Ransomware review: October 2024
Attacks by ‘dark horse’ ransomware groups are up 63%.
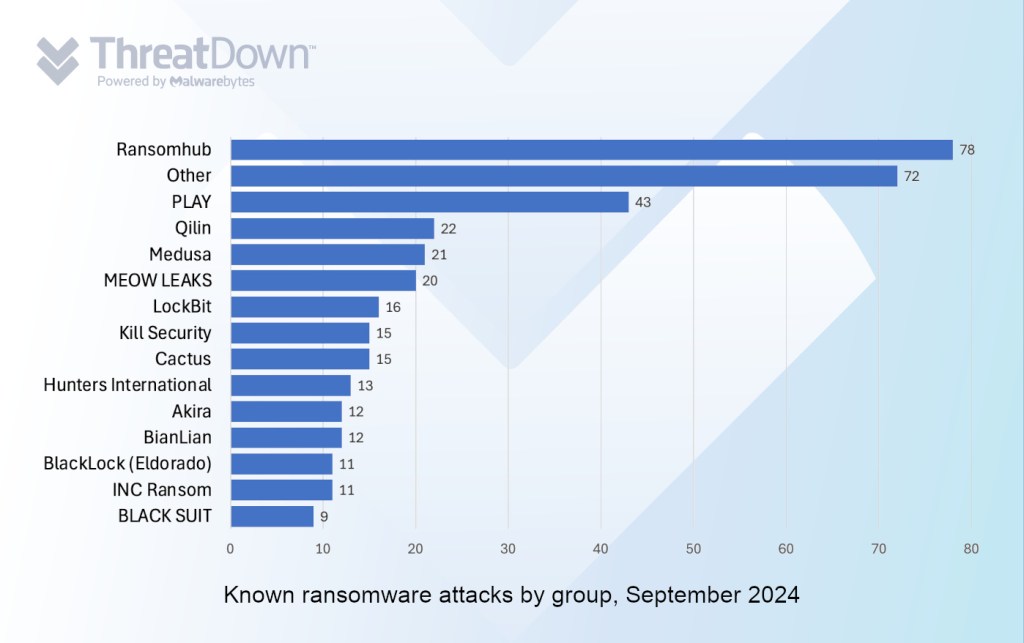
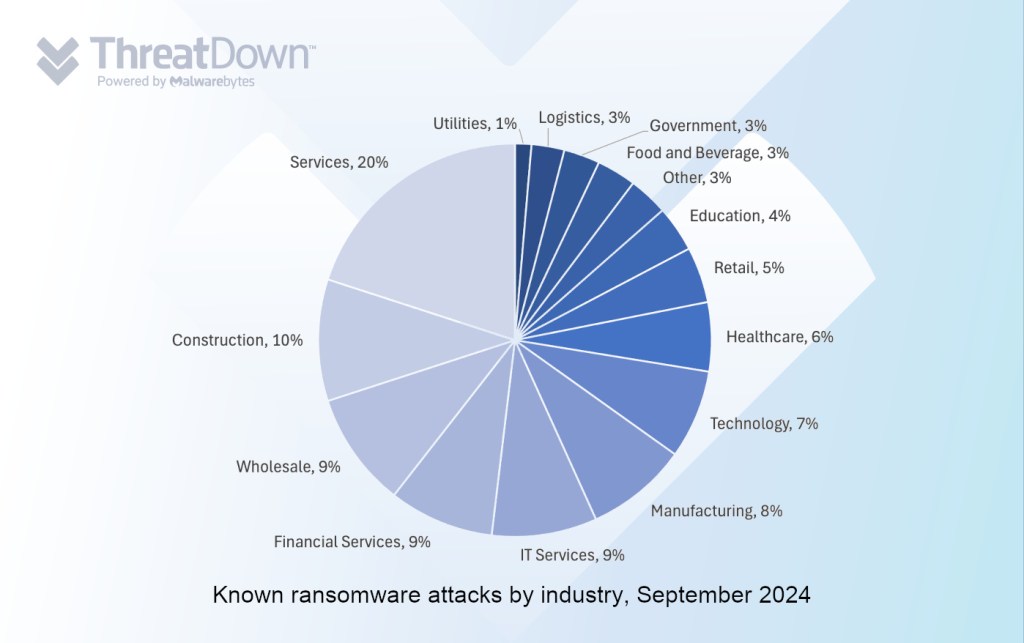
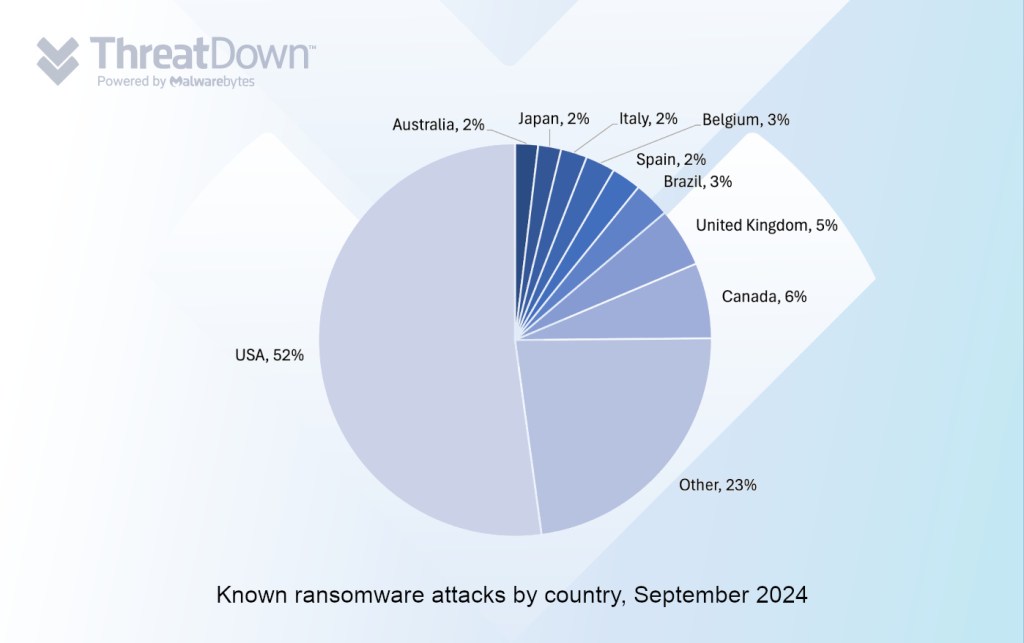
In September, we recorded a total of 370 ransomware victims, the third lowest all year. The biggest news of the month included ransomware gangs using new tools for data theft, the rise of “hybrid cloud” ransomware, and a 63% increase in attacks by ‘dark horse’ ransomware year-over-year.
First up, recent research by modePUSH showed BianLian and Rhysida using new tools for data exfiltration.
Specifically, the two groups have been observed using Azure Storage Explorer and AzCopy to steal sensitive data by transferring large volumes of files to cloud storage.
Typically, ransomware gangs have relied on tools like MEGAsync, Rclone, and FileZilla for data exfiltration. What makes Azure Storage Explorer different, however, is that it is a native Microsoft tool specifically designed to manage Azure storage. Since many organizations use Azure services legitimately, network security controls may be more lenient in allowing outbound traffic to trusted Microsoft IP addresses.
For defenders, this poses a unique challenge. Blocking tools like Azure Storage Explorer or AzCopy could disrupt legitimate cloud management tasks, as many businesses rely on these tools for daily operations. If you can’t outright ban them (like you should do with some other tools), focus on monitoring network traffic to Azure IP addresses for suspicious transfers.
In other news, Microsoft reported how Storm-0501, a ransomware affiliate, broke into cloud environments by exploiting stolen Microsoft Entra ID (formerly Azure AD) credentials. They started by targeting on-premises servers, specifically Microsoft Entra Connect Sync, which links on-premises systems to the cloud by synchronizing user credentials. This allowed the attackers to move seamlessly between on-premises and cloud environments using the same stolen passwords.
Storm-0501 used Impacket, an open-source toolkit commonly employed in penetration testing but favored by attackers for credential theft and lateral movement. In this case, the group used it to steal DPAPI (Data Protection API) encryption keys, which protect stored passwords. With these keys, they were able to extract plain text credentials from the server, gaining control of Microsoft Entra Connect Sync and both the on-premises and cloud environments.
