
Ransomware review: September 2024
In August, we recorded a total of 442 ransomware victims, the second-most all year.
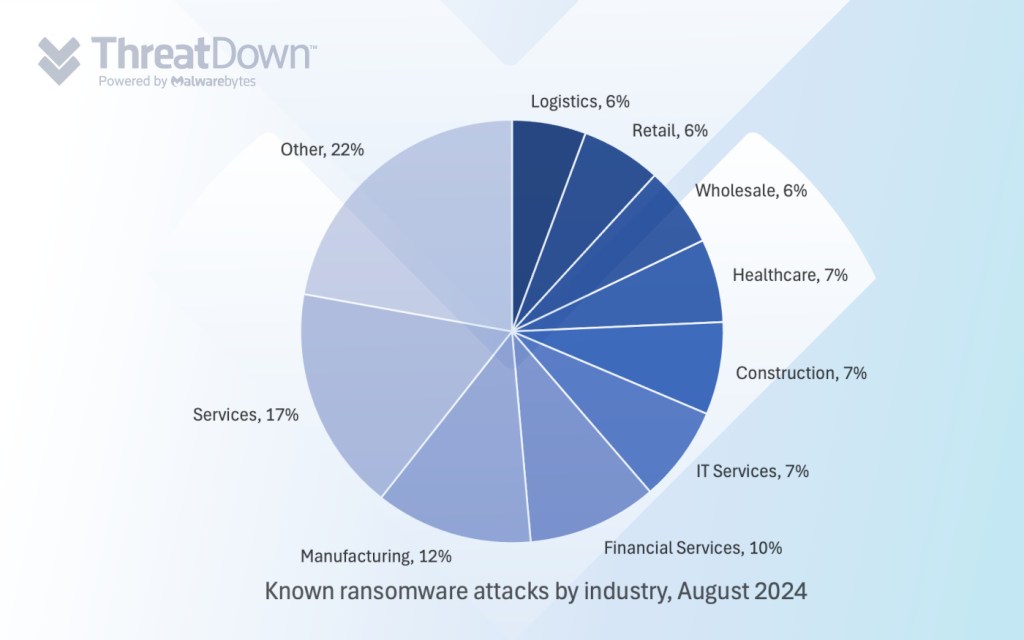
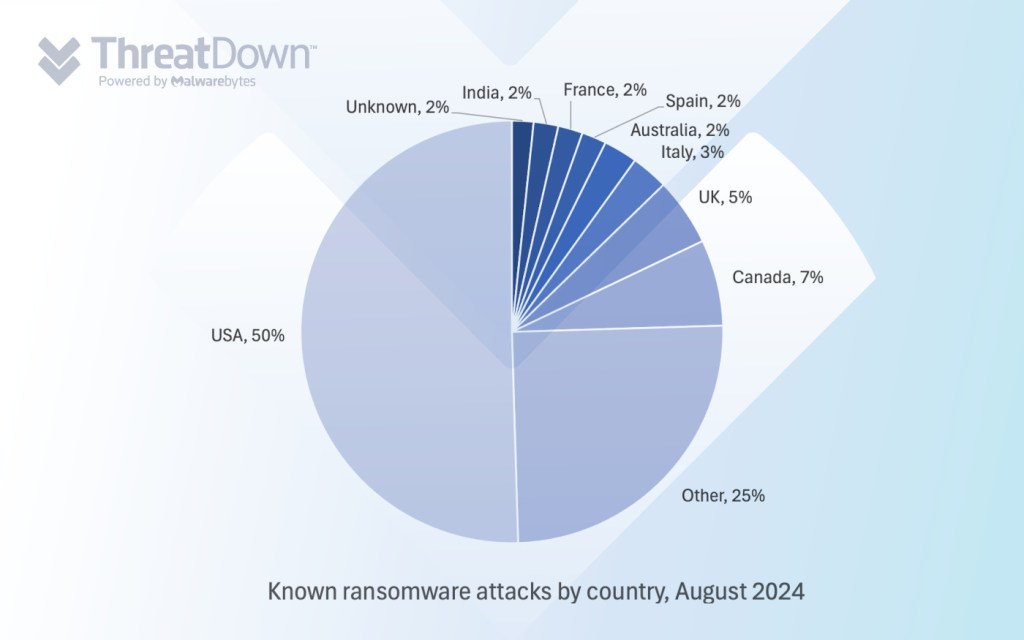
In August, we recorded a total of 442 ransomware victims, the second-most all year after May. The biggest news of the month included ransom payments surging to a record-breaking $450 million in the first half of 2024, the sudden resurgence of the Meow ransomware gang, and reports of RansomHub using multiple different EDR killers in its attacks.
Data from Chainalysis last month revealed that overall ransomware payments are up approximately 2% over the first half of 2024, from $449.1 million to $459.8 million. At the same time, median payments from “very high severity strains” are up 650%—from $200,000 in early 2023 to $1.5 million in mid-June 2024, signaling a consistent increase in payouts across all attacks. The surge in median payment amount is likely due to attackers targeting larger organizations with deeper pockets.
The good news? Fewer victims are paying than before, down 27% year-over-year, even though ransomware attacks are up 10% year-over-year.
