Ransomware review: July 2024
In June, LockBit said it breached the Federal Reserve and Black Basta was seen exploiting a Windows zero-day.
This article is based on research by Marcelo Rivero, Malwarebytes’ ransomware specialist, who monitors information published by ransomware gangs on their Dark Web sites. In this report, “known attacks” are those where the victim did not pay a ransom. This provides the best overall picture of ransomware activity, but the true number of attacks is far higher.
In June, a total of 358 victims were posted on ransomware leak sites, the second lowest all year. The biggest stories of the month included LockBit’s fraudulent attack on the Federal Reserve, the rise of ‘The Hateful Eight’ ransomware gangs, and a string of newly-exploited vulnerabilities, including a Windows zero-day. The ThreatDown MDR team also released two blog posts about attacks using Akira and LockBit, respectively.
After an all-time-high number of attacks in May, LockBit posted an all-time-low-number of just 12 victims on its leak site last month—one of which was supposedly the US Federal Reserve. While the post caused much buzz throughout the cybersecurity world, few actually believed that the claim was real, especially given LockBit’s increasingly erratic behavior in the wake of Operation Cronos. On June 25th, the group’s countdown to publishing the Federal Reserve’s data hit zero, and lo and behold, zilch: the data posted actually belonged to an Arkansas-based bank named Evolve.
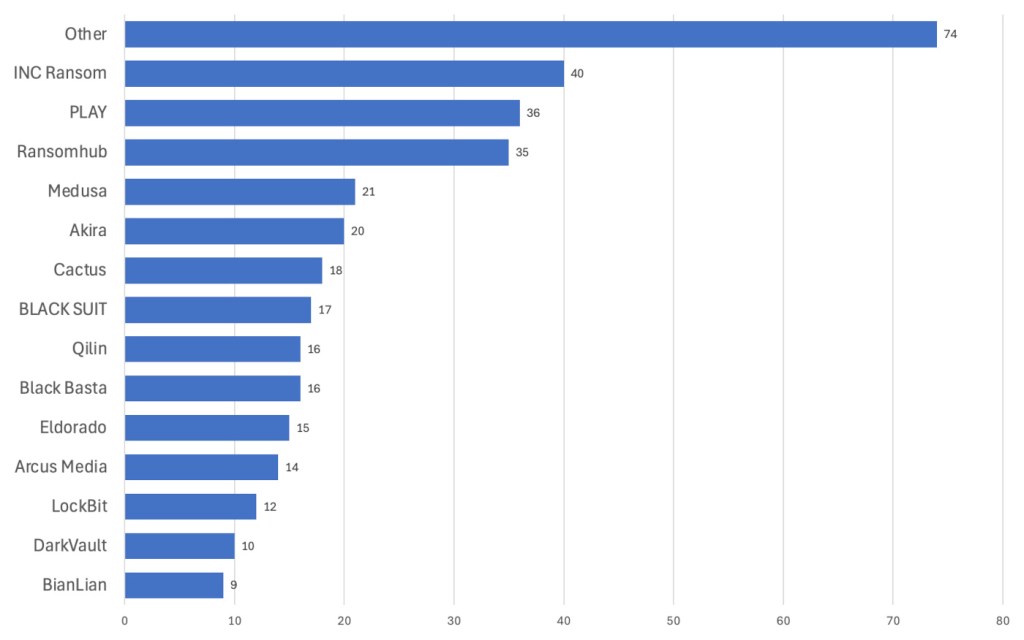
It’s a sign of how far LockBit has fallen that it’s resorting to such desperate publicity stunts, and proclaiming its unreliability to the world. The arrest of prominent LockBit leader and spokesperson LockBitSupp in May might have pushed whoever remains over the edge.
‘The Hateful Eight’
While just about every ransomware gang has poached some of LockBit’s affiliates in the months following operation Cronos, eight gangs have boomed in the months since, perhaps from picking up affiliates from both LockBit and the now defunct ALPHV group.
