
Ransomware review: December 2023
Threat Intelligence Team
Threat Intelligence Team
This article is based on research by Marcelo Rivero, Malwarebytes’ ransomware specialist, who monitors information published by ransomware gangs on their Dark Web sites. In this report, “known attacks” are those where the victim did not pay a ransom. This provides the best overall picture of ransomware activity, but the true number of attacks is far higher.
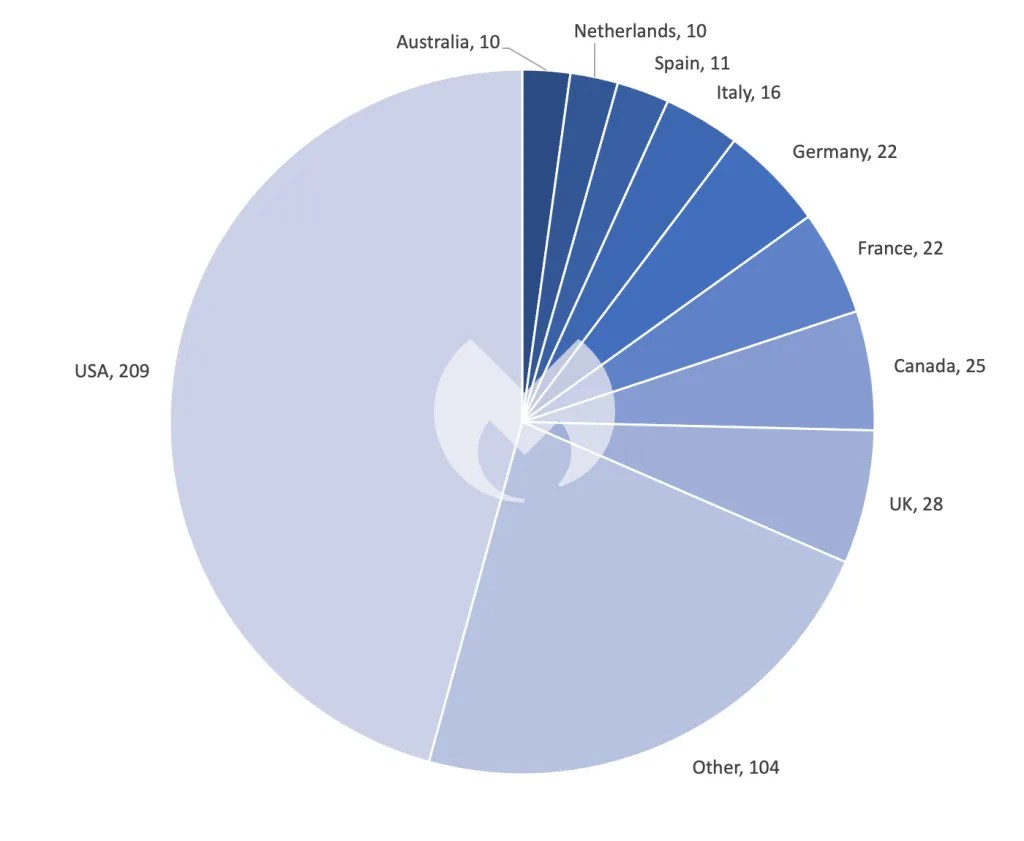
In November there were 457 total ransomware victims, making it the most active month for ransomware gangs in 2023 so far besides May. The top stories of the month include ALPHV’s shutdown (and subsequent return), an increased focus on the healthcare sector, and high-profile attacks on Toyota, Boeing, and more using a Citrix Bleed vulnerability (CVE-2023-4966).
The ALPHV ransomware gang, arguably the second most dangerous “big game” ransomware operator, appears to be back in business after its infrastructure went down for five days in early December. But all does not appear to be going well for group. ALPHV’s dark web leak site may be back but it is only showing a single victim with no sign of any of the hundreds of others it normally lists. The solitary listing on the site is dated December 13, which is after the site was restored.
