
Is it an attacker or an IT admin? Test your skills in two minutes…
Are you a security n00b or a Certified Threat Hunter? Take our quiz and put yourself to the test!
Living off the land (LOTL) techniques have become a favorite among ransomware attackers—and for good reason.
By using Windows-native tooling and commands, attackers can make themselves look like legitimate admins and slip under the radar as they prepare their attacks.
Because attackers and admins are using the same tools and commands, it can be difficult to know what to make of suspicious activity alerts. If we dig deep enough, however, we can usually get a better grasp of whether an action has good intent or bad intent behind it.
That’s where you, the security expert, come in.
In this quiz, we’ve compiled examples of ambiguous alerts from real situations for you to test your skills on. Some of these alerts came from legit IT admin activity—and some of them came from ransomware attackers using LOTL techniques.
So, can you separate wheat from chaff, good from bad? Let’s dive into scenario one.
Scenario 1: Disable Windows Firewall
The time is 1:15 PM on a Saturday.
One of your endpoints has a Medium Severity alert for Disable Windows Firewall. The user behind this activity is USR/admin.
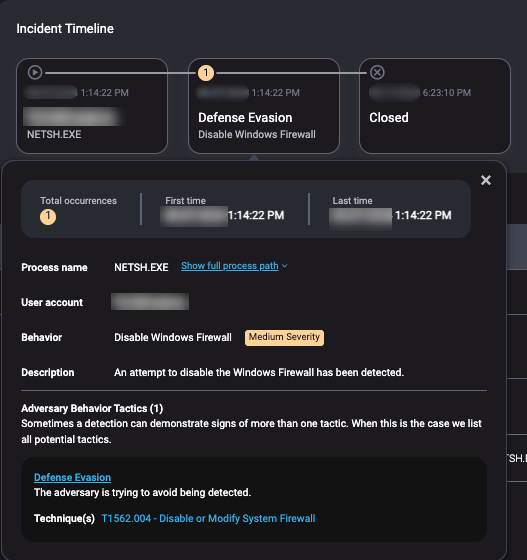
Clicking in the alert further, you find the command line for this alert is netsh advfirewall set all profiles state off.
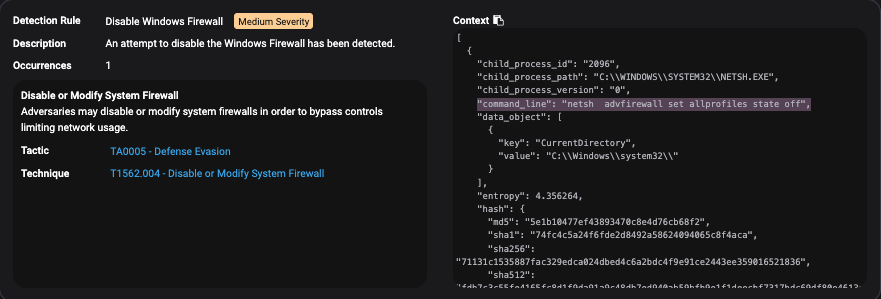
Given the day of the week, the time of day, the context of the command and account that executed it, is this an IT admin or a ransomware attack? Before you make a guess, let’s look at some quick arguments for each.
Arguments for this being a ransomware attacker:
- Odd timing on a weekend.
- Disabling all firewalls is extreme.
- Admin account could be compromised.
Arguments for this being an IT admin:
- Legitimate command for troubleshooting.
- Admin account commonly used for such tasks.
- Possible off-hours maintenance.
Click to reveal answer.
Answer: If you answered that this was ransomware attacker… you’d be wrong. This was an IT admin!
Scenario 2: Windows Firewall Add RDP Rule
The time is 4:24 AM on a Friday.
One of your endpoints has a Medium Severity alert for Windows Firewall Add Rule. The user behind this activity is USR/Administrator.
