
Lowe’s employees targeted in new malvertising campaign
In August, Lowe’s employees were the subject of a targeted campaign using fake ads and websites.
In mid-August, researchers for Malwarebytes Labs identified a malvertising campaign targeting Lowes employees via Google ads. Lowe’s employees who searched for “myloweslife” during that time may have been exposed to fraudulent ads that linked to a replica of the company’s My Lowe’s Life employee portal, setup to steal their login credentials.
Combining ads with a phishing page like this is a proven recipe for criminal success. The ruse works because unsuspecting users often rely on Google Search to take them to the sites they know, rather than manually entering the full URL in the browser’s address bar.
Malwarebytes’ Senior Director of Threat Research, Jerome Segura, found two different advertiser accounts impersonating My Lowe’s Life, and in one instance even saw three malicious ads, each using different lookalike URLs, on a single search result.
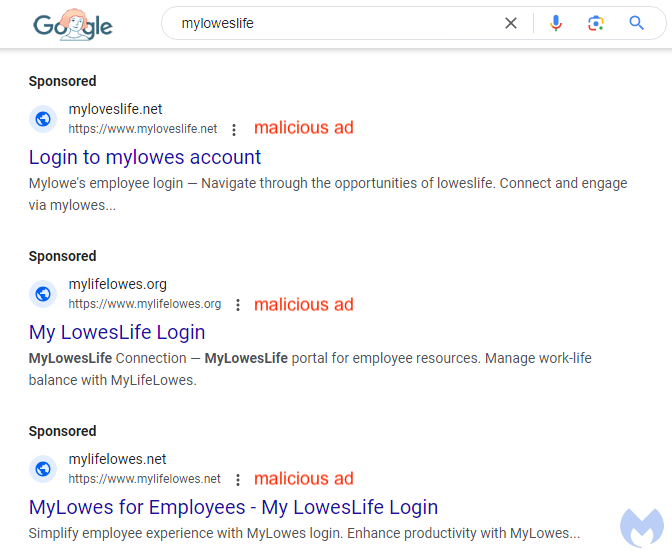
When victims clicked on one of the malicious Google ads, they were taken directly to a phishing page with a URL resembling the structure used by the real My Lowe’s Life website. The phishing page was an exact replica of the real Lowe’s portal, and asked users for their sales number and password, and on a subsequent page their security question. The details were then dispatched to the threat actor using an asynchronous POST request, and the victim was redirected to the real My Lowe’s Life website.
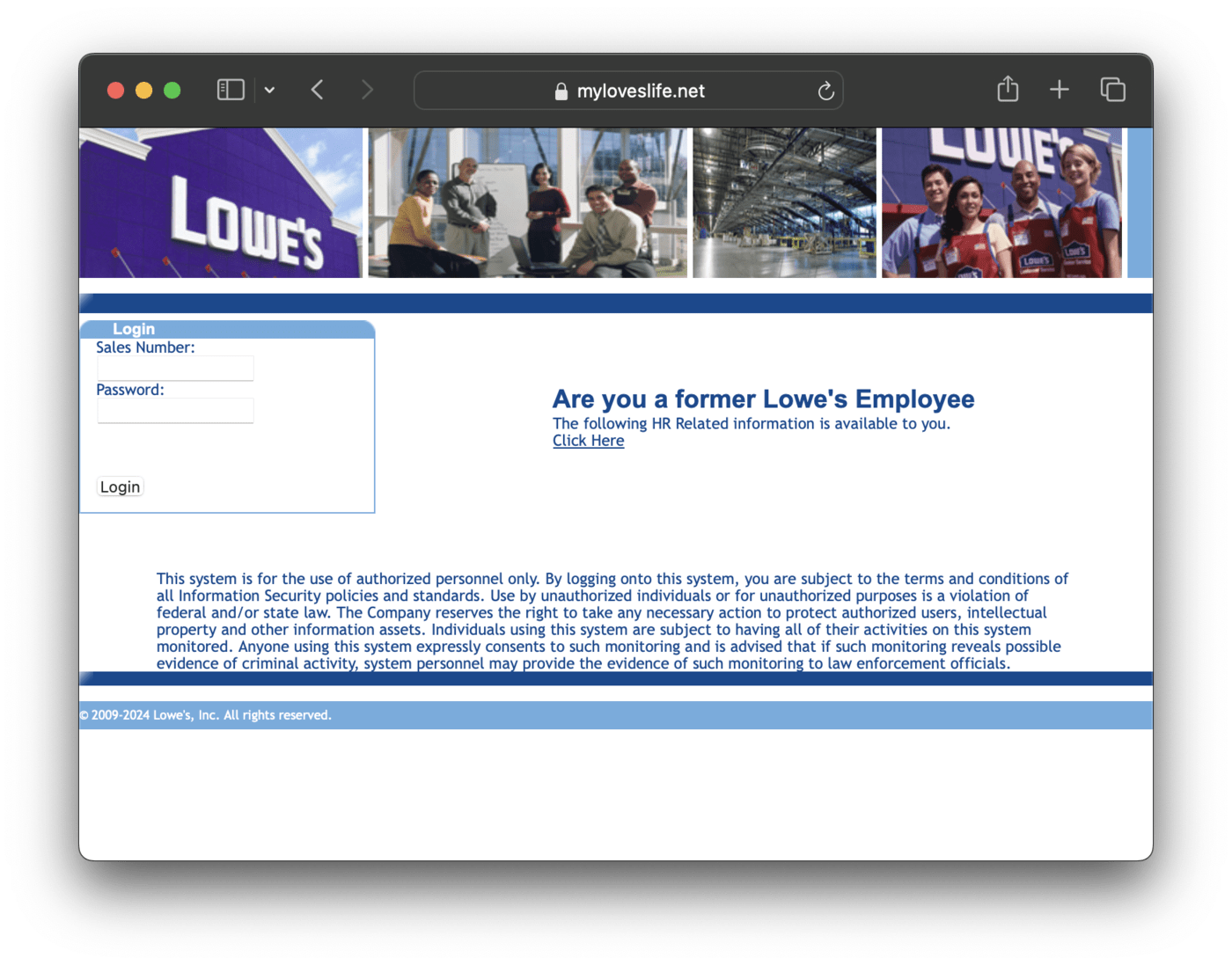
Although the phishing page linked from the ads resembled the Lowe’s website, the home pages of the phishing sites did not.
Instead, they used a generic ‘retail store’ design this acts as a disguise so that if anyone visited the sites by going directly to their home pages rather than following links from Google ads, they would not see anything malicious.
How ThreatDown protects against malicious websites
Brand impersonation via Google ads is a popular technique used by threat actors of all kinds. They know people will open up their default browser, do a quick search, and that’s exactly where they can target them.
The seven layers of protection in ThreatDown’s Endpoint Detection and Response includes Web Protection, which blocks access to and from known or suspicious internet addresses.