When the gang’s infrastructure went down a week ago, many suspected the hand of law enforcement, despite no official word on the subject. According to VX Underground, APLHV’s own explanation is that it suffered a hardware failure. If the group really has lost access to the data its business relies on, then it’s now getting a first hand look at what its victims go through when they’re attacked and their data is encrypted.
However, while it’s perfectly plausible that ALPHV is suffering hardware woes, law enforcement action can’t be ruled out. ALPHV would likely lose affiliates if it admitted to a brush with the law, so the ransomware gang is likely going to attribute the outage to something benign—whether that is true or not. Equally, the silence from the FBI could mean everything and nothing. In January, the agency took down one of ALPHV’s contemporaries, Hive, and revealed it had penetrated the group’s infrastructure six months prior.
Whether ALPHV’s troubles are caused by tight-lipped law enforcement, an ironic lack of disaster recovery planning, or some other sleight of hand, any disruption to the ransomware ecosystem is a welcome early Christmas present in our book.
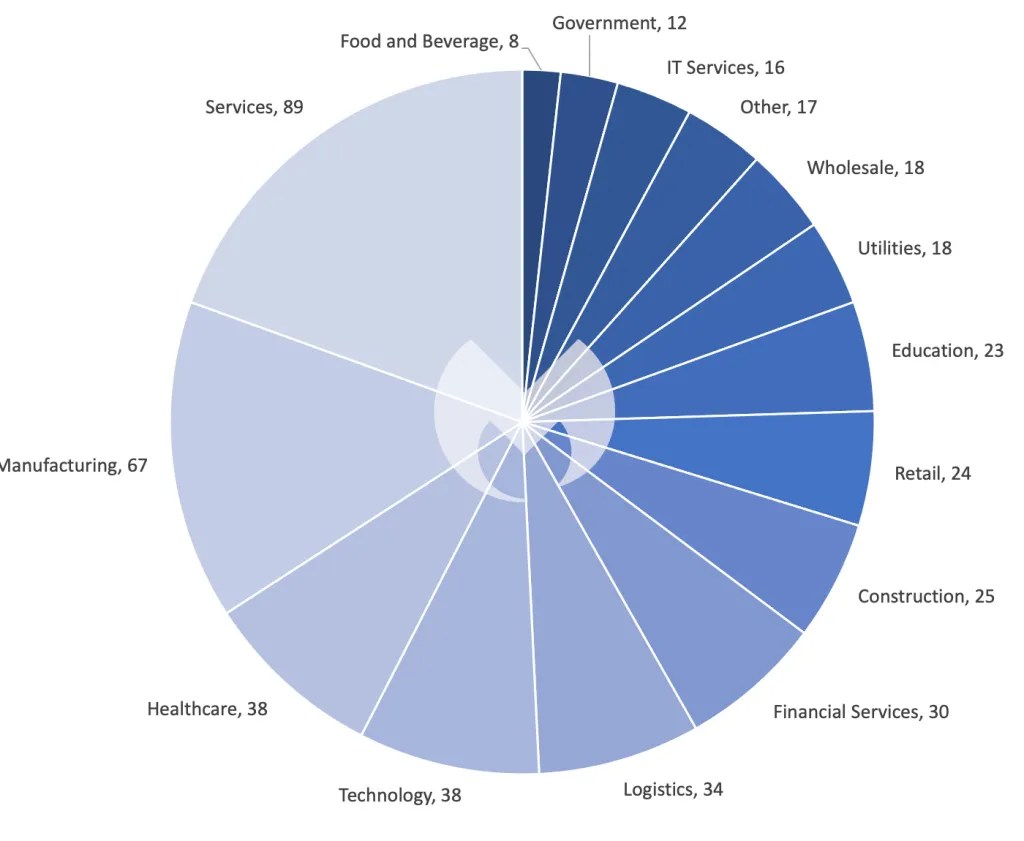
In other news, attacks on the healthcare sector last month reached an all-time high at 38 total attacks.