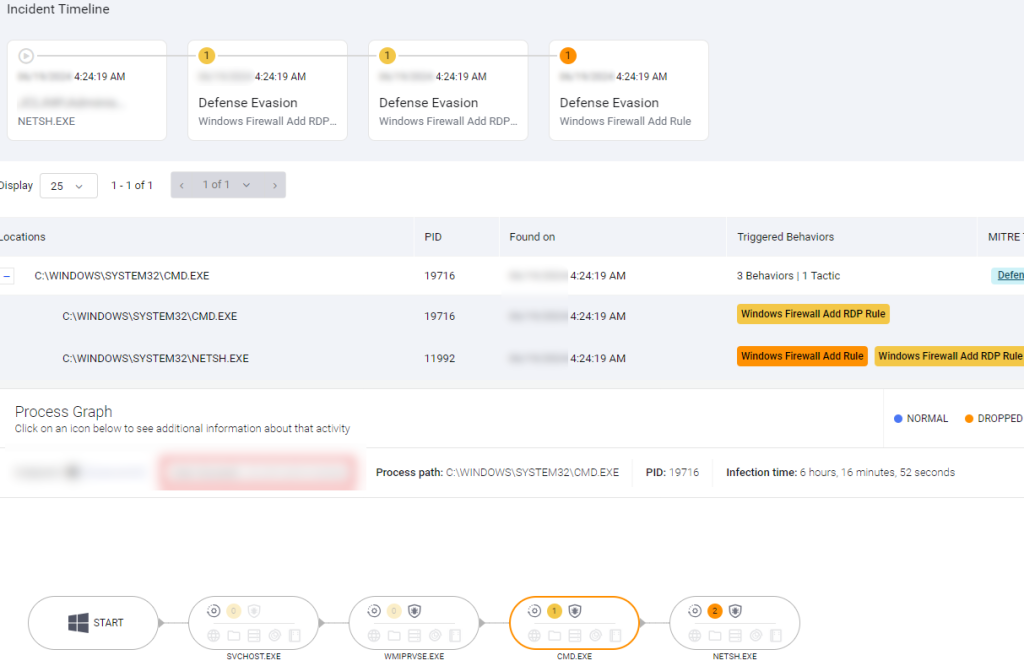
Clicking in the alert further, you find the command line for this alert is netsh advfirewall firewall add rule name="Allow RDP" protocol=TCP dir=in localport=3389 action=allow.
Given the day of the week, the time of day, the context of the command and account that executed it, is this an IT admin or a ransomware attack? Before you make a guess, let’s look at some quick arguments for each.
Arguments for this being a ransomware attacker:
- Unusual timing at 4:24 AM raises suspicion.
- Opening RDP could allow attackers remote access.
- Admin account could be compromised by attackers.
Arguments for this being an IT admin:
- Legitimate rule for enabling remote access (RDP).
- Admin account is typically used for network config changes.
- Off-hours admin tasks are common for minimizing disruptions.
Click to reveal answer.
Answer: This was a ransomware attacker! Notice how similar it is to the first scenario? That’s how tricky these attacks can be.
Scenario 3: Remote Process Creation via WMIC
The time is 2:33 PM on a Monday.
One of your endpoints has a Medium Severity alert for Remote Process Creation via WMIC. The account behind this activity belongs to the companies’ IT Helpdesk.
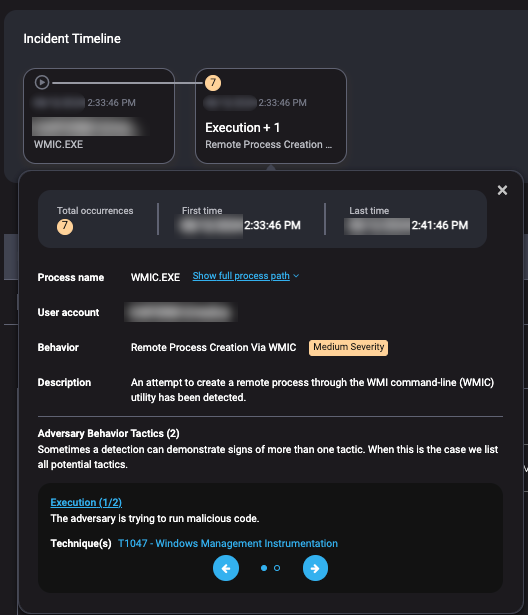
Clicking in the alert further, you find the command line for this alert is wmic /node:bb023416 system info.
