
Patch now! VMWare releases fix for critical vulnerabilities
Broadcom notified VMWare users about an update for VMware vCenter Server which addresses three critical vulnerabilities.
Broadcom notified VMWare users about an update for VMware vCenter Server which addresses three critical vulnerabilities.
VMWare vCenter Server is server management software that provides a centralized platform for controlling VMware vSphere environments, enabling the management of virtual machines and ESXi hosts.
Affected products are:
- vCenter Server 7.0
- vCenter Server 8.0
- VMware Cloud Foundation 4.x
- VMware Cloud Foundation 5.x
The links to the appropriate updates and their release notes can be found in the VMware Security Advisory. To fully protect yourself and your organization, install the patch version of your product as listed in the security advisory.
The CVEs covered in these updates are CVE-2024-37079, CVE-2024-37080, and CVE-2024-37081.
CVE-2024-37079 (CVSS score 9.8 out of 10) is a heap-overflow vulnerability in the implementation of the Distributed Computing Environment / Remote Procedure Calls (DCERPC) protocol. A malicious actor with network access to vCenter Server may trigger this vulnerability by sending a specially crafted network packet potentially leading to remote code execution (RCE).
A buffer overflow is a programming flaw that lets the data written to a reserved memory area (the buffer) go outside of bounds (overflow), allowing it to write data to adjacent memory locations. This means attackers can control the content of certain memory locations that they should not be able to access, which they then exploit to their advantage. Heaps are memory areas allocated to each program. Memory allocated to heaps can be dynamically allocated, which occasionally results in an overflow vulnerability.
DCERPC was established as a method to allow distributed software to be run as if it was all working on the same system. Information leakage is a known risk associated with DCERPC. An attacker can often gain vital information about the services running on the servers by querying systems using DCERPC.
CVE-2024-37080 (CVSS score 9.8 out of 10) is another heap-overflow vulnerability in the implementation of the DCERPC protocol. A malicious actor with network access to vCenter Server may trigger this vulnerability by sending a specially crafted network packet potentially leading to remote code execution.
CVE-2024-37081 (CVSS score 7.8 out of 10) are multiple local privilege escalation vulnerabilities due to misconfiguration of sudo. An authenticated local user with non-administrative privileges may exploit these issues to elevate privileges to root on vCenter Server Appliance.
Sudo allows a system administrator to delegate authority and give certain users the ability to run commands as root, essentially offering them full control.
VMWare says it has no knowledge of existing active exploitation, but it urges users to patch as soon as possible. Given the high CVSS scores of the RCE vulnerabilities, exploitation should not be very difficult and could have serious consequences.
Due to how many organizations use them on a daily basis, virtual machines are valuable targets to cybercriminals of all kinds—and ransomware groups in particular. We agree with Broadcom that it is prudent to fix these vulnerabilities as soon as you possibly can.
Streamlining Vulnerability Response with ThreatDown
Managing vulnerabilities and patches yourself can be a pain; however, ThreatDown takes care of vulnerability management all from one console.
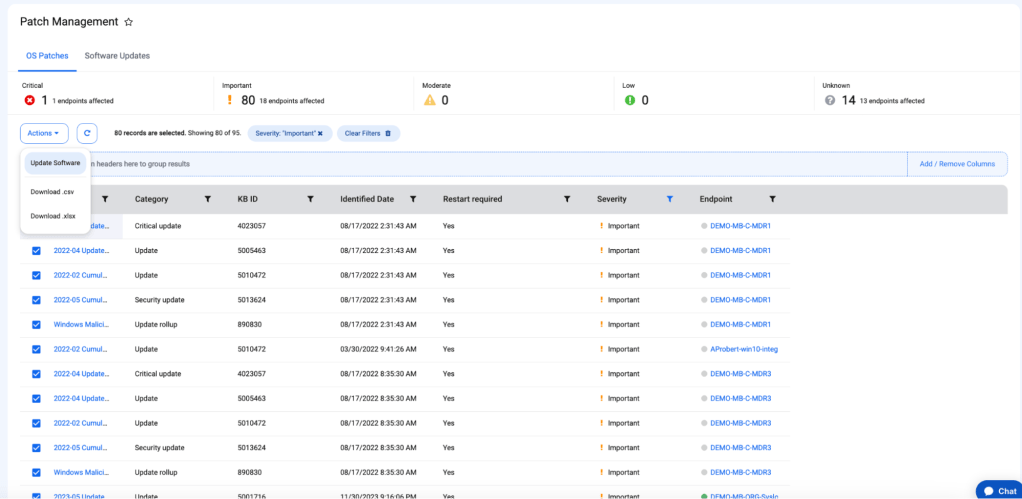
Learn more about our free Vulnerability Assessment solution here.




