Medusa ransomware: What organizations need to know
Organizations beware: the Medusa ransomware gang is on the rise.
Organizations beware: the Medusa ransomware gang is on the rise.
It’s quite rare that we see a ransomware gang tally as many victims, and in so short a time, as the Medusa ransomware gang has. Since we profiled them in March 2023, the group has executed 194 confirmed attacks—making them the eighth most prolific ransomware gang since February 2022.
In this article, we’ll explore who exactly Medusa is and how can organizations protect against them.

Medusa ransomware victimology
Medusa’s victimology doesn’t differ much from a majority of ransomware gangs, with an outsized focus on the US and the Services Industry. That said, there are two industries they attack at an above-average rate: Education and Healthcare.
Their recent explosion in monthly number of attacks is likely due to law enforcement disrupting two of the biggest ransomware gangs, LockBit and ALPHV, back in February, creating a new influx of customers for gangs like Medusa and others.


Medusa ransomware tactics, techniques, and procedures (TTPs)
The ThreatDown MDR and Threat Intelligence Teams have observed the following Medusa ransomware tactics, techniques, and procedures based on a recent attack on a national company in the Services industry:
| Tactic | Technique | IOC Example |
|---|---|---|
| Execution | Command and Scripting Interpreter | Use of PowerShell to execute malicious commands (powershell -exec bypass -enc QQBkAGQA LQBiNAHAAUABgAGUAZgBlAHIAZQBuAG cMAZQAgAC0ARQB4AGMABjA1AHMAZQB BvAGAUAUBhAHQAaAAlgACIAQwA6AFwA IgA=) |
| Defense Evasion | Impair Defenses | Termination of Microsoft Defender and ThreatDown processes using a loaded driver (C:\WINDOWS\G0BSJ5IAHI.EXE) (35dfc1fcb06fe31264a3fc7ff307e166) |
| Lateral Movement | Use of Remote Services | Execution of further payloads via PDQ Deploy across the network. |
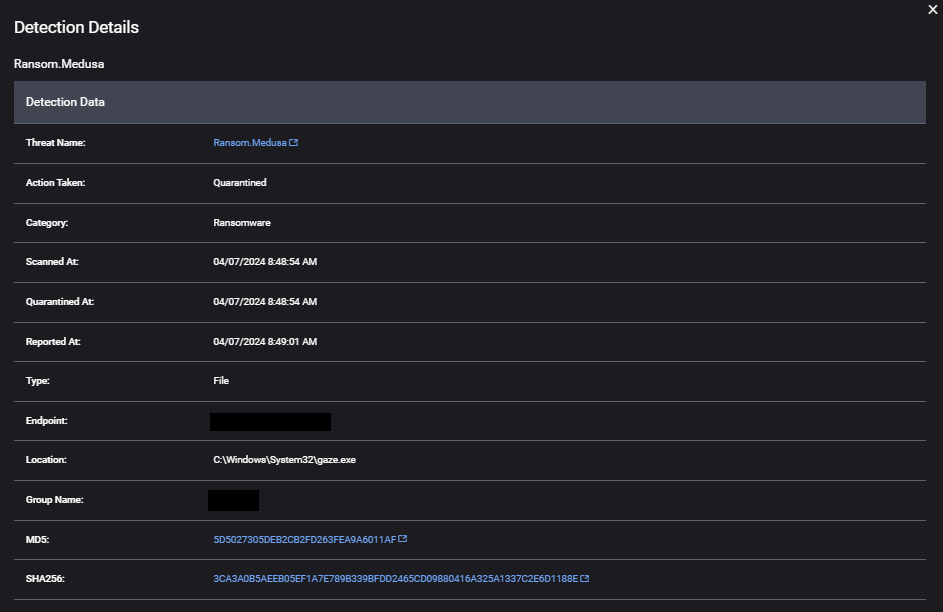
| Impact | Data Encrypted for Impact | Encryption activities conducted by C:\WINDOWS\System32\gaze.exe (5D5027305DEB2CB2FD263FEA9A6011AF) |
Our full customer case study, available here, outlines the sequence of events and key indicators associated with a Medusa ransomware attack, including using PDQ Deploy to remotely execute a payload that loads a vulnerable driver to terminate Defender and ThreatDown processes and a ransomware payload (Medusa). The ThreatDown MDR team’s prompt detection and response, involving isolating affected endpoints, mitigated the attack.
How to prevent Medusa ransomware
Medusa has made a big name for itself in a short amount of time.
While it looks like Medusa will attack anyone they think is an easy target, it’s safe to say that educational organizations in the USA should be particularly wary of Medusa considering their strong focus on that country and sector.
We recommend the organizations across all sectors follow a few best practices to prevent (and recover) from ransomware attacks from every angle. That includes:
- Block common forms of entry. Create a plan for patching vulnerabilities in internet-facing systems quickly; disable or harden remote access like RDP and VPNs; use endpoint security software that can detect exploits and malware used to deliver ransomware.
- Detect intrusions. Make it harder for intruders to operate inside your organization by segmenting networks and assigning access rights prudently. Use EDR or MDR to detect unusual activity before an attack occurs.
- Create offsite, offline backups. Keep backups offsite and offline, beyond the reach of attackers. Test them regularly to make sure you can restore essential business functions swiftly.
- Don’t get attacked twice. Once you’ve isolated the outbreak and stopped the first attack, you must remove every trace of the attackers, their malware, their tools, and their methods of entry, to avoid being attacked again.
Purpose-built for organizations with small (to non-existent) security teams that lack the resources to address all security alerts, the ThreatDown Elite Bundle includes award-winning technologies and 24x7x365 expert-managed monitoring and response from the ThreatDown MDR team.