The decline in the number of people paying, despite the increase in attacks, indicates that many organizations are becoming better equipped to handle ransomware incidents—whether through better backups, more robust defenses, or simply refusing to negotiate with attackers, which is always a welcome development.
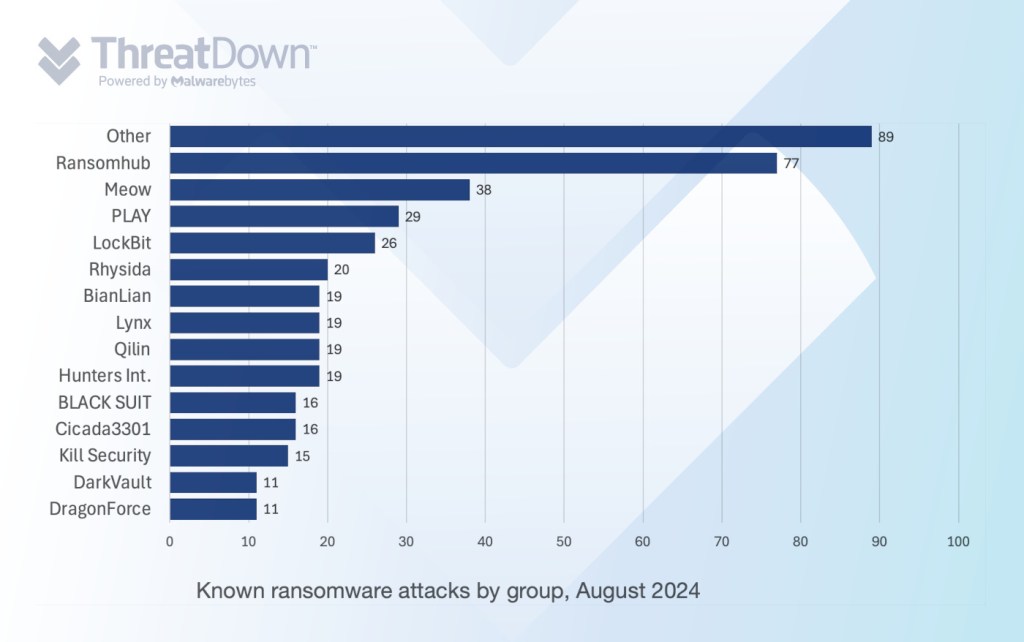
The Meow ransomware gang posted 34 victims on its leak site last month, which is more than their last 12 months combined. Meow, who we first reported on in late 2023, is built off the leaked Conti ransomware code. Their spike in activity reinforces the trend of smaller ransomware gangs stepping up after the fading of heavyweights like LockBit and ALPHV.
Most interesting about the group, however, is its stark departure from its previous hit list: Whereas before it mainly attacked Russian organizations, it’s now turned its attention to US institutions. Perhaps with the disruptions of major ransomware players that dominated attacks on US organizations, the US may now present a more competitive and lucrative target for smaller groups like Meow.
In other news, there was a spurt of information about RansomHub using EDR killers last month.
In August, RansomHub was caught using EDRKillShifter, a tool designed to disable EDR software. Similar to other EDR-killing tools like AuKill and Terminator, EDRKillShifter is designed to disable endpoint detection and response (EDR) software by exploiting vulnerable drivers, commonly referred to as BYOVD (Bring Your Own Vulnerable Driver) attacks. The tool acts as a loader, delivering legitimate yet vulnerable drivers that attackers can abuse to shut down security defenses on compromised hosts.
In early September, the ThreatDown MDR team was the first to report on RansomHub using TDSSKiller, a legitimate tool from Kaspersky, to attack endpoint agents.
Since these tools operate at the kernel level, they have deep access to the core of the operating system. The takeaway? Limit kernel access—often exploited through vulnerable drivers—by enforcing the principle of least privilege and restricting driver execution. It’s also crucial to lock down driver access, monitor for suspicious activity, and segment networks to contain any potential breaches.
New player: Helldown
Helldown is a new ransomware gang that published 17 victims on its leak site last month.
How to avoid ransomware
- Block common forms of entry. Create a plan for patching vulnerabilities in internet-facing systems quickly; and disable or harden remote access like RDP and VPNs.
- Prevent intrusions. Stop threats early before they can even infiltrate or infect your endpoints. Use endpoint security software that can prevent exploits and malware used to deliver ransomware.
- Detect intrusions. Make it harder for intruders to operate inside your organization by segmenting networks and assigning access rights prudently. Use EDR or MDR to detect unusual activity before an attack occurs.
- Stop malicious encryption. Deploy Endpoint Detection and Response software like ThreatDown EDR that uses multiple different detection techniques to identify ransomware, and ransomware rollback to restore damaged system files.
- Create offsite, offline backups. Keep backups offsite and offline, beyond the reach of attackers. Test them regularly to make sure you can restore essential business functions swiftly.
- Don’t get attacked twice. Once you’ve isolated the outbreak and stopped the first attack, you must remove every trace of the attackers, their malware, their tools, and their methods of entry, to avoid being attacked again.



