
5 early signs of a ransomware attack (based on real examples)
Spot the five early signs of ransomware gangs moving laterally through your network.
Detecting a ransomware attack early is one of the best ways to prevent an encryption event—but sometimes, that’s easier said than done.
Why? Because ransomware gangs are sneaky, using Living off the Land (LOTL) techniques to avoid detection in the early stages of their attacks, where they seek to move laterally. The result is that by the time an organization realizes it’s being attacked, it’s often too late: There are backdoors into the network, data has already been stolen, and encryption may have started.
By being aware of the most common early signs of a ransomware attack, however, organizations can better spot and block ransomware gangs moving laterally through their network.
The ThreatDown Malware Removal Specialist (MRS) team, who handle hundreds of real ransomware cases a year, has consistently observed several early indicators of a ransomware attack for you to be aware of. Let’s dive into five of them.
1. Out of place IT admin tools
The detection of IT admin tools on an endpoint can be an early indicator of a ransomware attack. Attackers use these tools to gain control over systems and perform various malicious activities such as data exfiltration.
Recognizing IT admin tools and determining how recently they were created or installed on an endpoint is crucial. Tools such as Remote Monitoring and Management (RMM) software, PsExec, Wireshark, and Advanced IP Scanner, if found unexpectedly, can signify an impending ransomware attack.
For example, the ThreatDown MRS team recently discovered attackers using AnyDesk remote management software to establish a Command and Control (C&C) server on a company network. The attacker infiltrated the environment by exploiting an unpatched server with open ports exposed to the internet. AnyDesk was installed by the threat actor afterward. Such activity is typical of what our Threat Intel teams observe just before the widespread encryption carried out in ransomware attacks.
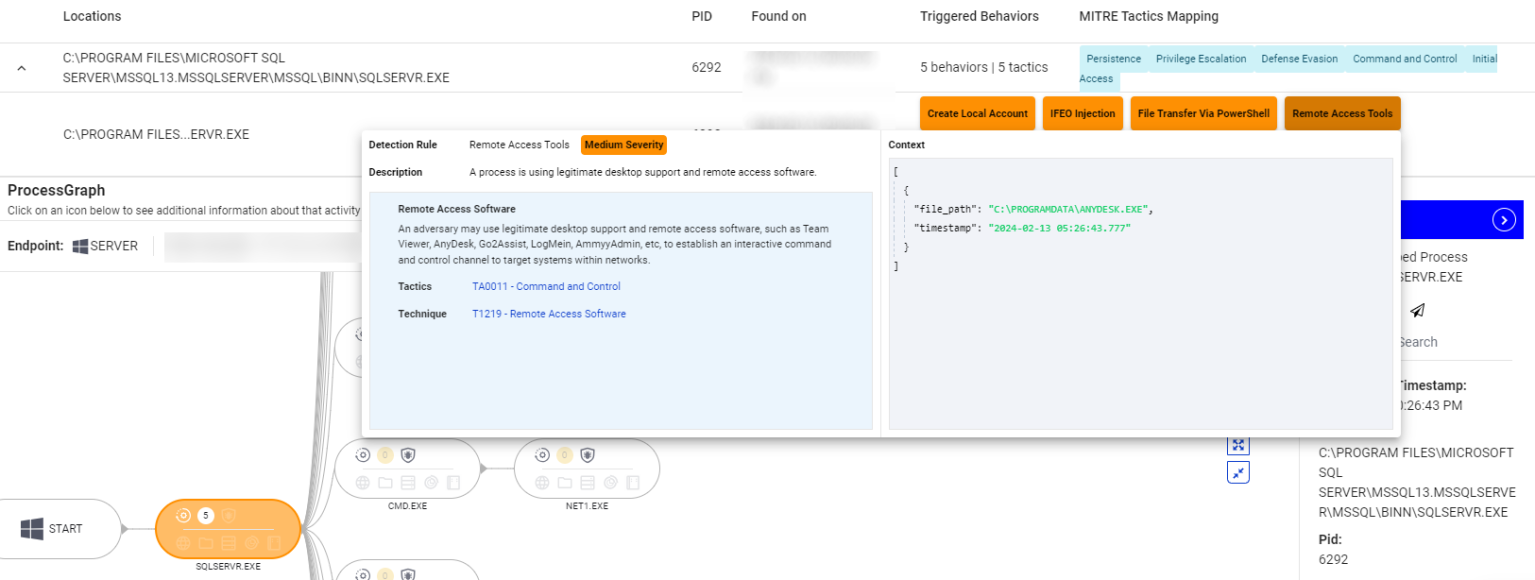
2. Credential dumping
Credential dumping involves extracting account login credentials from a compromised system. Attackers use these credentials to move laterally within a network and escalate privileges.
