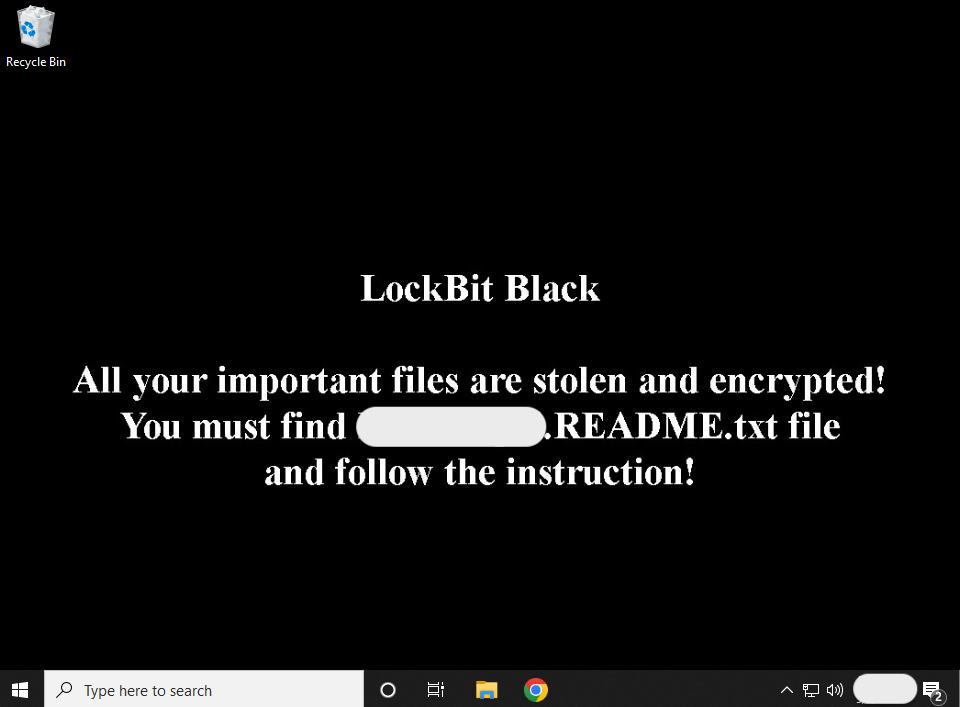
LockBit Black
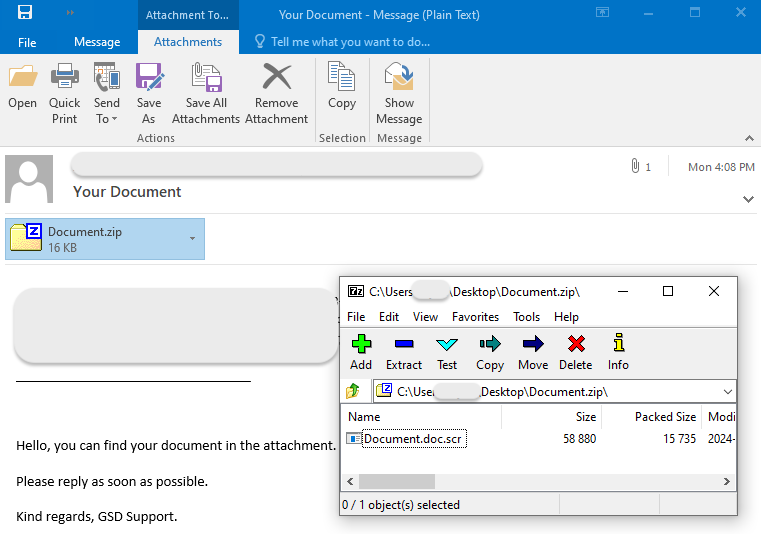
LockBit Black via zipped attachment in email
LockBit Black, tested on May 1, 2024
Today we are looking at a ransomware attack that originated from a malicious email. This is a typical social-engineering attack that could target any of your employees, and perhaps would be most effective against those who regularly communicate with third parties. The lure here is a Document, but it could very well be more specific, such as an invoice, a parking ticket, etc.
This email is from a malspam campaign that was observed around the end of April 2024 initiated by a ransomware affiliated with LockBit Black (AKA LockBit 3.0).
