
Anything but science fiction: The anatomy of an Akira ransomware attack
An analysis of a real life Akira ransomware attack.
Since we first observed it in April 2023, the Akira ransomware gang has made a big name for itself in a short time. With 244 confirmed attacks from April 2023 to March 2024, Akira has already become the eighth most prolific ransomware group since we began tracking all gangs in February 2022.
Akira made headlines in April after the Cybersecurity and Infrastructure Security Agency (CISA) FBI announced that the gang made $42 million from 250 attacks since March 2023, or an average of $3,500,000 a month. The CISA report also details Akira’s’ Tools, Tactics, and Procedures (TTPs).
Recently, a ThreatDown MDR client suffered an Akira ransomware attack. The incident involved sophisticated infiltration tactics, resulting in significant data encryption and operational disruption; however, the ThreatDown MDR team swiftly intervened to help the client recover from the attack. Let’s dive into the details.
Initial detection
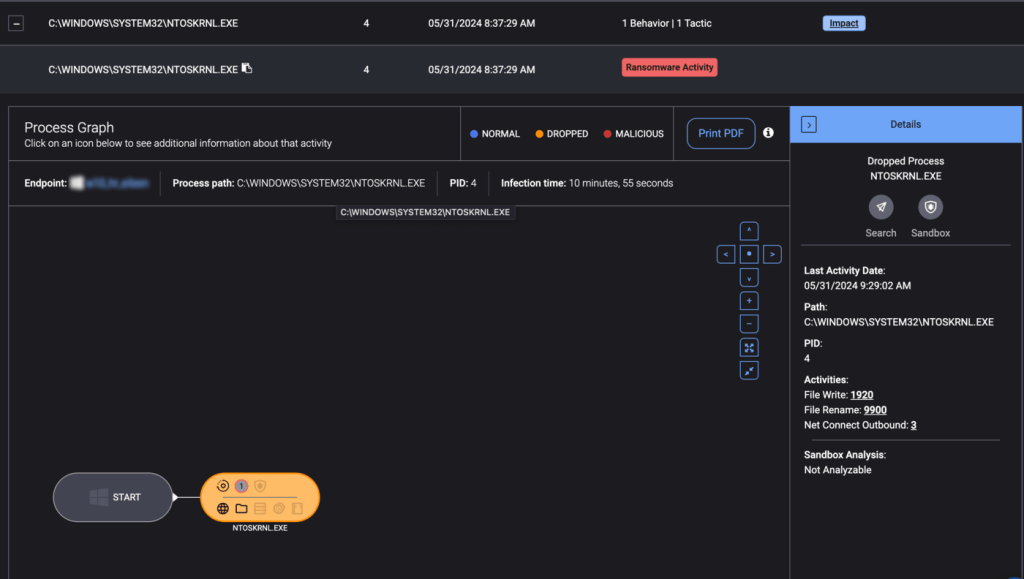
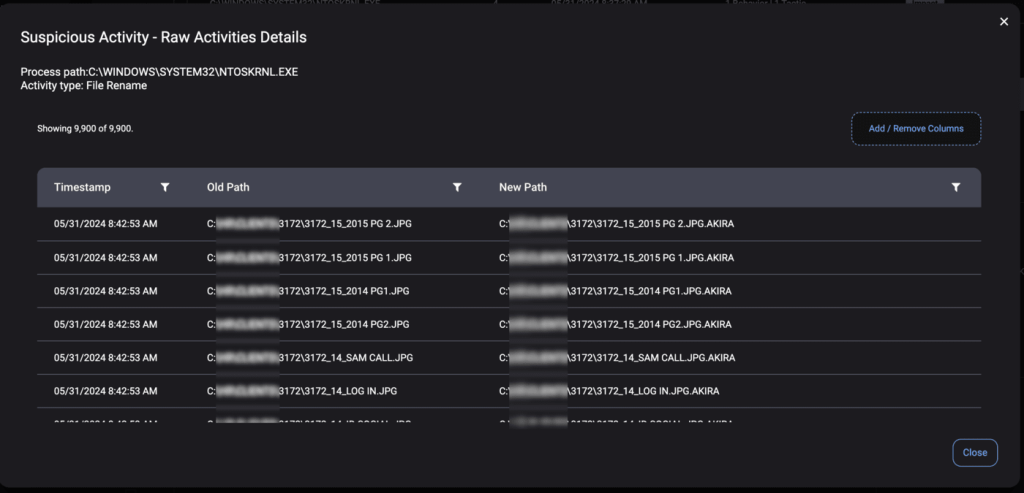
The ThreatDown MDR team first received an alert indicating suspicious ransomware activity originating from the NTOSKRNL.EXE process. The alert highlighted that thousands of files were renamed with the .akira file extension, signaling a ransomware attack.