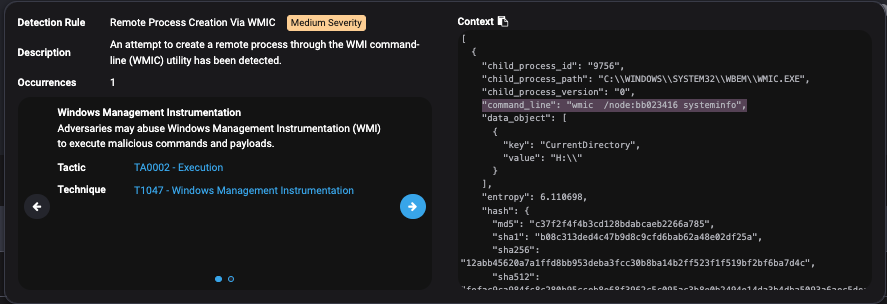
Given the day of the week, the time of day, the context of the command and account that executed it, is this an IT admin or a ransomware attack? Before you make a guess, let’s look at some quick arguments for each.
Arguments for this being a ransomware attacker:
- WMIC is often abused by attackers for reconnaissance.
- Remote process creation could indicate lateral movement.
- Helpdesk account might be compromised for malicious use.
Arguments for this being an IT admin:
- WMIC command used for gathering system info, common for support tasks.
- IT Helpdesk account typically involved in such queries.
- Normal working hours on a Monday, fitting for admin activity.
Click to reveal answer.
Answer: This was an IT admin!
Scenario 4: Privileged Group Discovery Via Net
The time is 2:36 AM on a Thursday.
One of your endpoints has a Medium Severity alert for Privileged Group Discovery Via Net. The account behind this activity belongs to an IT manager.
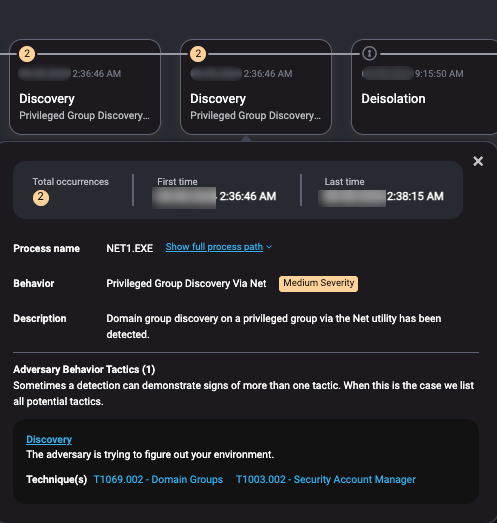
Clicking in the alert further, we find the command line for this alert is net group "Enterprise Admins" /dom.
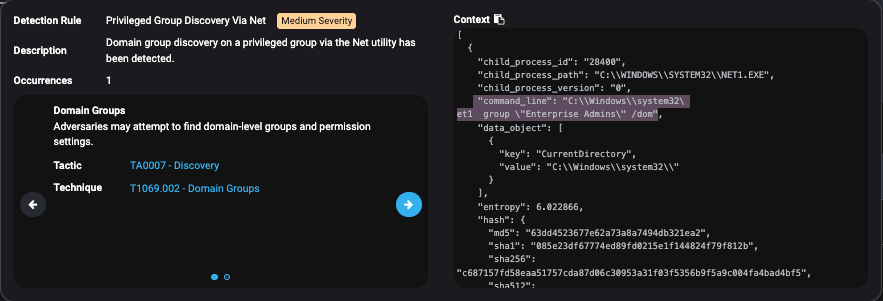
Given the day of the week, the time of day, the context of the command and account that executed it, is this an IT admin or a ransomware attack? Before you make a guess, let’s look at some quick arguments for each.
Arguments for this being a ransomware attacker:
- Suspicious time at 2:36 AM.
- Privileged group discovery is a known tactic in attacks.
- IT manager account might be compromised for escalation attempts.
Arguments for this being an IT admin:
- Querying privileged groups can be part of routine checks.
- IT manager account typically has access to perform such tasks.
- Could be off-hours maintenance or audit work.
Click to reveal answer.
Answer: This was a ransomware attacker!
Scenario 5: Domain Trust Discovery
The time is 3:45 AM on a Tuesday.
One of your endpoints has a Low Severity alert for Domain Trust Discovery. The user behind this activity is USR/Administrator.