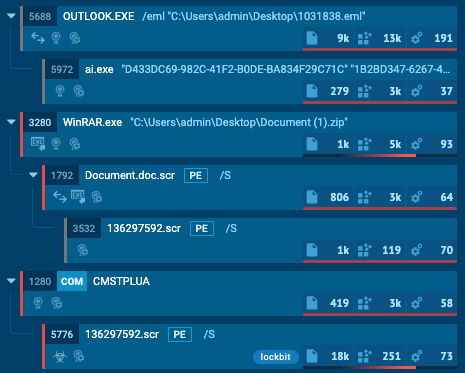
Distribution (email->ZIP->SCR->download EXE)
This LockBit Black malware sample was distributed via a malspam campaign using the Phorpiex botnet. The email with subject “Your Document” contains a zipped attachment. The file inside the archive uses the double extension trick (.doc.scr) to mimic a Word document.
Wallpaper change:
Encrypted documents:

Ransom note:
!! ALL YOUR FILES ARE ENCRYPTED !!!
You can't restore them without our decryptor.
Don't try to use any public tools, you could damage the files and lose them forever.
To make sure our decryptor works, contact us and decrypt one file for free.
Download TOX messenger: https://tox[.]chat/
Add friend in TOX, ID: {sanitized}Process flow
Protection
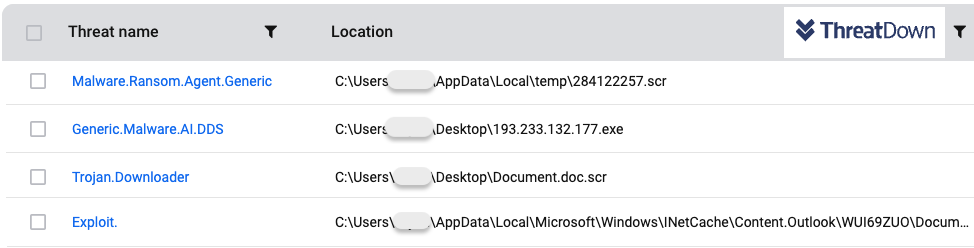
We tested ThreatDown by looking at each protection layer:
- Anti-Exploit: attachment blocked when opened from email client
- Anti-Malware engine: attachment detected when executed from disk
- Anti-Malware engine: LockBit payload when executed from disk
- Anti-Ransomware: Lockbit encryption
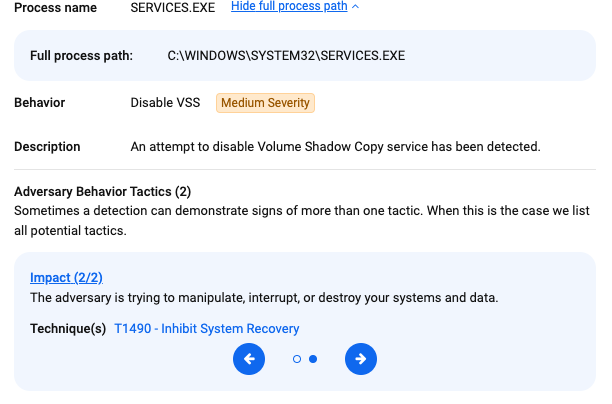
Endpoint Detection and Response (EDR)
EDR detected suspicious activity related to LockBit disabling volume shadow copies.
Mitigations
ThreatDown customers were already protected against this threat, and not just via one specific security layer. This is especially important for threats like ransomware because they are very destructive by nature.
There were a few elements in this attack that anyone can learn from:
- The malicious email was asking the user to “reply as soon as possible”. This is a common tactic used by criminals because they know that they often have a very limited time window before their payload is being detected. They want you to do something quickly and let your guards down.
- The attachment, a zip file, contained an executable. Many, if not most email clients do not allow executables to be attached directly as is. Threat actors will compress them as .zip, .rar or some other extension. There are of course legitimate archives, but you should be extra careful when a file is packaged that way.
- The file inside the zip was named Document.doc.scr. The thing is, Microsoft Windows will often omit known extension types. Because of that, the file will look like it has a .doc extension (and therefore seems like a document) whereas it is in fact a .scr (screensaver, but executable). It is a good idea to change that setting and force Windows to show you all extensions.
Did you like this walkthough? For more, check out our index page here.
Indicators of Compromise (IOCs)
Email subject
Your Document
Email body
Hello, you can find your document in the attachment.
Please reply as soon as possible.
Kind regards, GSD Support.
Attachment name
Document.zip
Attachment SHA256
1c5fd7bf511885054464124142f793501ab2c6e987b203c1a5f4b3bdcccb1fa1
Extracted attachment name
Document.doc.scr
Extracted attachment SHA256
0cc54ffd005b4d3d048e72f6d66bcc1ac5a7a511ab9ecf59dc1d2ece72c69e85
LockBit download URL
hxxp[://]193[.]233[.]132[.]177/lbb[.]exe
LockBit SHA256
a18a6bacc0d8b1dd4544cdf1e178a98a36b575b5be8b307c27c65455b1307616