The record follows a steady uptick in attacks on the sector we’ve observed over the past year. According to the findings released by the Department of Health and Human Services last month, there has been a 278% increase in ransomware attacks on health sector over the past four years. “The large breaches reported this year have affected over 88 million individuals, a 60% increase from last year,” the agency also said.

Ransomware attacks on healthcare, 03/22 to 011/23
An attack on Ardent Health Services last month stands as a devastating reification of the trend. The attack, which occurred on Thanksgiving Day, left emergency rooms in multiple hospitals across four US states shut down for five days.
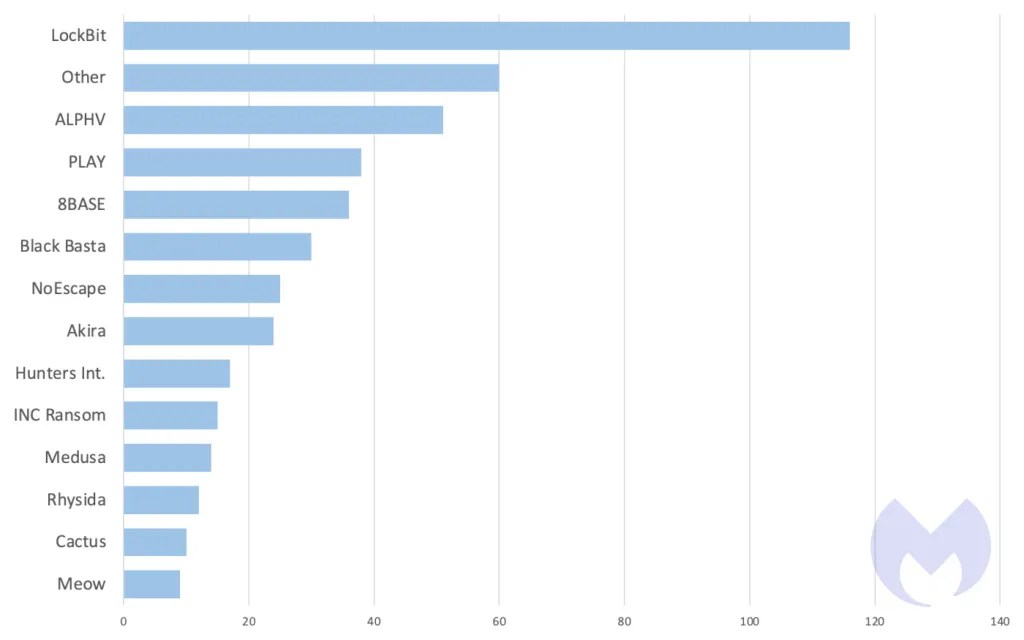
What explains the rise and focus on attacks on the healthcare sector? Well, for one thing, there isn’t a clear bias of one gang disproportionately targeting health care—our data shows LockBit is consistently at the top of the list, as they are likely for most sectors. The explanation, then, likely resides in a combination of facts:
- Ransomware attacks are up overall for all sectors
- Healthcare is easy to attack (Large number of weak points due to use of legacy systems, third-party vendors, etc).
- Healthcare might be more likely to pay (Higher desire to protect sensitive patient data).
Pair this up with a Thanksgiving holiday, and a bigger increase in attacks on health care is somewhat expected.
In other news, ransomware gangs rushed to exploit the Citrix Bleed vulnerability last month, taking advantage of a massive attack surface with over 8,300 vulnerable devices. LockBit led the fray by using the vulnerability to breach the likes of the Industrial and Commercial Bank of China (ICBC), DP World, Allen & Overy, and Boeing. Reported to have been in use as a zero-day since late August, Citrix Bleed provides attackers with the capability to bypass multi-factor authentication (MFA) and hijack legitimate user sessions. It is also said to be very easy to exploit.