Interestingly, Microsoft noted that Storm-0501 didn’t always deploy ransomware immediately, as it did in this case with Embargo ransomware. In some instances, they only set up a backdoor to maintain long-term control of the network without encrypting files. This tactic allowed them to stay hidden for future exploitation.
Lastly, our own research into ransomware data reveals just how much law enforcement action against LockBit (Operation Cronos) and the exit scam by ALPHV have shaken up the broader ransomware landscape.
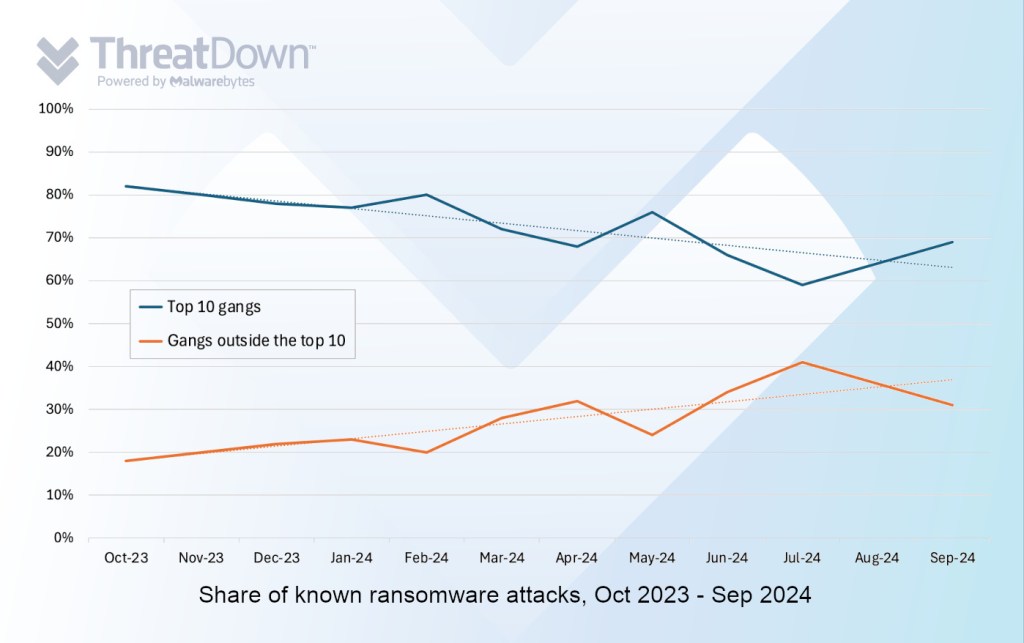
From October 2023 through September 2024, there was a 63% increase in the total number of known attacks outside the top ten ransomware gangs (‘dark horse’ groups) when comparing the first six months to the last six months. During the same period, total known attacks within the top ten ransomware gangs actually decreased by 6%.
In the first half of this period, the share of total known ransomware attacks done by the ‘dark horse’ groups was 20%, compared to 80% for the top ten. In the second half, the share of total known ransomware attacks done by the ‘dark horse’ groups was 30%, compared to 70% for the top ten.
Put another way, the share of total known ransomware attacks by ‘dark horse’ groups is increasing each month. At the same time as the top 10 share is shrinking.
New player: Orca
Orca is a new ransomware gang that published two victims on its leak site last month.
How to avoid ransomware
- Block common forms of entry. Create a plan for patching vulnerabilities in internet-facing systems quickly; and disable or harden remote access like RDP and VPNs.
- Prevent intrusions. Stop threats early before they can even infiltrate or infect your endpoints. Use endpoint security software that can prevent exploits and malware used to deliver ransomware.
- Detect intrusions. Make it harder for intruders to operate inside your organization by segmenting networks and assigning access rights prudently. Use EDR or MDR to detect unusual activity before an attack occurs.
- Stop malicious encryption. Deploy Endpoint Detection and Response software like ThreatDown EDR that uses multiple different detection techniques to identify ransomware, and ransomware rollback to restore damaged system files.
- Create offsite, offline backups. Keep backups offsite and offline, beyond the reach of attackers. Test them regularly to make sure you can restore essential business functions swiftly.
- Don’t get attacked twice. Once you’ve isolated the outbreak and stopped the first attack, you must remove every trace of the attackers, their malware, their tools, and their methods of entry, to avoid being attacked again.