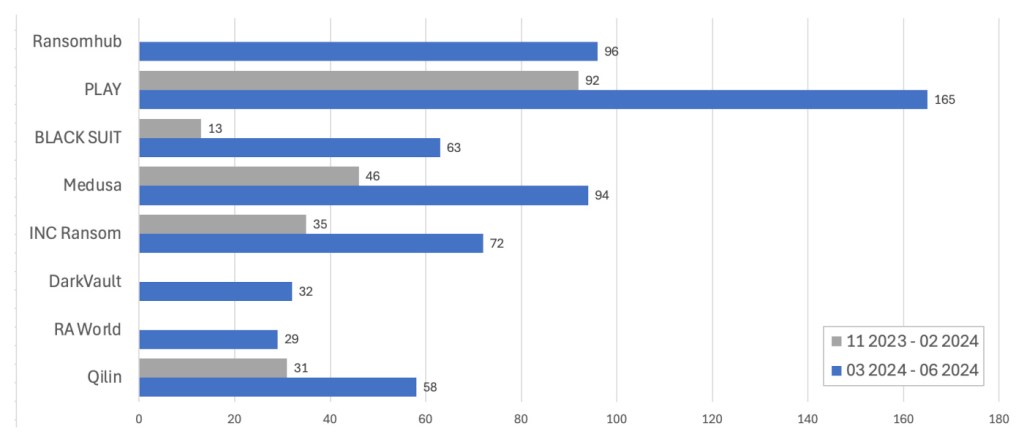
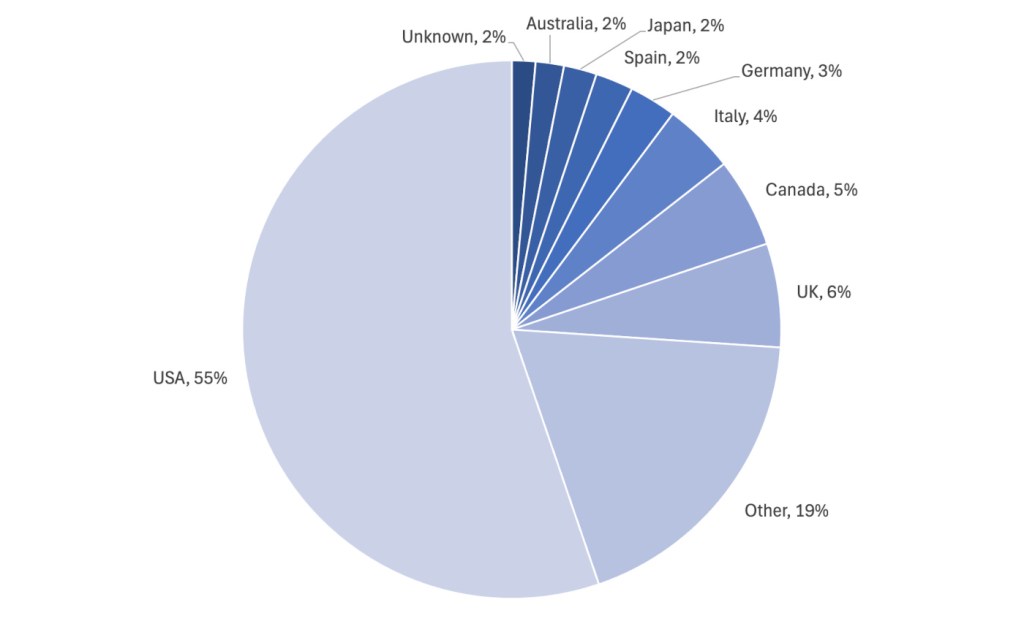
Attacks by industry and country

‘De facto’ zero-days
At the rate in which ransomware gangs exploit new vulnerabilities every month, we might just have to start adding a dedicated section to the topic in our recaps going forward. After all, ransomware gangs exploited more zero-days in 2023 than ever before, and so far in 2024 they aren’t slowing down.
Case in point: last month, the Black Basta ransomware operation was suspected of exploiting a Windows privilege escalation vulnerability (CVE-2024-26169) before a fix was available. Even without zero-days, attackers are acting quickly enough to create the same urgency. For instance, TellYouThePass began exploiting the recently patched CVE-2024-4577 less than 48 hours after PHP’s maintainers released security updates.
