
Ransomware review: August 2024
In July there were a total of 424 ransomware victims.
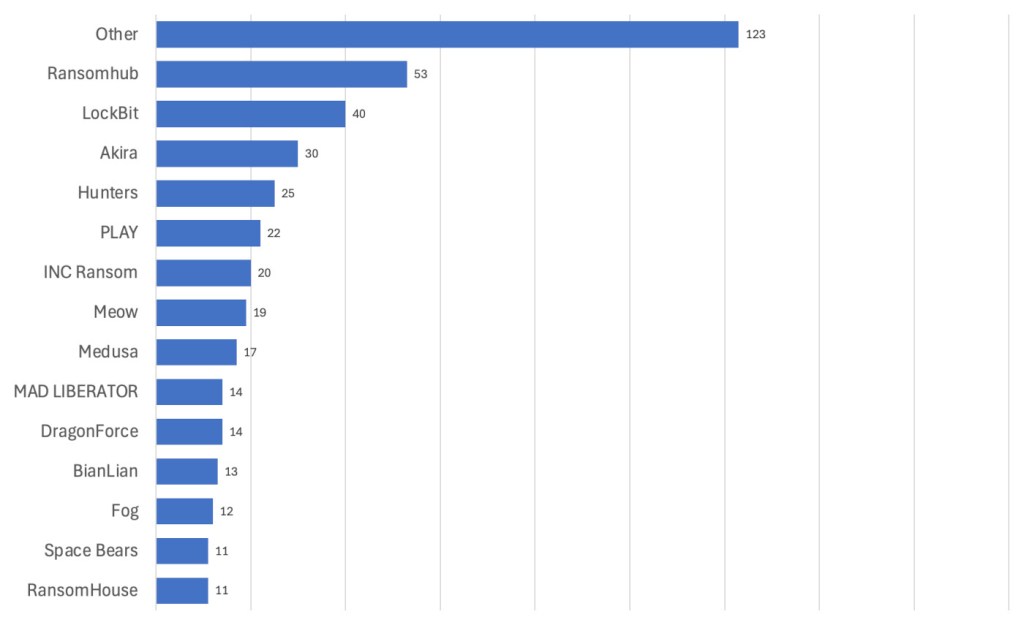
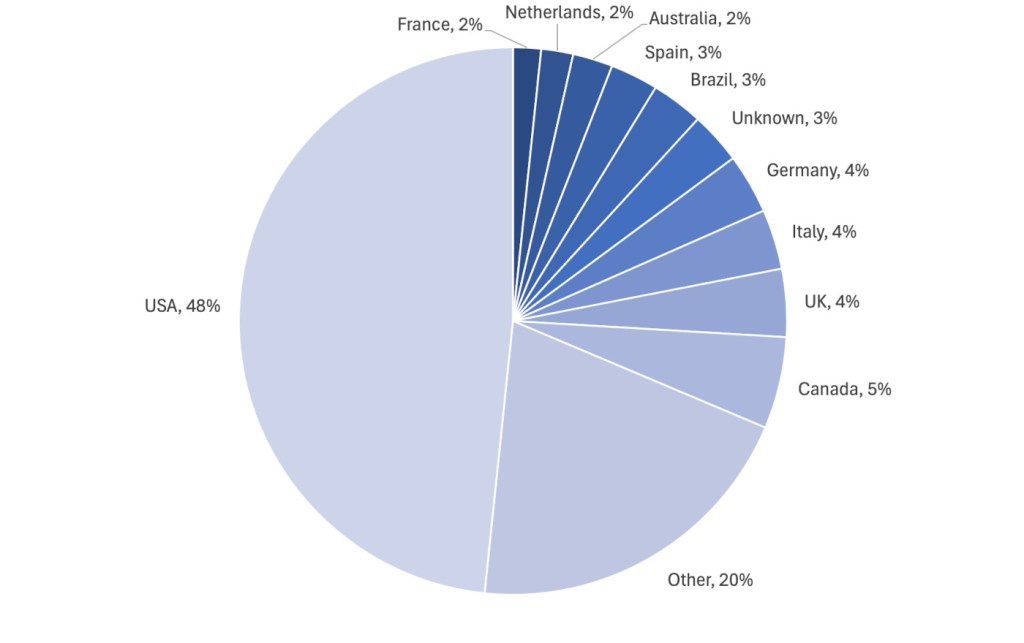
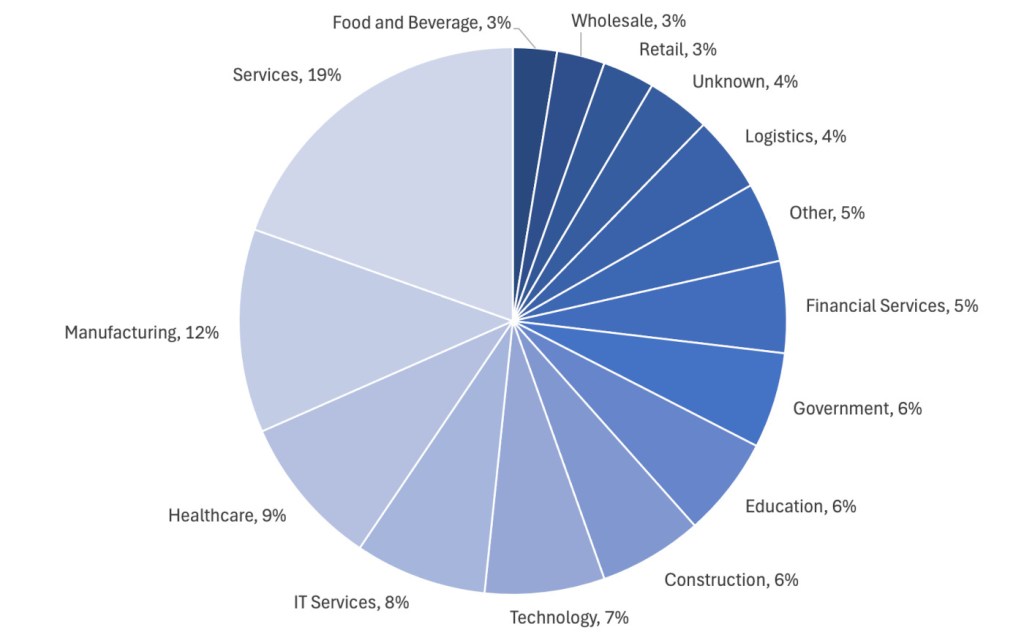
In July, we recorded a total of 424 ransomware victims. The biggest stories of the month included a record-breaking $75 million ransom, more gangs attacking VMware ESXi VMs, and the rise of RansomHub as a top ransomware gang.