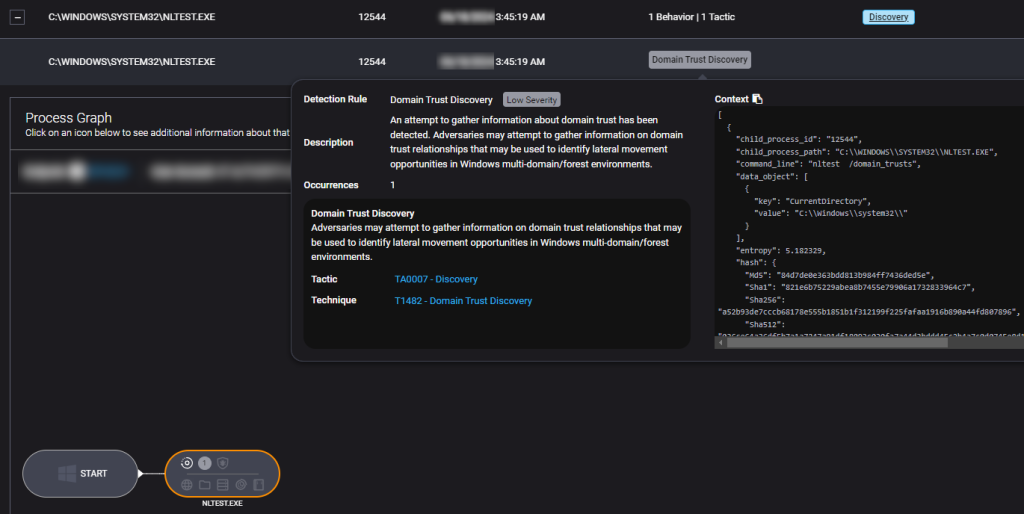
Clicking in the alert further, you find the command line for this alert is nltest /domain_trusts.
Given the day of the week, the time of day, the context of the command and account that executed it, is this an IT admin or a ransomware attack? Before you make a guess, let’s look at some quick arguments for each.
Arguments for this being a ransomware attacker:
- Unusual time at 3:45 AM.
- Domain trust discovery is common in attacker reconnaissance.
- Administrator account may be compromised for lateral movement.
Arguments for this being an IT admin:
- Domain trust checks can be part of network maintenance.
- Administrator account is typically used for such operations.
- Possible off-hours network troubleshooting.
Click to reveal answer.
Answer: This was a ransomware attacker!
How did you do?
0/5 – Rookie Mistake
Oof, tough start! But don’t sweat it—there’s always time to level up those LOTL detection skills.
1/5 – Almost There
One right! You’re starting to warm up. A little more practice and you’ll be catching attackers in no time.
2/5 – On the Radar
Not bad! You’re getting a feel for it, but a few attackers or false positives slipped by. Keep sharpening those skills.
3/5 – Security Scout
You’re more than halfway there! You’ve got a solid grasp, but a little more vigilance could go a long way.
4/5 – Threat Hunter
So close! You’re nearly unstoppable—just one sneaky attacker or false positive got past you. Next time, they won’t be so lucky.
5/5 – ThreatDown MDR Analyst
Perfect score! You’re the boss of alerts—ransomware and false positives don’t stand a chance against you!
The bigger picture
As you can see, LOTL attacks can be really tricky. With attackers using the same native Windows tools that your IT team might use every day, the arguments for both IT admin activity and ransomware attacks are often equally convincing.
Needless to say, it takes more than a quick guess to get it right. Each alert needs careful investigation, from digging into the context to reaching out to the account owner and verifying if the activity was legitimate or not. Assuming without confirming can lead to dangerous blind spots.
Timing, of course, is one of the biggest clues.
As we pointed out in our 2024 State of Ransomware report, a majority of ransomware attacks now happen in the early morning hours—exactly like some of the examples here. Seeing suspicious activity at 3 or 4 AM, like disabling firewalls or adding RDP rules, should immediately make you pause. Watching for unusual admin tool use during off-hours is a practical way to get ahead of these threats.
But monitoring alerts around the clock requires constant attention—and for those without that sort of team, that’s where ThreatDown MDR comes in.
Our team of dedicated analysts monitors your network 24×7, diving into alerts in real-time. They handle the investigation, cross-check details, and reach out when needed to confirm whether the activity is legit or a potential threat. With ThreatDown MDR on your side, you’ve got eyes on your network no matter the time of day, catching threats before they can cause harm.
Get in touch with ThreatDown MDR today here and make sure your network is protected every hour of the day.




