
GrimResource MSC attack uses 5-year-old vulnerability
Cybercriminals’ search for an alternative to Office macros has brought them to MSC files used by the Microsoft Management Console.
Researchers in South Korea have discovered a new attack method that could be adopted by ransomware groups.
Since Microsoft started blocking Office macros in documents downloaded from the Internet—or more specifically, documents with the Mark-of-the-Web (MotW)—cybercriminals have been looking for new ways to get victims to execute malicious code.
So far, none of them have been had the sticking power of macros. At first, cybercriminals focused on ways to remove the MotW by packaging documents in ISO and ZIP files. But Microsoft and 7-zip put an end to those options, so the search moved on.
The new attack method, dubbed GrimResource, was noticed in attacks by the Kimsuky APT group, a North-Korean state-sponsored group, against activists in the North Korean human rights and anti-North Korea sectors. But there are also signs it was deployed against Japan.
The attackers used Windows MSC (.msc) files, which are used in the Microsoft Management Console (MMC). Microsoft Management Console (MMC) can be used to create, save and open administrative tools, called consoles, which manage the hardware, software, and network components of your Microsoft Windows operating system. MMC runs on all Windows client operating systems that are currently supported.
In the observed attack, the attackers contacted the target on Facebook and invited them to download an MSC file disguised as a Word document from OneDrive. The icon of the MSC was changed to match the Word icon, and its “Run” button was changed to “Open”, so that targets would be less suspicious.
When the target clicks “Open”, the malicious command set inside is executed, exploiting a XSS vulnerability in Microsoft’s apds.dll library with DotNetToJScript, which gives the attacker arbitrary code execution. DotNetToJScript is a free tool to generate JScript that bootstraps an arbitrary .NET Assembly and class. So, basically this will execute arbitrary .NET code through the JavaScript engine, bypassing any security measures in place.
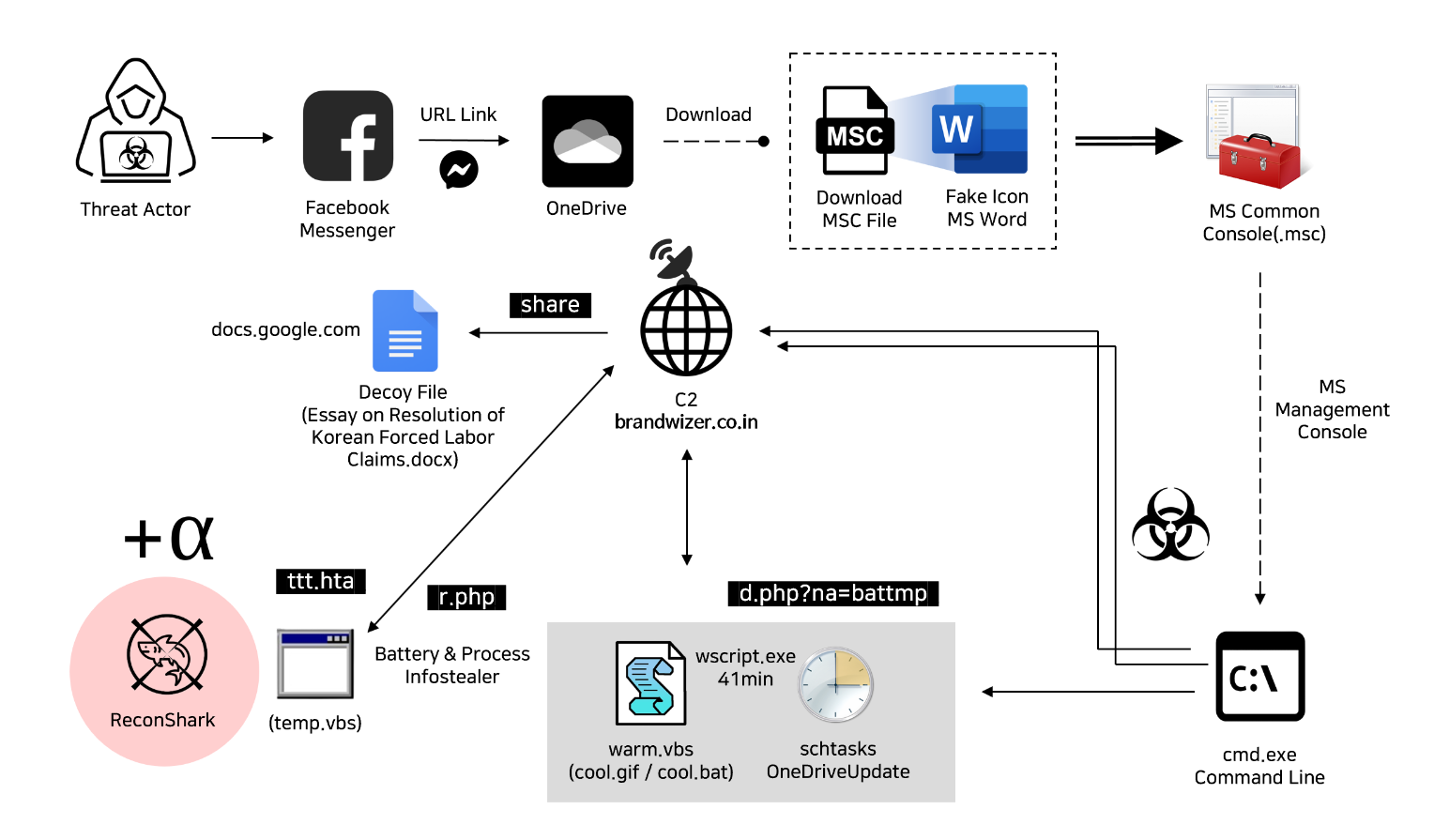
Through some obfuscated and stealthy scripts, the final payload is injected into a new instance of dllhost.exe. The observed payload was Cobalt Strike. Cybercriminals deploy Cobalt Strike to map out a network and identify any vulnerabilities, as well as deploy implants, backdoors, and other tools to accomplish lateral movement and a complete compromise of the network.
With a working exploit available, it probably won’t be too long before ransomware groups start to use this method. Maybe it’s time for Microsoft to issue a patch for the apds.dll vulnerability that was discovered in 2019.
Threat hunting
System administrators, defenders, and Managed Detection and Response (MDR) teams are advised to be on the lookout for:
- File operations involving apds.dll invoked by mmc.exe.
- Suspicious executions via MCC, especially processes spawned by mmc.exe with .msc file arguments.
- Read-write-execute (RWX) memory allocations by mmc.exe that originate from script engines or .NET components.
- Unusual .NET COM object creation within non-standard script interpreters like JScript or VBScript.
- Temporary HTML files created in the INetCache folder as a result of APDS XSS redirection.
Also, Elastic Security has also published a complete list of GrimResource indicators on GitHub and provided YARA rules in the report to help defenders detect suspicious MSC files.
We don’t just report on vulnerabilities—we identify them, and prioritize action.
Cybersecurity risks should never spread beyond a headline. Keep vulnerabilities in check by using ThreatDown’s Vulnerability Assessment and Patch Management solutions.