Timeline of events:
- 05/31/2024, 9:37:29 AM – [Endpoint 1]: The first endpoint is encrypted with the
.akiraextension. - 05/31/2024, 9:48:21 AM – [Endpoint 2]: The second endpoint is encrypted with the
.akiraextension. - 05/31/2024, 10:25:04 AM – [Endpoint 3]: A third endpoint is encrypted with the
.akiraextension.
Infection analysis
Network connections: The NTOSKRNL.EXE processes on both endpoints showed evidence of communication with the domain controller (Endpoint 2) over port 445 (SMB). This suggested that the domain controller might have been distributing the ransomware, although concrete evidence was lacking due to the endpoint being offline.
Suspicious executable: On Endpoint 2, the team identified a suspicious executable located at C:\USERS\[REDACTED]\DOCUMENTS\WIN.EXE. This executable appeared to be the ransomware encryptor, deploying the malware to internal hosts over port 445 (SMB). The process graph indicated communication with 17 different endpoints.
Attack methodology
Tools and Techniques
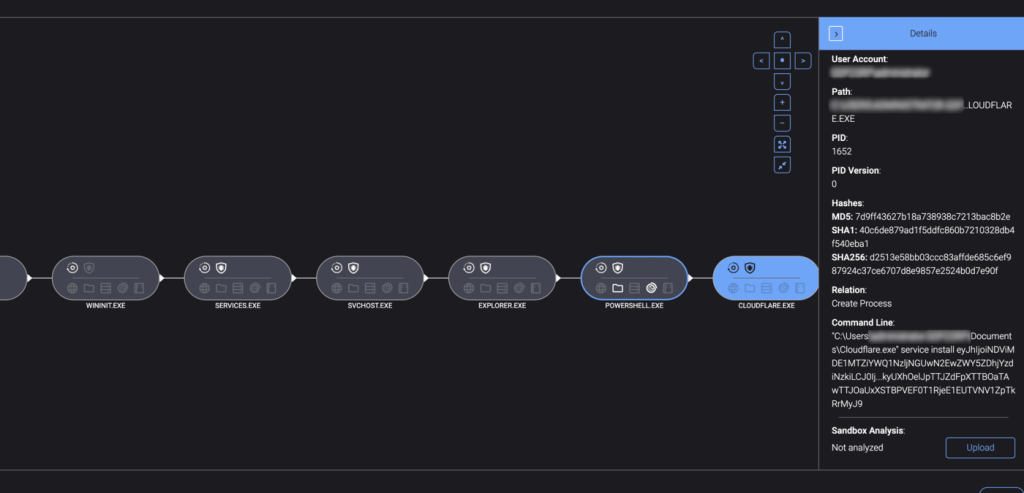
- Cloudflare Tunnel:
- Used to gain initial access to Endpoint 2.
- Command:
C:\Users\[REDACTED]\Documents\Cloudflare.exe tunnel run --token [REDACTED]
- Advanced IP Scanner:
- Used to scan the network and identify targets.
- Command:
"C:\Users\[REDACTED]\AppData\Local\Temp\Advanced IP Scanner 2\advanced_ip_scanner.exe" /portable "C:/Users/[REDACTED]/Documents/" /lng en_us
- WIN.EXE:
- Deployed ransomware to identified targets.
