Cl0p ransomware gang claims first victims of the MOVEit vulnerability
On Friday June 2, 2023 we reported about a MOVEit Transfer vulnerability that was actively being exploited. If your organization uses MOVEit Transfer and you haven’t patched yet, it really is time to move it.
Excuse the bad pun, but yesterday we saw the first victims of this vulnerability come forward. MOVEit Transfer is a widely used file transfer software which encrypts files and uses secure File Transfer Protocols to transfer data. As such, it has a large userbase in healthcare, education, US federal and state government, and financial institutions.
The Common Vulnerabilities and Exposures (CVE) database lists publicly disclosed computer security flaws. On Friday the CVE had not been assigned yet, but now this vulnerability has now been listed as:
CVE-2023-34362: In Progress MOVEit Transfer before 2021.0.6 (13.0.6), 2021.1.4 (13.1.4), 2022.0.4 (14.0.4), 2022.1.5 (14.1.5), and 2023.0.1 (15.0.1), a SQL injection vulnerability has been found in the MOVEit Transfer web application that could allow an unauthenticated attacker to gain access to MOVEit Transfer’s database. Depending on the database engine being used (MySQL, Microsoft SQL Server, or Azure SQL), an attacker may be able to infer information about the structure and contents of the database, and execute SQL statements that alter or delete database elements. NOTE: this is exploited in the wild in May and June 2023; exploitation of unpatched systems can occur via HTTP or HTTPS. All versions (e.g., 2020.0 and 2019x) before the five explicitly mentioned versions are affected, including older unsupported versions.
Microsoft says that the group behind the attacks on MOVEit instances is the Lace Tempest group, which is a known ransomware operator and runs the extortion website Cl0p. This was confirmed by a Cl0p representative to Bleeping Computer, who also said that the criminals started exploiting the vulnerability on May 27th, during the US Memorial Day holiday.
We saw a similar scenario unfold in March which caused Cl0p to occupy the first place as most used ransomware in our Ransomware Review for that month. Contributing to Cl0p’s rise to the number one spot was its extensive GoAnywhere campaign. The group successfully breached over 104 organizations by taking advantage of a zero-day vulnerability in the widely-used managed file transfer software, GoAnywhere MFT.
As we have pointed out before, ransomware gangs can afford to play the long game now. And some of them do. When you have hundreds or maybe even thousands of victims to choose from, you start with the juiciest ones that are most likely to pay.
Payroll provider Zellis who serves British Airways and the BBC would be a good example of that. Pharmacy chain Boots, which employs more than 57,000 people in the UK and Ireland, has also announced that it has been impacted.
A Reuters reporter that has an inside contact in the Cl0p ransomware gang tweeted a screenshot of his contact saying that the military, gov(ernment), children’s hospitals, and police would not be attacked.
The same was repeated by BleepingComputer’s contact. But this is no guarantee, and in the end they may not be able to resist the urge to steal data from those networks anyway.
All this means that if your organization uses MOVEit Transfer and it is internet facing, you should assume that your network has been breached. The fact that you haven’t noticed anything yet probably means you are low on the list of desirable targets. It does NOT mean you got away lucky and simply patching the vulnerability is enough.
What needs to be done
First of all, MOVEit Transfer users should visit the Progress security bulletin about this vulnerability and bookmark it. You can find the latest advice, Indicators of Compromise (IOCs), affected versions, and available patches there.
Basically the advice, and you can find detailed instructions on the page, is to:
- Disable all HTTP and HTTPs traffic to your MOVEit Transfer environment.
- Delete unauthorized files and user accounts.
- Reset service account credentials for affected systems and the MOVEit Service Account.
- Apply the patch or upgrade.
- Verify to confirm the files have been successfully deleted and no unauthorized accounts remain.
- Re-enable all HTTP and HTTPs traffic to your MOVEit Transfer environment.
- Continue to monitor your network, endpoints, and logs for IoCs.
Additionally, users of MOVEit Transfer with Microsoft Azure integration should take immediate action to rotate their Azure storage keys.
In our previous post about this vulnerability I mentioned a few tools to help you find the malicious artifacts:
- MoveIT-WebShellCheck a Python script by ZephrFish
- Sigma rule by Florian Roth
- Yara rule by Florian Roth
- Sigma rule by tsale
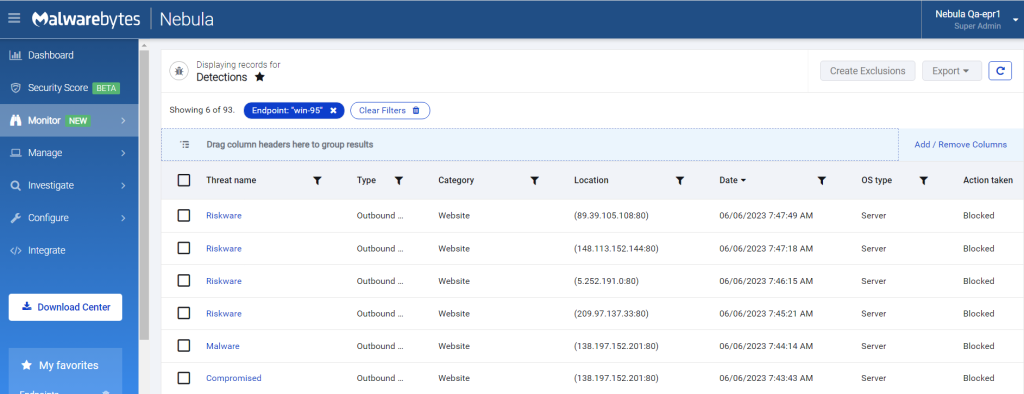
Malwarebytes detects the malicious webshell C:MOVEitTransferwwwroothuman2.aspx as Exploit.Silock.MOVEit and blocks five malicious IP addresses—138.197.152.201, 209.97.137.33, 5.252.191.0/24, 148.113.152.144, 89.39.105.108—that were found to be looking for vulnerable systems.