
Rise of Atomic Stealer signals a sea change in macOS malware
Atomic Stealer is the most popular malware-as-a-service on macOS because of highly active affiliate-driven distribution campaigns and constant feature upgrades.
A new version of the Atomic Stealer (AMOS) malware is now circulating in the wild, and it has the popular new Arc browser in its sights. AMOS stealer is a relatively new and very active malware-as-a-service specifically for macOS that first appeared in April 2023. Since then, it has seen regular updates, and been distributed in numerous different campaigns.
AMOS makes money for its operators by finding and stealing valuable information on the computers it infects, such as credit card details, authentication cookies, passwords and cryptocurrency. Although it doesn’t discriminate between computers on home or corporate networks, AMOS’s appetite for passwords and authentication cookies should be of serious concern to organisations using Macs, because cybercriminal gangs pay for credentials they can use to breach company networks.
The latest version of AMOS has added a number of features that put Mac users at greater risk. The new features were announced on Telegram, and verified by ThreatDown’s engineers using samples found in the wild.
The latest iteration of AMOS adds Wasabi and Ledger Live to the list of wallets it can target. If it finds the Ledger Live app on an infected computer, it replaces it with a fake version that can steal seed phrases—which can be used to regenerate an entire wallet (and all the funds stored inside it). It now also searches computers for Monero, a type of cryptocurrency that’s easier to mine than some more well known currencies, like Bitcoin or Ethereum.
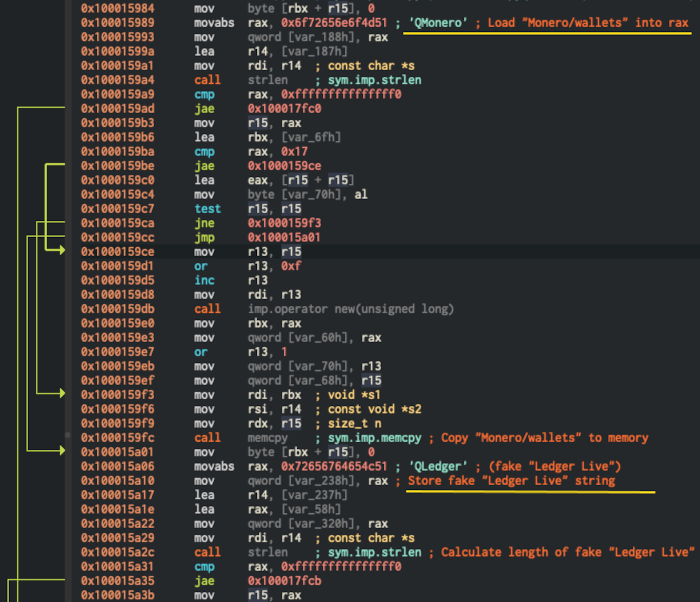
The web browsers installed on an infected computer are a prime target for Atomic Stealer too, because of the array of sensitive data they can store, including credit card details, passwords, personal information used to autofill forms, and authentication cookies.
Prior to the latest version, AMOS already included code to steal from most popular browsers, but it has now added Chrome Canary, an experimental early-release version of the Chrome browser, and Arc, a new browser that’s attracted lots of positive attention from press and technologists, to its list of targets. Neither browser has much market share, but AMOS already knows how to target the browsers that do, and it’s not difficult to imagine that Chrome Canary and Arc are popular with people who keep cryptocurrency.
As well as stealing data from the web browsers themselves, AMOS can also steal data from browser extensions (plugins), and boasts that it now targets more than 100.
A new problem for Macs
One of the curious things about malware, is that different threats proliferate on different platforms. iPhones, Androids, Windows desktops, Mac laptops, Linux servers, and all the other devices and operating systems that make up the computing ecosystem occupy different niches, and criminals have learned that different threats make money on different platforms.
