
Upgrade now! Critical Fortra FileCatalyst Workflow vulnerability needs your attention
An SQL injection vulnerability in Forta’s FileCatalyst Workflow has a CVSS score of 9.8 and a working proof-of-concept exploit.
Fortra has released an upgrade to patch a vulnerability with a CVSS score of 9.8 out of 10 in its FileCatalyst Workflow portal, for which a published proof-of-concept (PoC) exploit exists.
Fortra describes FileCatalyst Workflow as a web portal that simplifies and accelerates large file exchanges and boosts productivity by streamlining submission, distribution, and file sharing.
If you are running FileCatalyst Workflow version 5.1.6 build 135 or earlier, you will need to download version 5.1.6 build 139 or newer, or follow the mitigation steps below, which disable the vulnerable servlets.
- Stop the Tomcat Service
- Navigate to the web.xml file located at:
<tomcat install dir>/webapps/workflow/WEB-INF/web.xml - Backup the web.xml file to a safe location before making changes
- Edit the file and comment out the
<servlet-mapping>blocks for:csv_servlet, pdf_servlet, xml_servlet, json_servlet - Save the changes and start your Tomcat Service
The vulnerability, listed as CVE-2024-5276, is an SQL injection vulnerability that allows an attacker to “modify application data”. This includes the ability to create an administrator account with a password of the attacker’s choosing.
According to Fortra, the vulnerability cannot be used for data exfiltration via SQL injection, and successful unauthenticated exploitation requires a Workflow system with anonymous access enabled, otherwise an authenticated user is required.
We advise administrators to apply the upgrade or the mitigation steps as soon as possible, since vulnerabilities in file transfer apps are of great interest to ransomware groups.
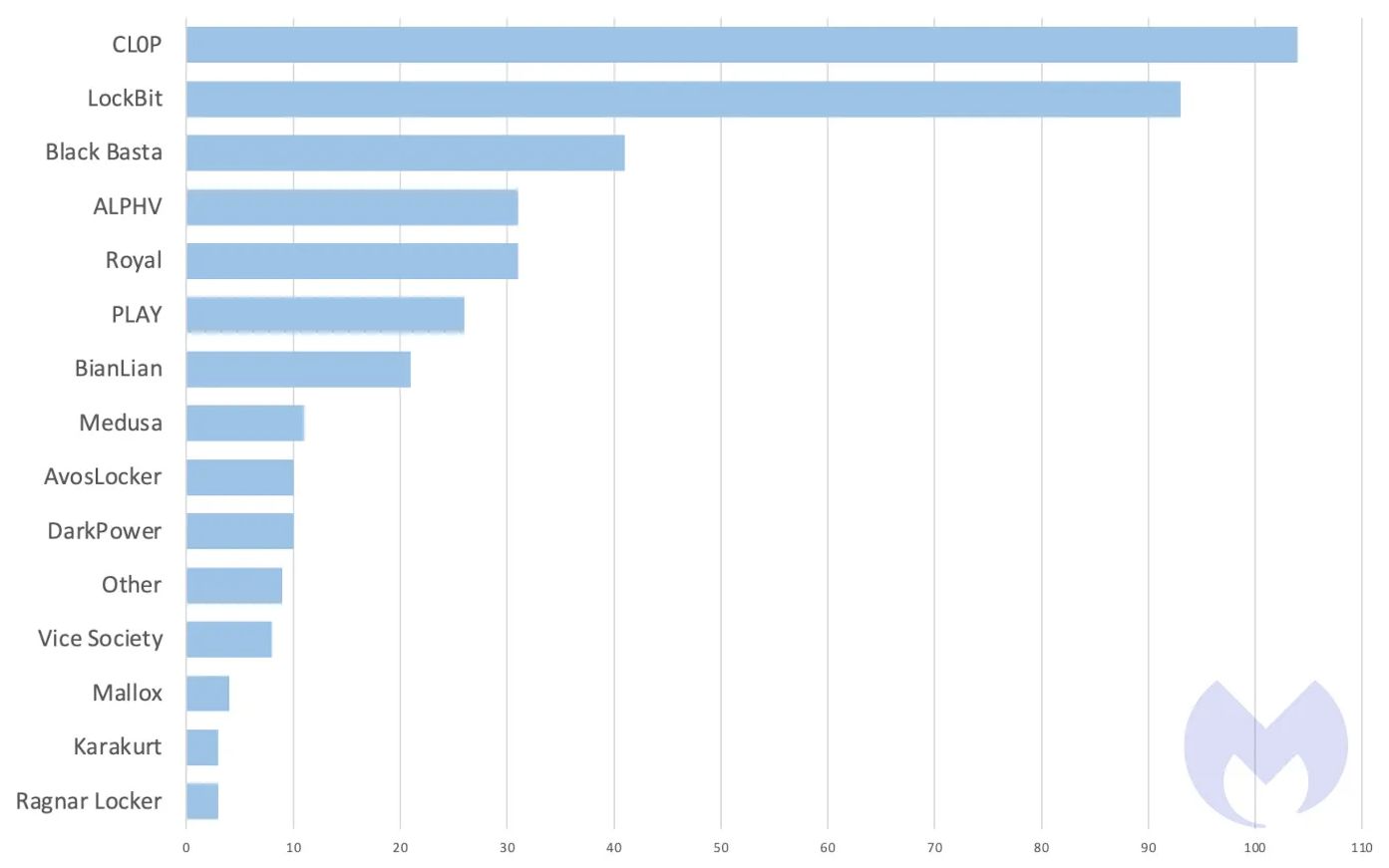
As we reported in our April 2023 ransomware review, last year the Cl0p ransomware group successfully breached over 104 organizations in one month by taking advantage of a zero-day vulnerability in Fortra’s GoAnywhere MFT file transfer software.
How to avoid ransomware
- Block common forms of entry. Create a plan for patching vulnerabilities in internet-facing systems quickly; and disable or harden remote access like RDP and VPNs.
- Prevent intrusions. Stop threats early before they can even infiltrate or infect your endpoints. Use endpoint security software that can prevent exploits and malware used to deliver ransomware.
- Detect intrusions. Make it harder for intruders to operate inside your organization by segmenting networks and assigning access rights prudently. Use EDR or MDR to detect unusual activity before an attack occurs.
- Stop malicious encryption. Deploy Endpoint Detection and Response software like ThreatDown EDR that uses multiple different detection techniques to identify ransomware, and ransomware rollback to restore damaged system files.
- Create offsite, offline backups. Keep backups offsite and offline, beyond the reach of attackers. Test them regularly to make sure you can restore essential business functions swiftly.
- Don’t get attacked twice. Once you’ve isolated the outbreak and stopped the first attack, you must remove every trace of the attackers, their malware, their tools, and their methods of entry, to avoid being attacked again.