A Fortune 50 company paid a record-breaking $75 million ransom to the Dark Angels ransomware group last month. The payment—confirmed by Zscaler ThreatLabz and crypto intelligence firm Chainalysis—surpasses the previous record of $40 million paid by CNA in an Evil Corp attack, making it the highest known ransom ever paid to a ransomware group.
Perhaps the most interesting fact about the historic payment, however, is just how little-known Dark Angels is. By our data, Dark Angels hasn’t published any victims on its leak site since the summer of last year, when it posted just eight. The unsuspecting group proves that, when assessing the danger of a ransomware gang, overall attack volume might matter less than “big game hunting”—targeting high-value companies for massive payouts.
In other news, VMware ESXi ransomware attacks made headlines last month. Whether the news was CISA warning of ESXi bugs being exploited in attacks, a new PLAY ransomware variant targeting ESXi VMs, or the SEXi ransomware gang rebranding to APT INC, each ESXi-Ransomware development points to a concerning trend.
ESXi VMs, which host critical business applications and data, are prime targets for ransomware attacks because they offer a high-impact payoff. Attackers often breach these VMs by exploiting unpatched vulnerabilities or using stolen or weak administrative credentials. Once inside a host network, attackers can also move laterally to compromise ESXi servers.
To help protect against the rising tide of ESXi ransomware attacks, be sure to regularly update and patch systems, enforce strong access controls with multi-factor authentication, and implement continuous monitoring for unusual activity.
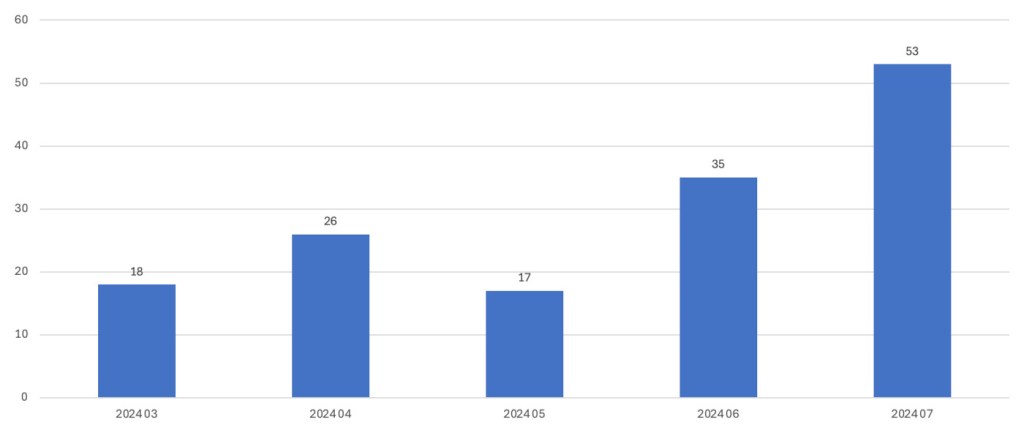
Finally, we think organizations should be paying special attention to the RansomHub gang, whose attacks are increasing each month. As you can see in the chart below, the gang had an all-time-high number of 53 attacks in July, making RansomHub the single-most dominant gang of the month. And, in line with our point about ESXi attack trends, RansomHub is known to target ESXI VMs as well. We recommend blocking the RansomHub IOCs listed in this blog post.
New Gangs
We saw a total of nine new ransomware gangs in July, including:
- Dispossessor
- Blackout
- Fog
- Lynx
- MAD LIBERATOR
- Pryx
- Ransomcortex
- Space Bears
- Vanir Group
How ThreatDown Addresses Ransomware
The Malwarebytes’ ThreatDown product portfolio takes a a comprehensive approach to ransomware attacks. Our integrated solutions combine EP, VPM, and EDR technologies, tailored to your organization’s specific needs, including:
- Advanced Web Protection: Blocking phishing websites ransomware gangs use for initial access.
- RDP Shield: Securing remote access points with Brute Force Protection.
- Continuous Vulnerability Scanning and Patch Management: Identifying and patching weaknesses before ransomware gangs can exploit them.
- Sophisticated EDR: Detecting and neutralizing advanced threats such as LockBit within the network.
- Ransomware Rollback: Reversing the impact of any successful attacks.
For organizations with an in-house team to investigate and respond to suspicious activity around-the-clock, ThreatDown Managed Detection and Response (MDR) services, provide expert monitoring and swift threat response to ransomware threats 24x7X365. Reach out for a quote today.