One of the most interesting developments last month were new reports reinforcing claims that Rhysida may be a rebrand of the infamous Vice Society ransomware gang. Not only does Rhysida share many operational and technical patterns with Vice Society—including using NTDSUtil for backups in ‘temp_l0gs’ and SystemBC for C2 communications—but the distribution of their monthly attacks lines up as well. Vice Society hasn’t been active since June 2023—the same month we witnessed the rise of Rhysida.

Vice Society vs Rhysidia monthly ransomware attacks. Rhysida seems to pick up right where Vice Society dropped off
That being said, a rebrand isn’t confirmed. Perhaps Rhysida is a splinter group. Whatever the explanation, however, it’s almost certain this pattern is no mere coincidence—especially considering the victimology of the two groups is extremely similar (a focus on education and healthcare sectors).
New Player: MEOW
First detected in August 2022, Meow ransomware, linked to the Conti v2 variant, reappeared after vanishing in February 2023. The group published nine victims to its leak site in November.
Operating as MeowCorp or MeowCorp2022, it encrypts files with a “.MEOW” extension and sends ransom notes demanding contact via email or Telegram. Using ChaCha20 and RSA-4096 encryption, Meow is related to other malware strains originating from the leaked Conti variant. Its dark web site shows a limited victim list, including the high-profile entity Sloan Kettering Cancer Center.
Preventing Ransomware
Fighting off ransomware gangs like the ones we report on each month requires a layered security strategy. Technology that preemptively keeps gangs out of your systems is great—but it’s not enough.
Ransomware attackers target the easiest entry points: an example chain might be that they first try phishing emails, then open RDP ports, and if those are secured, they’ll exploit unpatched vulnerabilities. Multi-layered security is about making infiltration progressively harder and detecting those who do get through.
Technologies like Endpoint Protection (EP) and Vulnerability and Patch Management (VPM) are vital first defenses, reducing breach likelihood.
The key point, though, is to assume that motivated gangs will eventually breach defenses. Endpoint Detection and Response (EDR) is crucial for finding and removing threats before damage occurs. And if a breach does happen—ransomware rollback tools can undo changes.
How ThreatDown Addresses Ransomware
ThreatDown bundles take a comprehensive approach to these challenges. Our integrated solutions combine EP, VPM, and EDR technologies, tailored to your organization’s specific needs. ThreatDown’s select bundles offer:
- Advanced Web Protection: Blocking phishing websites ransomware gangs use for initial access.
- RDP Shield: Securing remote access points with Brute Force Protection.
- Continuous Vulnerability Scanning and Patch Management: Identifying and patching weaknesses before ransomware gangs can exploit them.
- Sophisticated EDR: Detecting and neutralizing advanced threats such as LockBit within the network.
- Ransomware Rollback: Reversing the impact of any successful attacks.
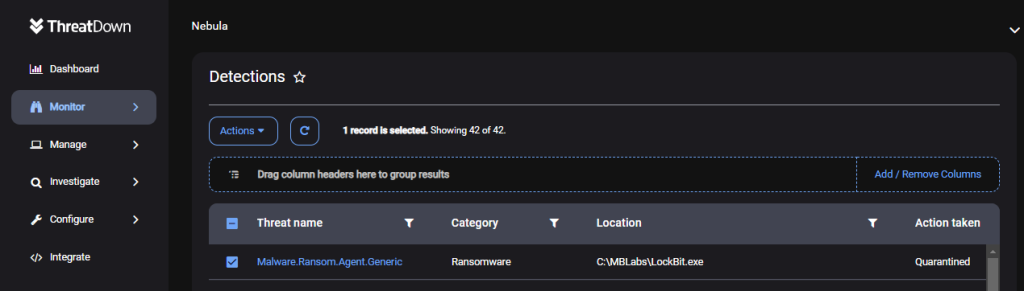
ThreatDown EDR detecting LockBit ransomware
ThreatDown automatically quarantining LockBit ransomware