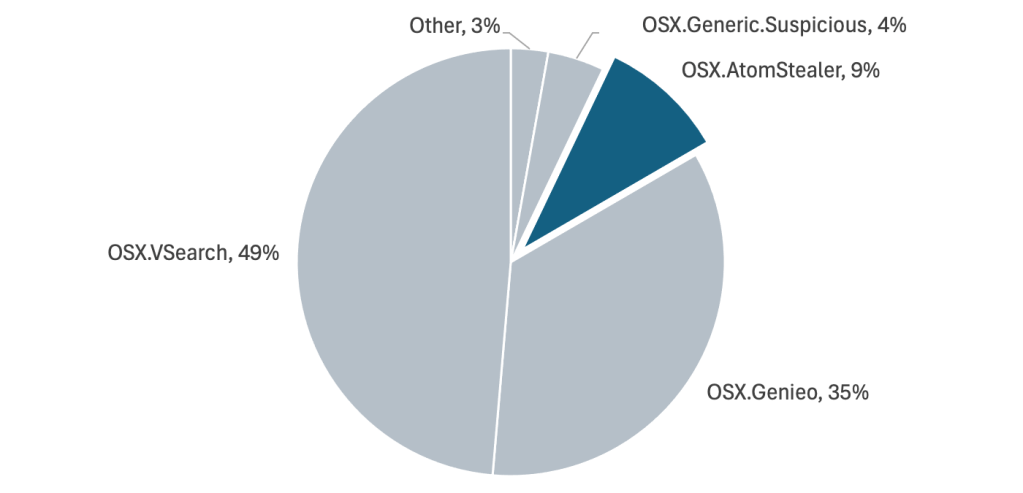
For many years, the most prevalent malware on Macs has been VSearch adware, or the browser hijacker Genieo, and the received wisdom was that these were the types of threats that made money on the platform. However, Atomic Stealer is now challenging that view, and in little over a year has risen to become the third most detected malware on Macs, accounting for 9% of macOS malware detections in 2024.
With hindsight, perhaps it shouldn’t be a surprise that Atomic Stealer arrived when it did. Macs are no longer niche machines. Demand for Macs has grown despite declining PC sales, and Apple’s macOS, in its many forms, now represents a 26% share of US desktop operating systems, while a quarter of businesses run Macs at least somewhere on their networks.
Alongside Apple’s robust laptop sales, 2023 also saw a resurgence in malware distribution channels that mesh well with malware-as-a-service like AMOS—malvertising and fake browser updates. In malvertising attacks, cybercriminals make Google or Bing search ads for popular software products, and link to replica websites where unwitting users download malware instead of the software they were searching for.
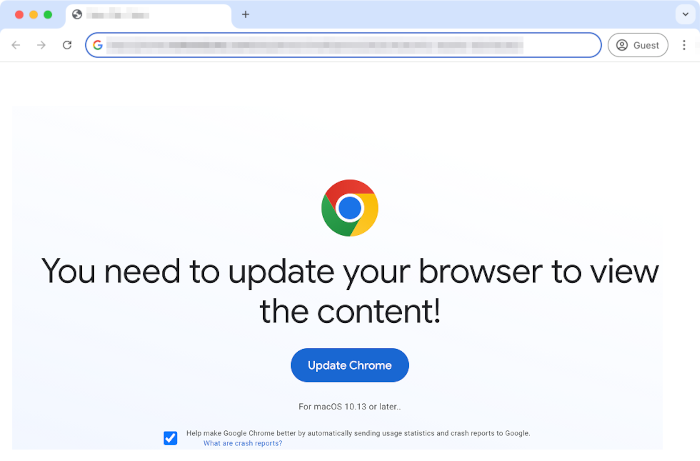
Fake browser updates also use the web to spread, but instead of criminals spinning up their own websites, they hijack existing sites and use them to launch popup windows masquerading as security updates for whatever browser a visitor is using. Instead of a browser update, victims who hit the download button get malware.
In both cases, the hard work in creating the campaigns is setting up back end infrastructure. With that infrastructure in place for spreading Windows malware, it was likely a small lift for criminals to create Mac malware campaigns as well. Atomic Stealer, which is offered for sale as a service at $3,000 a month, appears to have been a beneficiary of the new distribution channels.
Whatever the root cause, Marcelo Rivero, Senior Malware Research Engineer for ThreatDown’s Mac protection, thinks we are seeing a sea change in Mac malware.
Until recently, macOS threats were mostly adware and cryptominers, with ransomware never really taking off. The rise of new stealers like AMOS has shifted the threat landscape.
The increase in detections, the regular addition of new features, and the range of different tactics used to spread it, all suggest that Atomic Stealer malware has found a successful new business model for targeting Mac users.
Rivero:
Atomic Stealer has become the most persistent and fast-evolving macOS stealer, with highly active affiliate-driven distribution campaigns and constant feature upgrades, making it the most popular malware-as-a-service on macOS right now.
ThreatDown malware researchers are tracking Atomic Stealer closely, and all ThreatDown bundles include protection for Macs.




