Sharing and Analysis Center (MS-ISAC), released a joint Cybersecurity Advisory (CSA) about Black Basta. The advisory provides a lot of Indicators of Compromise (IOCs) and Tactics and Techniques related to Black Basta and is worth a read.
How to avoid ransomware
- Block common forms of entry. Create a plan for patching vulnerabilities in internet-facing systems quickly; and disable or harden remote access like RDP and VPNs.
- Prevent intrusions. Stop threats early before they can even infiltrate or infect your endpoints. Use endpoint security software that can prevent exploits and malware used to deliver ransomware.
- Detect intrusions. Make it harder for intruders to operate inside your organization by segmenting networks and assigning access rights prudently. Use EDR or MDR to detect unusual activity before an attack occurs.
- Stop malicious encryption. Deploy Endpoint Detection and Response software like ThreatDown EDR that uses multiple different detection techniques to identify ransomware, and ransomware rollback to restore damaged system files.
- Create offsite, offline backups. Keep backups offsite and offline, beyond the reach of attackers. Test them regularly to make sure you can restore essential business functions swiftly.
- Don’t get attacked twice. Once you’ve isolated the outbreak and stopped the first attack, you must remove every trace of the attackers, their malware, their tools, and their methods of entry, to avoid being attacked again.