With ransomware gangs not only increasing their use of zero-days but also exploiting known vulnerabilities on near-zero-day timelines, organizations should focus their defenses on extensive monitoring to detect and respond swiftly to breaches.
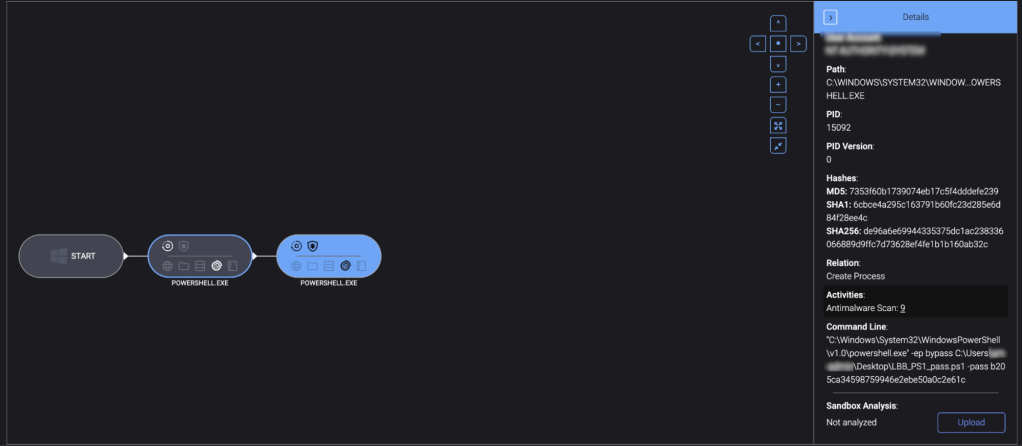
Bonus: The Anatomy of a LockBit and Akira Attacks
Recently, a ThreatDown MDR client suffered an Akira ransomware attack. The incident involved sophisticated infiltration tactics, resulting in significant data encryption and operational disruption; however, the ThreatDown MDR team swiftly intervened to help the client recover from the attack. You can dive into the details here.
Also in June, the ThreatDown MDR team stopped a LockBit ransomware attack in its early stages—but not without first tackling a series of Living off the Land (LOTL) techniques used by the attacker. Take a look at a real incident response case where LockBit extensively used LOTL techniques for evasion, lateral movement, and attempted payload delivery on a ThreatDown MDR client.
New ransomware gangs
Cicada3301
Cicada3301 is a new ransomware gang that published the data of 4 victims on its leak site in June.
SenSayQ
SenSayQ is a new ransomware gang that published the data of 2 victims on its leak site in June.
Trinity
Trinity is a new ransomware gang that published the data of 3 victims on its leak site in June.
ElDorado
ElDorado is a new ransomware gang that published the data of 15 victims on its leak site in June. It is a Go-based ransomware that can encrypt both Windows and Linux platforms, including VMware ESXi VMs.
How to avoid ransomware
- Block common forms of entry. Create a plan for patching vulnerabilities in internet-facing systems quickly; and disable or harden remote access like RDP and VPNs.
- Prevent intrusions. Stop threats early before they can even infiltrate or infect your endpoints. Use endpoint security software that can prevent exploits and malware used to deliver ransomware.
- Detect intrusions. Make it harder for intruders to operate inside your organization by segmenting networks and assigning access rights prudently. Use EDR or MDR to detect unusual activity before an attack occurs.
- Stop malicious encryption. Deploy Endpoint Detection and Response software like ThreatDown EDR that uses multiple different detection techniques to identify ransomware, and ransomware rollback to restore damaged system files.
- Create offsite, offline backups. Keep backups offsite and offline, beyond the reach of attackers. Test them regularly to make sure you can restore essential business functions swiftly.
- Don’t get attacked twice. Once you’ve isolated the outbreak and stopped the first attack, you must remove every trace of the attackers, their malware, their tools, and their methods of entry, to avoid being attacked again.
Detecting ransomware attacks with ThreatDown Managed Detection and Response (MDR)
ThreatDown MDR analysts are experienced in detecting threats early and blocking ransomware attackers before it’s too late. Read more on how the ThreatDown MDR team successfully stopped a Medusa ransomware attack.