Monitoring for unusual access patterns or the presence of tools like Mimikatz, which is commonly used for credential dumping, can help identify a ransomware attack in the early stages. Any unexpected or unauthorized attempt to access stored credentials should be investigated immediately.
For example, ThreatDown recently observed an attack where threat actors used CMD.EXE to run credential dumping tools and scripts that would enable them to escalate privileges and move laterally within the target’s network.

3. Reconnaissance commands
Reconnaissance commands are used by attackers to gather information about a network and its users. EDR systems, such as ThreatDown EDR, often alert on reconnaissance-type commands such as nltest, net user, and net group. While these commands can be benign, their context is critical—making them a perfect example of a LOTL technique.
Internal IT administrators must verify if they recognize the commands run for the user account on the endpoint, the time they were executed, and whether they align with regular administrative activities.
For example, ThreatDown was able to stop a ransomware attack in its early stages recently after following up an EDR alert for NLTEST.EXE, which attackers had used in an attempt to gather information about critical network resources and escalate their attack by moving laterally within the network.
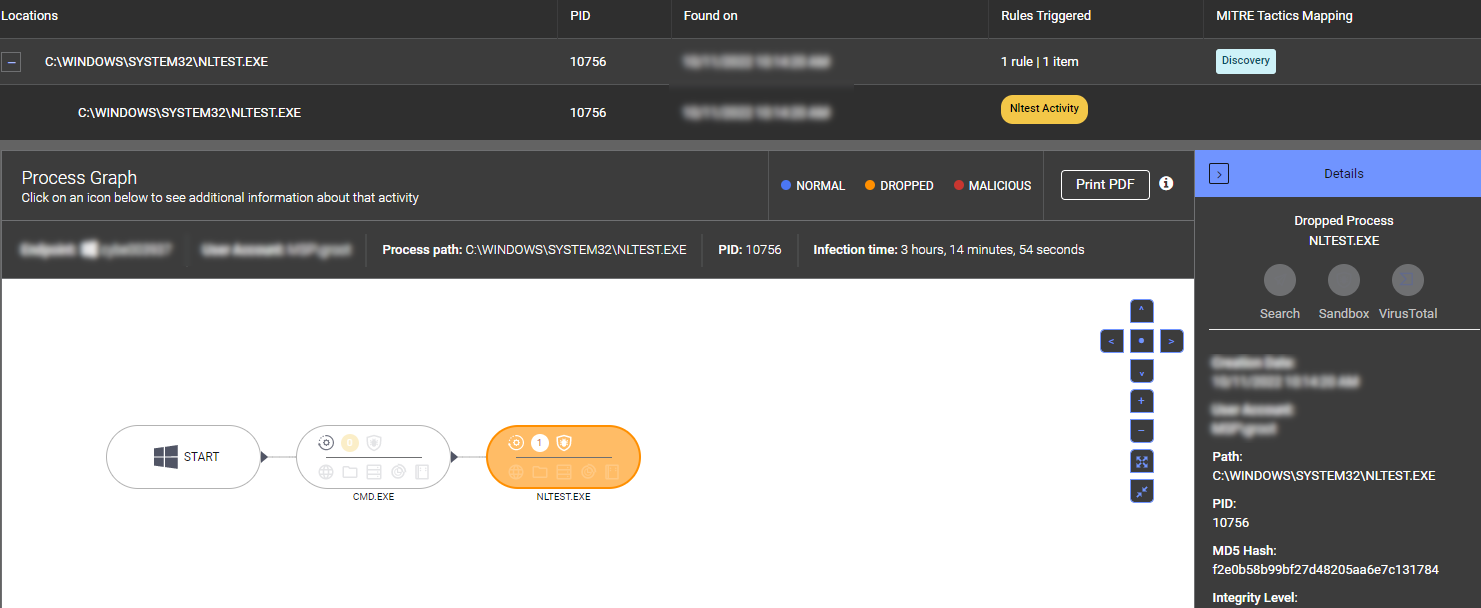
NLTEST.EXE.4. Presence or execution of common hacking tools
The presence or attempted execution of hacking tools can be a clear sign of an ongoing attack.