- Command:
"C:\Users\[REDACTED]\Documents\win.exe" -s=C:\Users\[REDACTED]\Documents\path2.txt -n=20 -remote
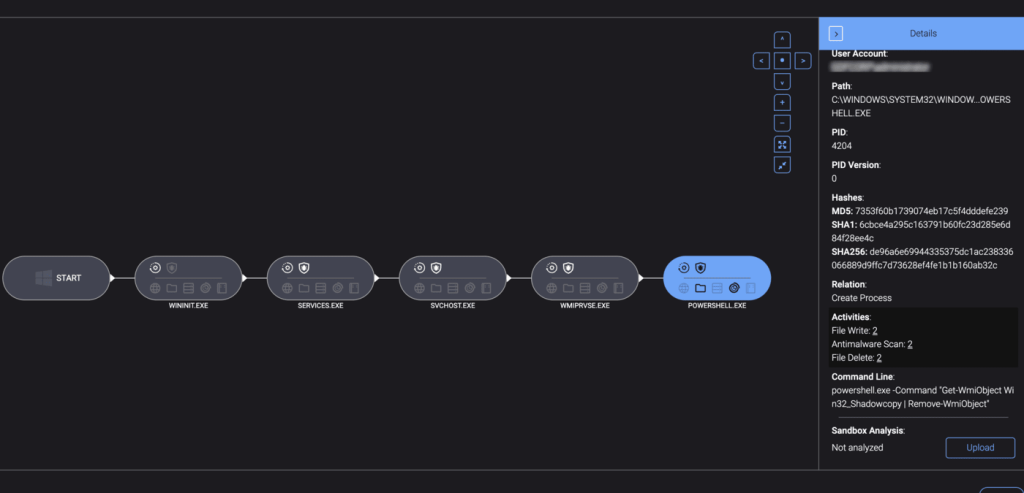
PowerShell activity
- Suspicious PowerShell and
cmd.exeactivities had been previously excluded from monitoring by the customer, blinding the team to these activities. - Proxy execution of processes through a whitelisted PowerShell resulted in the following actions:
- Dropping files to excluded directories.
- Deleting shadow copies.
- Logging users off remote hosts.
- Querying remote desktop services.
- Deleting legitimate admin users.
Screenshots of events
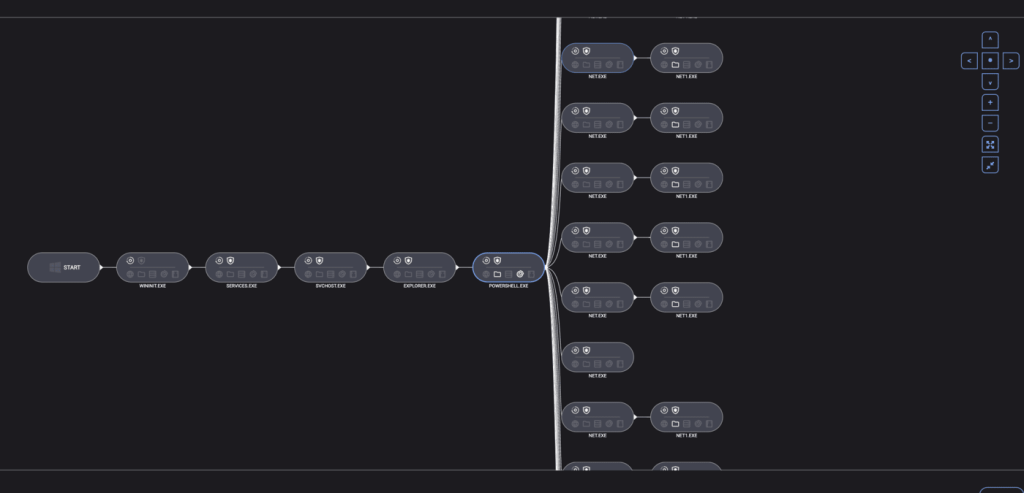

Potential root cause
The initial vector for the attack involved using PowerShell to create a Cloudflare Tunnel. This tunnel facilitated the attackers’ remote access, followed by deploying Advanced IP Scanner to identify network targets. Subsequently, the ransomware was deployed from the WIN.EXE executable.
Remediation actions
The remediation process included:
- Identifying compromised users and deactivating their accounts.
- Identifying and deleting illegitimate admin users created by the threat actors.
- Isolating impacted systems.
- Identifying and isolating the host distributing the ransomware.
- Rebuilding the list of infected machines and slowly reintroducing them back into the network.
Detecting ransomware attacks with ThreatDown MDR
By promptly isolating affected systems and revoking compromised accounts, the ThreatDown MDR team stopped the spread of Akira ransomware and initiated recovery procedures to restore normal operations.
Purpose-built for organizations with small (to non-existent) security teams that lack the resources to address threats like Akira ransomware, the ThreatDown Ultimate Bundle includes award-winning technologies and 24x7x365 expert-managed monitoring and response from the ThreatDown MDR team.




