
New RansomHub attack uses TDSSKiller and LaZagne, disables EDR
The attack signals a new shift in RansomHub’s arsenal of tools.
The ThreatDown Managed Detection and Response (MDR) team recently identified the RansomHub ransomware gang using a previously unseen method of attack using two tools: TDSSKiller, employed to disable endpoint detection and response (EDR) systems, and LaZagne, used to harvest credentials.
Although both TDSSKiller and LaZagne have been used by attackers for years, this is the first record of RansomHub using them in its operations, with the TTPs not listed in CISA’s recently published advisory on RansomHub. The tools were deployed following initial reconnaissance and network probing through admin group enumeration, such as net1 group "Enterprise Admins" /do.
TDSSKiller
After completing its reconnaissance and privilege enumeration, RansomHub attempted to disable security services using TDSSKiller, a legitimate tool developed by Kaspersky to remove rootkits. It is also capable of disabling EDR software through a command line script or batch file, as shown below.

RansomHub used TDSSKiller to attempt to disable several essential security services. Because the attacker had admin privileges, the attempt to disable the service can be successful, even with anti-tampering protections on.
Command line details:
- Command line:
tdsskiller.exe -dcsvc [....]- The -dcsvc flag was used to target specific security services.
- File path: The attackers attempted to run TDSSKiller from a temporary directory (
C:\Users\<User>\AppData\Local\Temp\), with a dynamically generated filename like{89BCFDFB-BBAF-4631-9E8C-P98AB539AC}.exe.

The Sangfor Cyber Guardian Incident Response (IR) team has written about the LockBit ransomware gang also using the -dcsvc parameter of TDSSKiller in an attack:
The “-dcsvc <service_name>” command deletes the specified service, removing the registry keys and executables associated with the service and software, as shown in the test conducted on Windows Defender Antimalware Client Version: 4.18.23050.5.
IOCs
File Name: TDSSKiller.exe
SHA-256: 2d823c8b6076e932d696e8cb8a2c5c5df6d392526cba8e39b64c43635f683009
File Size: 4.82 MB
MD5: ff1eff0e0f1f2eabe1199ae71194e560
LaZagne
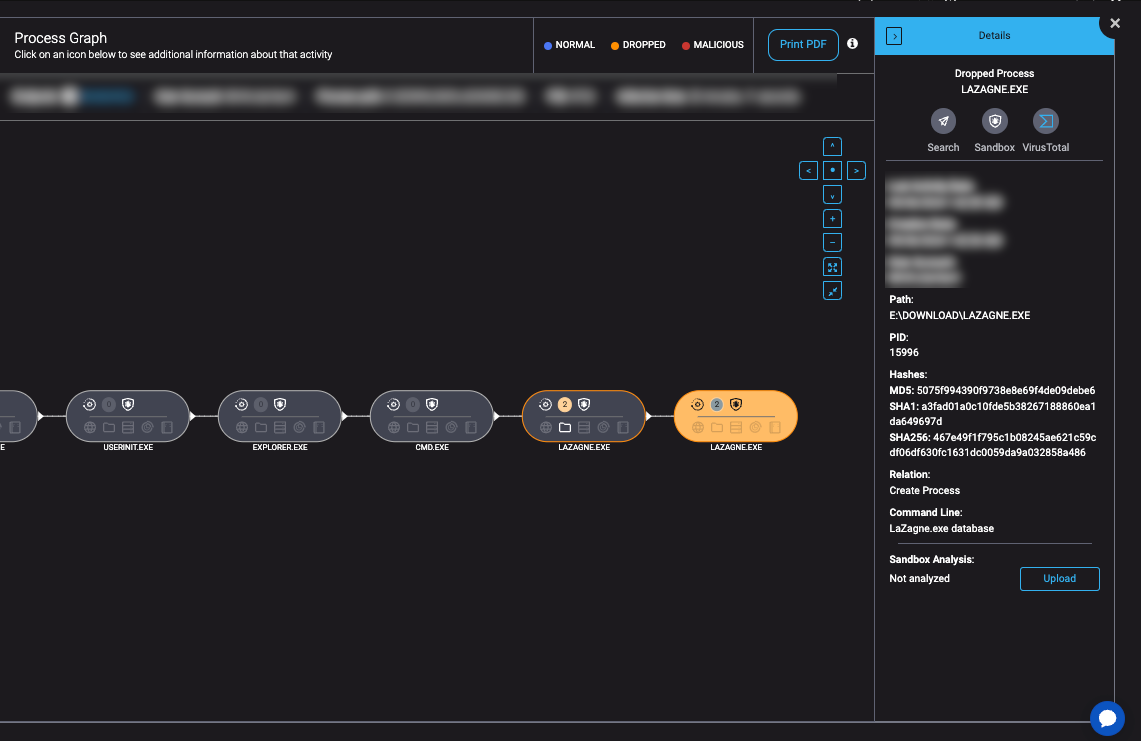
RansomHub also attempted to deploy LaZagne, a well-known credential-harvesting tool, to extract stored credentials from the compromised system. LaZagne allows attackers to retrieve login information from various applications, including browsers, email clients, and databases, enhancing their ability to move laterally within the network.
Command line details:
- Command line: LaZagne.exe database
- The attackers specifically targeted database credentials, a key asset in their broader plan to access critical infrastructure and escalate privileges. Database credentials can grant attackers control over sensitive data or administrative access to critical systems.
- File write and delete activity: LaZagne generated 60 file writes and 1 file deletion during its execution. These writes were likely logs of extracted credentials, while the deletion likely served to cover up traces of the credential-harvesting operation.
IOCs
File Name: LaZagne.exe
SHA-256: 467e49f1f795c1b08245ae621c59cdf06df630fc1631dc0059da9a032858a486
File Size: 9.66 MB
MD5: 5075f994390f9738e8e69f4de09debe6
Mitigations and advice
ThreatDown currently detects TDSSKiller as RiskWare.TDSSKiller and LaZagne as Malware.AI.2681500992. Because this campaign is very active currently, we’ve also added a detection rule to quarantine TDSSKiller when executed with a cmdline to target security services. To further defend against ransomware attacks using EDR killers and credential stealers, we suggest the following:
- Restrict Bring Your Own Vulnerable Driver (BYOVD) exploits: Implement controls to monitor and restrict vulnerable drivers like TDSSKiller, especially when executed with suspicious command-line flags such as
-dcsvc. Quarantining or blocking known misuse patterns while allowing legitimate uses can prevent BYOVD attacks. - Isolate critical systems: Use network segmentation to limit lateral movement. This can prevent attackers who gain access to credentials from spreading across the network and accessing sensitive databases.
For organizations without an in-house team to investigate and respond to suspicious activity around-the-clock, ThreatDown Managed Detection and Response (MDR) services provide expert monitoring and swift threat response to ransomware threats 24x7X365. Reach out for a quote today.