Tools like ProcessHacker, IOBit Uninstaller, and GMER are often used by attackers to disable security measures and gain deeper control over a system. Detecting these tools, especially if they are not part of the standard IT toolkit, should trigger an immediate investigation and response.
In a recent case, ThreatDown detected and quarantined ProcessHacker, Mimikatz, and LaZagne as ransomware attackers attempted to use them to escalate their privileges, dump credentials, and gather sensitive information.
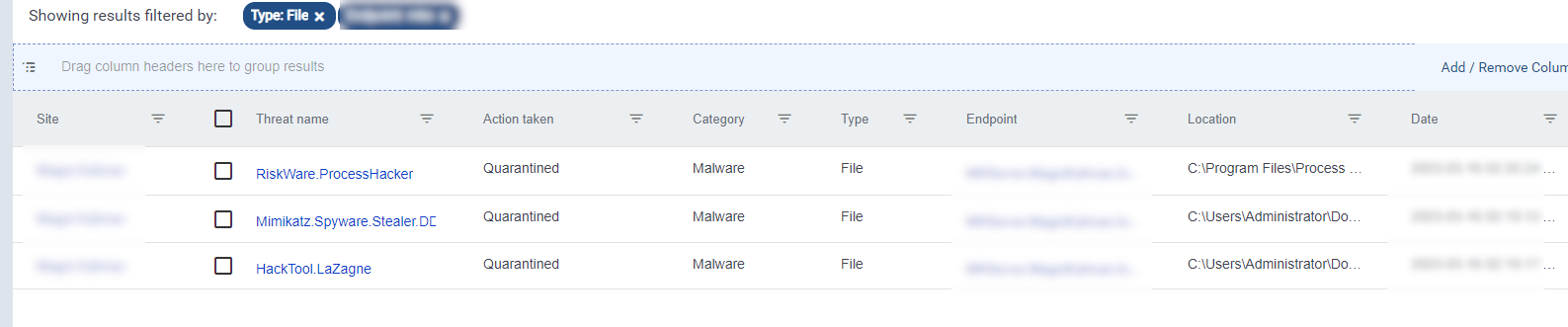
5. Brute force intrusion detections
Brute force attacks involve repeatedly attempting to gain access to a system by guessing passwords.
Detection systems that log multiple failed login attempts, especially within a short time frame, can signal a brute force attack. Such intrusion attempts can be a precursor to a ransomware attack, as attackers seek to gain initial access before deploying a malicious payload.
Monitoring for and responding to brute force intrusion detections can prevent attackers from establishing a foothold in a network.
In a recent attack, ThreatDown observed over 20,000 RDP brute force intrusion detections for various servers, indicating a significant and persistent attempt to gain unauthorized access to the target’s network.
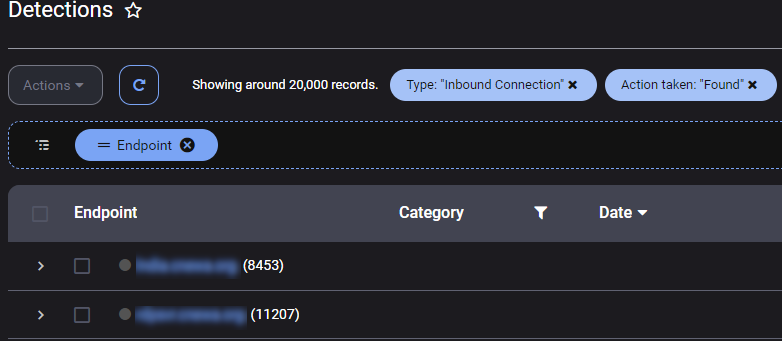
Early ransomware attacks and Managed Detection and Response (MDR)
Ransomware groups know that their attacks can be spotted by trained eyes, and experienced gangs will take care to work when you aren’t around. Spotting ransomware attacks early requires constant monitoring of network traffic, reviewing logs, and sifting through EDR suspicious activity alerts looking for anomalies on a round-the-clock basis, which can be difficult for small and medium-sized organizations to maintain.
ThreatDown MDR analysts are experienced in detecting threats early and blocking ransomware attackers before it’s too late. Read more on how the ThreatDown MDR team successfully stopped a Medusa ransomware attack here.




